- Cisco Community
- Technology and Support
- Small Business Support Community
- Switches - Small Business
- Re: SG350XG SSL Certificate SAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SG350XG SSL Certificate SAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2022 08:52 AM
Hello,
I have a couple of old SG350XG switches, and I am trying to generate a CSR and create a new custom SSL certificate.
After applying the generated certs, Chrom/Edge etc still does not trust the cert because there is no SAN. The CSR gives me no option to enter a SAN.
Is there any other way for me to generate a cert for these switches that conforms to modern SSL cert standards?
Thanks
James
- Labels:
-
Small Business Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-04-2022 11:05 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-05-2022 07:51 AM
Hi,
Thanks, but I'm not sure this answers my query?
As there is no box to enter a SAN on the CSR, I cannot add a SAN. This means even after successfully requesting and importing the cert, it still isn't trusted by my browser.
Perhaps what you are saying, is that Firefox does not generate errors on certs that do not have SANs, and that my workaround to not being able to specify one, is to use Firefox as my browser?
Cheers
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2022 02:58 AM - edited 07-06-2022 03:05 AM
you have to perform this by CLI
Verify your certificate and private key
Generate the public key from the private key
Import certificate and keys to the switch
use the below command to import a custom certificate
#crypto certificate 1 import ( past you input certificate and certificate )
switch can have up to 2 certificate
GUI
Security > SSL Server > SSL Server Authentication Setting --can Import/create certificate
Jitendra
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2022 08:45 AM
Hi,
Even via the CLI, the crypto commands do not allow me to specify a SAN:
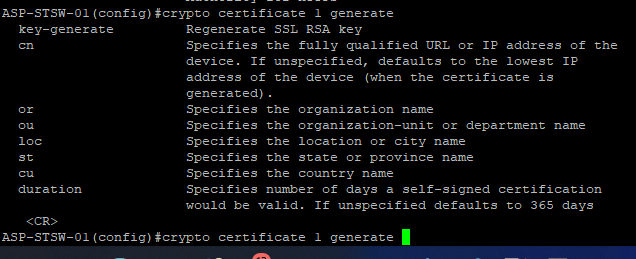
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-06-2022 09:32 PM
check the below article if its help for you.
Jitendra
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2022 02:16 AM
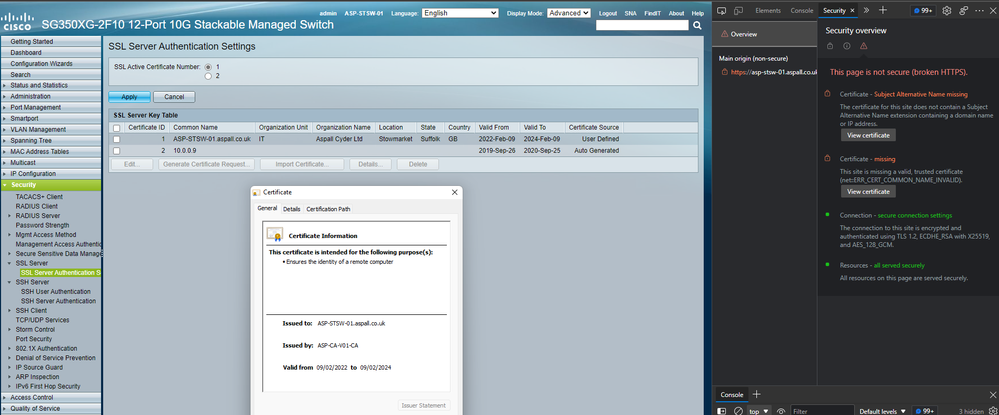
Sorry, no it doesn't.
I don't have any issues generating and importing a certificate via the GUI, the issue is the browser does not like the certificate that it generates.
Please refer to previous screenshot, whereby the browser says it does not trust the cert as "Subject alternate name is missing".
I specifically need to know, how can I generate a CSR for this switch that includes a Subject Alternate Name.
Thanks
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2022 08:34 AM
Is it perhaps possible to just generate a CSR using OpenSSL with a SAN on it, then import the cert into the switch, or do I need to be worrying about private keys?
Cheers
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 03:54 AM
Hi,
I have managed, with some support from Cisco support team, to import some certs and keys into my Catalyst 9200 series switches.
I'm still struggling with these though.
I have used OpenSSL to generate a CSR and new private key, which I used to issue a new cert from our AD CA.
When going to import a cert on these switches, I can enter the certificate detail, the public key (extracted from the private key) as well as the private key.
I am told though, that the key is "missing headers".
I tried adding the DEK headers to my private key (that were required when importing to my 9200s), but it gave me the same error.
Can anyone guide me on what the correct format for each of the keys is, so I can modify what I have and have another go at importing?
Many thanks
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 04:06 AM
hi James,
to get it working seamlessly you need to have key and certificate in .pem format.
private_rsa_key.pem
public_rsa_key.pem
cert.pem
what format do you have?
Alex
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-21-2022 05:08 AM
I believe it is PEM, as the format within the keys and cert are:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIFHD.....
-----END ENCRYPTED PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIFmz...
-----END CERTIFICATE-----
I used the below openssl command to generate the key and CSR:
.\openssl.exe req -newkey rsa:2048 -subj "/C=/ST=/L=/O=/OU=/CN=" -sha256 -keyout key.key -out csr.csr -config .\openssl_san.cnf
The CSR was then submitted to our internal AD CA, and a base64 encoded (rather than DER) was downloaded.
Many thanks
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2022 01:59 AM
Any additional guidance for me on this please?
Many thanks
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-30-2023 02:43 PM
You have to decrypt your private key with openssl.
Use command: openssl.exe rsa -in device_private.key -out device_private_decrypt.key
enter password used to create csr, and result file wil have header with BEGIN RSA PRIVATE KEY as reqiored by switch
Regards,
Marcin
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide