- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- How To: Agentless Posture Configuration, validation & Troubleshooting
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-15-2020 05:08 AM - edited 10-15-2020 10:02 AM
- Introduction
- Components
- Supported Endpoints
- Prerequisites
- Windows 10 Endpoint Configuration
- GPO configuration for Managed Windows to allow PowerShell Remoting and Firewall Exceptions
- Cisco ISE Configuration
- Validating the configuration with flow
- Solutions when Agentless Posture fails
- Verifying endpoint flow if Agentless Posture flow fails
- Issues & Troubleshooting
Introduction
Cisco Identity Services Engine (ISE) gives you intelligent Integrated protection through intent-based policy and compliance solution. Cisco ISE supports posturing of endpoints with different Anyconnect deployment methods so far. With increase in market demand and need for Agentless posture functionality, Cisco ISE 3.0 onwards supports Agentless posture functionality. With this functionality, there is no user-intervention required to download Anyconnect agent and install on the system. While Agent and Agentless gives different flexibility/control, this document describes configuration required for Agentless posture functionality from scratch, required configuration on windows 10 Endpoints and validate the Agentless posture functionality with a roundtrip.
Components
Cisco Identity Services Engine 3.0
Windows 10 Client
Access Switch
Wireless Lan Controller
Supported Endpoints
Cisco Identity Services Engine Release 3.0 supports windows 10 and macOS endpoints.
Prerequisites
Cisco Identity Services Engine is able to assess posture using Agentless functionality by connecting to the connected endpoints. Below are the requirements for successful Agentless posture functionality on windows and macOS Endpoints.
- The client must be reachable by its IP address, and that IP address must be available in RADIUS accounting.
- Windows and Mac clients are currently supported.
- For Windows clients, port 5985 to access Powershell on the client must be open. Powershell must be version 5.1 or above.
- For Mac OSX clients, port 22 to access SSH must be open to access the client. The client must have curl version 7.34 or above.
- Client credentials for shell login must have local admin privileges.
- Run the posture feed update to get the latest clients, as described in the configuration steps.
- Ensure that the following entry is updated in the sudoers file to avoid certificate installation failure on the endpoints:<macadminusername> ALL = (ALL) NOPASSWD: /usr/bin/security, /usr/bin/osascript
- For Mac OSX, the user account configured must be an administrator's account. To view this window, click the Menu icon (
)and choose Administration > System > Settings > Endpoint Scripts > Login Configuration > MAC Local User. Agentless posture for Mac OSX won’t work with any other account type, even if you grant more privileges.
Windows 10 Endpoint Configuration
As per criteria above, PowerShell Remoting has to be enabled and we will have to ensure local firewall is allowing incoming PowerShell port over TCP. We will see how to achieve it.
Enabling PowerShell Remoting Locally on endpoint:
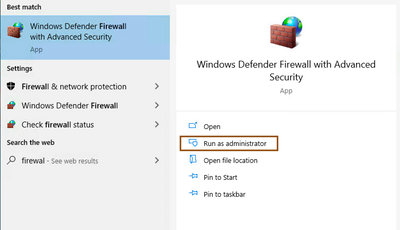
- Allow PowerShell port (5985) incoming connections. For this, open Windows Defender Firewall with advanced Security app with administrative privileges.
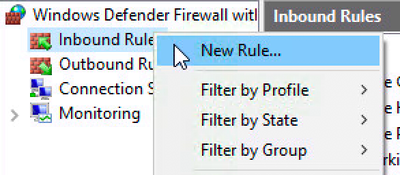
- Select Inbound Rules, and click on New Rule
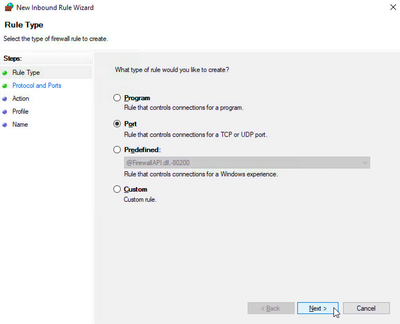
- Select Port under Rule Type.
- Select TCP as apply to and provide Specific local ports with port number 5985.
NOTE: By default 5985 is the port Microsoft uses for PowerShell remoting purpose. You can customize to new port on both Cisco ISE and Windows endpoints. Please refer to Microsoft documentation on configuring different port for PowerShell Remoting. In Cisco ISE, you can modify default port number from Administration > System > Settings > Endpoint Scripts > Settings menu.
