- Cisco Community
- Technology and Support
- Security
- Duo Security
- Managing Users
- Re: LDAPS With Self Signed Cert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
LDAPS With Self Signed Cert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 02:04 PM
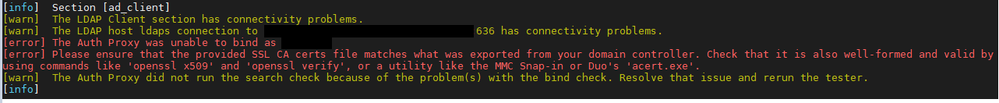
I have been banging my head against Google trying to get Duo Auth Proxy (Ubuntu) to work with LDAPS using a self signed cert. I have confirmed that LDAPS is working using the cert I created. Ldp.exe binds LDAPS (after I import the .cer into my Windows PC), a SaaS service is able to use LDAPS, and our Meraki AD integration picked it up. I have double and triple checked my DC to make sure I have the correct cert.
Duo works fine when I comment out the LDAPS strings in the ad_client section of my config file.
The cert was created in PowerShell, and the correct hostnames are being used. I put the .PFX in the personal computer store on the Domain Controller, and exported that same .PFX in .CER Base64, then converted that to .PEM using OpenSSL.
I am using a Duo free account if that makes any difference.
- Labels:
-
Directory Sync
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 03:08 PM
Since the cert is self-signed, it is its own CA, and has to be added to the “SSL CA certs file” as mentioned in your error message. (Or change the Auth Proxy’s config to point to a new file containing a copy of the cert.)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2022 03:35 PM
I am specifying the exported .PEM in the authproxy config. See below for the LDAPS parts in my config:
transport=ldaps
ssl_ca_certs_file=dc.pem exported pem in /conf
ssl_verify_hostname=true
I’ll look into the SSL CA certs file. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2022 06:38 AM
I created a new cert using OpenSSL on Linux and got everything working. I don’t know why it didn’t like the cert I created with PowerShell, possibly because it was a 6 year cert? The new one is only 1 year.
I generated the .KEY and .CRT, then converted the .KEY to .PFX. This was all done with OpenSSL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 07:52 AM
Did the first self-signed cert include “Certificate Signing” in its key usage? That is an extra requirement we have (mentioned in the description of the ad_client ssl_ca_certs_file parameter) when you use a self-signed cert. I don’t think New-SelfSignedCertificate includes that key usage by default.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 09:18 AM
That was most likely it. I can’t find any reference to “Certificate Signing” in the New-SelfSignedCertificate cmdlet. All I worried about were the correct hostname/alternative names, then exported the .PFX and .CRT files. The Org/OU/etc fields were all left blank unlike my OpenSSL cert. I also had to create the .PFX using the .KEY and .CER files that were created with OpenSSL.
Hopefully this helps someone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 09:34 AM
-keyusage certsign
Specifies the key usages set in the key usage extension of the certificate. The acceptable values for this parameter are:
CertSign
CRLSign
DataEncipherment
DecipherOnly
DigitalSignature
EncipherOnly
KeyAgreement
KeyEncipherment
None (default)
NonRepudiationDiscover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide