- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Site to Site vpn not establishing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Site to Site vpn not establishing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2024 03:01 AM
I am trying to configure Site to site vpn in lab, same parameters have been configured on both Routers but for some reason it is not working. sh crypto isakmp sa output there is nothing.
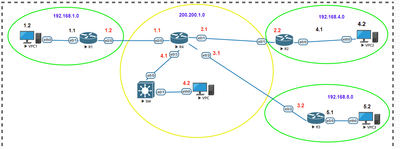
I am attaching the topology, I am trying to make tunnel between R1 & R2, and testing by pinging PCs behind R1 and R2 but request is timing out.
R1#sh run
Building configuration...
Current configuration : 1609 bytes
!
! Last configuration change at 12:49:20 EET Sun Jan 28 2024
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
bsd-client server url https://cloudsso.cisco.com/as/token.oauth2
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
!
!
!
!!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
cts logging verbose
!
!
!
redundancy
!
!
!
!
!
!
!
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key key123 address 200.200.2.2
!
!
crypto ipsec transform-set TS1 esp-3des esp-sha-hmac
mode tunnel
!
!
!
crypto map MAP1 1 ipsec-isakmp
set peer 200.200.2.2
set transform-set TS1
match address list1
!
!
!
!
!
interface Ethernet0/0
ip address 200.200.1.2 255.255.255.0
crypto map MAP1
!
interface Ethernet0/1
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 192.168.4.0 255.255.255.0 200.200.2.2
ip route 200.200.2.0 255.255.255.0 200.200.1.1
ip route 200.200.3.0 255.255.255.0 200.200.1.1
ip route 200.200.4.0 255.255.255.0 200.200.1.1
!
ip access-list extended list1
permit ip 192.168.1.0 0.0.0.255 192.168.4.0 0.0.0.255
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
login
transport input none
!
!
end
=======================
R2#sh run
Building configuration...
Current configuration : 1609 bytes
!
! Last configuration change at 12:56:40 EET Sun Jan 28 2024
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
!
!
!
bsd-client server url https://cloudsso.cisco.com/as/token.oauth2
clock timezone EET 2 0
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
cts logging verbose
!
!
!
redundancy
!
!
!
!
!
!
!
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
crypto isakmp key key123 address 200.200.1.2
!
!
crypto ipsec transform-set TS1 esp-3des esp-sha-hmac
mode tunnel
!
!
!
crypto map MAP1 1 ipsec-isakmp
set peer 200.200.1.2
set transform-set TS1
match address list1
!
!
!
!
!
interface Ethernet0/0
ip address 192.168.4.1 255.255.255.0
!
interface Ethernet0/1
ip address 200.200.2.2 255.255.255.0
crypto map MAP1
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
ip route 192.168.1.0 255.255.255.0 200.200.1.2
ip route 200.200.1.0 255.255.255.0 200.200.2.1
ip route 200.200.3.0 255.255.255.0 200.200.2.1
ip route 200.200.4.0 255.255.255.0 200.200.2.1
!
ip access-list extended list1
permit ip 192.168.4.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
line con 0
logging synchronous
line aux 0
line vty 0 4
login
transport input none
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2024 03:06 AM
@asfandyar779514494 try adding default route in routers.
Good luck
KB
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2024 03:09 AM
As @Kasun Bandara mentioned
You need defualt route or static route for remote lan in each router
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2024 03:11 AM
Which device do you use to ping the other side's PC? If you use the router, you have to use the LAN interface as the source. Or even better, ping from the PC. If you ping from the router without any source, the traffic will not match the crypto ACL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2024 10:28 AM - edited 01-28-2024 10:33 AM
What does the output of show crypto isakmp sa detail and show crypto ipsec sa show you?
Also run some debugs on both routers while you try to establish a connection and analyze the output and / or paste the output here.
debug crypto isakmp
debug crypto ipsec
Also, your static routes for the remote networks are incorrect on both routers.
R1 has ip route 192.168.4.0 255.255.255.0 200.200.2.2, but the next hop should be 200.200.1.1, And R2 has ip route 192.168.1.0 255.255.255.0 200.200.1.2, but the next hop should be 200.200.2.1.
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide