- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- D275: Duo Release Notes for Sep 29, 2023
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-04-2023 08:12 AM
Hello everyone! Here are the release notes for our most recent updates to Duo.
Public release notes are published on the Customer Community every other Friday, the day after the D-release is completely rolled out. You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
Check out the Guide to Duo End-of-Life and End-of-Support Plans. This guide provides an up-to-date list of current and past end-of-life plans for Duo products.
What's in this release?
- New features, enhancements, and other improvements
- Now in public preview: Duo Trust Monitor security event notifications
- Removal of passcodes from Duo Risk-Based Factor Selection methods
- Why has Duo removed passcodes as a RBFS step-up authentication method?
- Operating systems policy updated
- New Devices Policy timing options for warning and blocking users with out of date operating systems, browsers, and plugins
- Update to the Duo MSP Console
- New and updated applications
- Duo Authentication Proxy version 6.1.0 released
- Three new named SAML applications with Duo SSO and two SSO updates
- Duo Device Health application public beta versions 5.4.2 and 5.4.3 released
- Duo Mobile for Android version 4.50.0 released
- Duo Mobile for iOS version 4.50.0 released
- Bug fixes
New features, enhancements, and other improvements
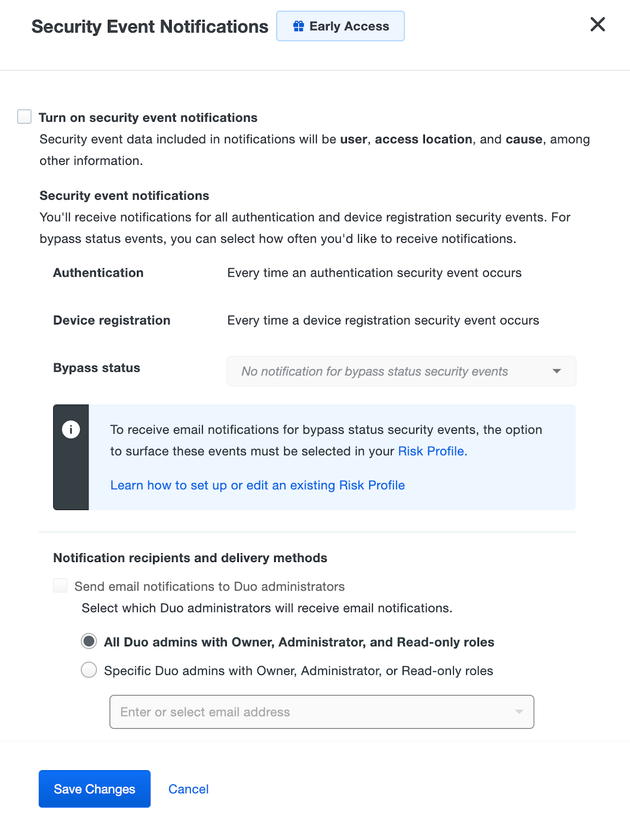
Now in public preview: Duo Trust Monitor security event notifications
- Duo administrators with the Duo Premier or Duo Advantage edition can now enable email notifications sent for each security event surfaced by Duo Trust Monitor.
- Configure Duo to send security event notifications either to all Duo admins, or only to specific Duo admins, with Owner, Administrator, and Read-only roles.
Removal of passcodes from Duo Risk-Based Factor Selection methods
- Duo’s Risk-Based Factor Selection (RBFS) policy will no longer allow passcodes via SMS, Duo Mobile, and hardware token as RBFS step-up authentication methods.
- The change will affect end-users logging into applications protected by RBFS policy. When RBFS detects a risk pattern and requires a step-up authentication from an end-user, the end-user will not be able to use passcode methods to complete the step-up authentication until the end-user completes MFA with a more secure method.
- Going forward, RBFS step-up authentication will offer the following methods:
WebAuthn FIDO2 security keys with biometric or PIN verification
Platform authenticators like Touch ID or Windows Hello
Bypass codes provided by a Duo administrator
- This change will not apply to the Auth API.
Why has Duo removed passcodes as a RBFS step-up authentication method?This change will improve Duo protection from passcode phishing. As our customers’ trusted advisor in secure access, we are committed to developing Risk-Based Authentication policies that provide the strongest protection possible in response to high-risk authentication patterns. We have learned from our research that passcodes no longer give our customers the protection they need from high-risk threats. By collaborating with customers on the research of threat actor capabilities, Duo has verified that attackers are increasingly targeting passcodes to gain access to protected applications. |
Operating systems policy updated
- iOS 17 and macOS 14 Sonoma are now available in operating systems policy.
- Duo operating systems policy will now recognize iOS 17 as the latest, and iOS 16 as up-to-date.
- On September 21, 2023, Apple released critical security updates to iOS 17 and iOS 16, but not iOS 15. Therefore, Duo will now recognize iOS 15 as end-of-life.
- Duo operating systems policy will now recognize macOS 14 Sonoma as the latest, and macOS 13 Ventura as up-to-date.
New Devices Policy timing options for warning and blocking users with out of date operating systems, browsers, and plugins
- Operating systems policy now lets you select 3 days or 7 days from the dropdown lists for When a version becomes out of date or end of life, encourage to update and When a version becomes out of date or end of life, encourage to block.
- Browsers policy: When you choose to Warn users if their browser is out of date, you may now select 3 days or 1 week from the dropdown list for And block them if it's more than [ ] out of date.
- Plugins policy: When you choose to Warn users when their Java plugin is out of date, you may now select 3 days or 1 week from the dropdown list for And block them if it's more than [ ] out of date.
- These policies are available in Duo Advantage and Duo Premier.
Update to the Duo MSP Console
- All Duo Managed Service Providers (MSPs) can now manage subaccounts on different Duo deployments
- Read this article to learn more about how to identify your Duo deployment.
- As noted in the Release Notes for D273, this means MSPs will not have access to the public preview of the redesigned header and navigation in the Duo Admin Panel.
New and updated applications
Duo Authentication Proxy version 6.1.0 released
- Restores the default for allow_concat to false in the radius_server_eap section.
- Fixes various bugs in radius_server_eap functionality.
- No longer logs configured server sections twice at startup.
- Authentication Proxy upgrades no longer fail when there is a subdirectory inside the conf directory.
- The Windows service now correctly installs/uninstalls when there is an invalid authproxy.cfg (ZTAT-27)
- Provides a utility script to assist with converting radius_server_iframe sections to radius_server_auto. See Guide to Duo's iFrame Reconfiguration Script.
- Updates Cryptography to 41.0.3.
- Updates OpenSSL to 3.1.2.
Three new named SAML applications with Duo SSO and two SSO updates
- There are now named SAML applications to protect Zoho, Zoho One, and NinjaOne with Duo SSO, our cloud identity provider.
- Reminder: Duo Access Gateway will reach end of life October 16 through 26, 2023. Please see the Guide to Duo Access Gateway end of life for more details.
Duo Device Health application public beta versions 5.4.2 and 5.4.3 released
- macOS beta version 5.4.2.0
- Minor improvements and enhancements.
- macOS beta version 5.4.3.0
- Duo Device Health is now Duo Desktop. Upgrading to this version of the app automatically removes Duo Device Health.
- Windows beta version 5.4.2
- Minor improvements and enhancements.
- Windows beta version 5.4.3
- Duo Device Health is now Duo Desktop. Upgrading to this version of the app automatically removes Duo Device Health.
Duo Mobile for Android version 4.50.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
Duo Mobile for iOS version 4.50.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
Bug fixes
- Fixed a bug that prevented selection of Duo Mobile one-time passcodes when Duo administrator enrollment only allowed security keys or Duo Mobile one-time passcodes as verification methods. Previously, security key registration could not be skipped in favor of Duo Mobile one-time passcodes.
- Fixed a bug that repeated the Log in prompt when end-users logged in using Duo Single Sign-On or Duo Passwordless.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