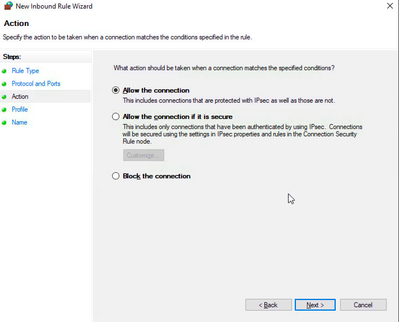
- Select Allow the Connection under Action.
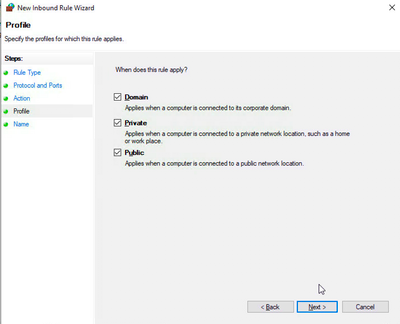
- Select appropriate profile such as domain/private/public
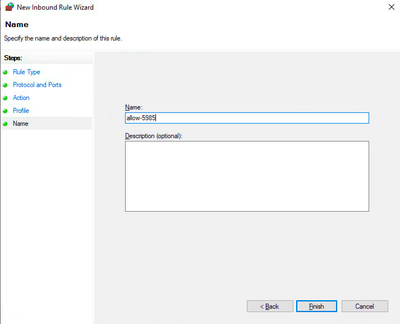
- Provide meaningful name and then submit.
- Ensure that TCP port 5985 is allowed
- On windows endpoint, open PowerShell prompt with administrator privileges
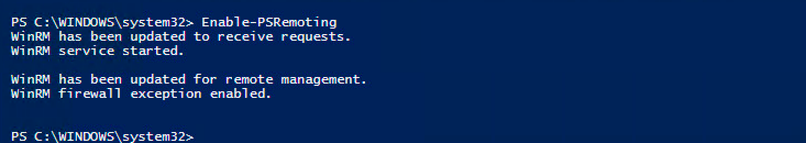
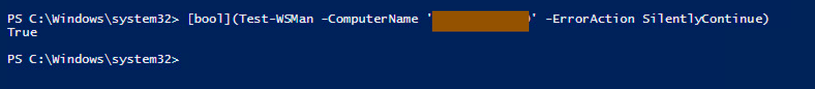
- If PowerShell Remoting isn’t enabled, then You can enable it using command “Enable-PSRemoting”. You can also use “-Force” as parameter.
- Optionally, you can restart WinRM service with command “Restart-Service WinRM” and/or “Restart-Service winmgmt”
- Test whether PowerShell Remoting is enabled or not. [bool](Test-WSMan -ComputerName 'ComputerName' -ErrorAction SilentlyContinue)
- Optionally, add a host to <trust zone> which needs to connect remotely, you can type the following cmdlet in PowerShell (again, you’ll need to run it as Administrator) : "Set-Item wsman:\localhost\client\TrustedHosts -Value server_name -Force" (where server_name is Cisco ISE). This will allow only Cisco ISE can talk to the client’s via PowerShell remoting.
NOTE: You can also achieve this from GPO. Refer to Microsoft documentation to allow PowerShell Remoting and setting firewall to allow incoming connection from GPO.
GPO configuration for Managed Windows to allow PowerShell Remoting and Firewall Exceptions
Below GPO configuration would allow you to configure PowerShell Remoting and firewall exceptions on managed Windows endpoints. GPO is a powerful tool for the managing Windows endpoints in an organization. Organization Units (OUs) would be flexible to limit the scope of GPO policies rather than applying on entire organization.
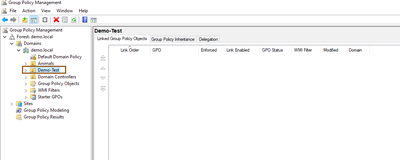
- I have configured OU called Demo-Test for this purpose. Open Group Policy Management Console and select the OU Demo-Test.
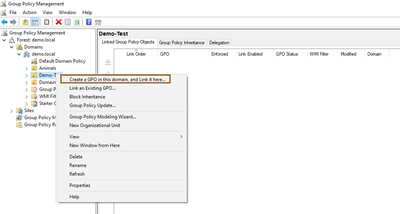
- Right click and select Create a GPO in this domain, and Link it here…
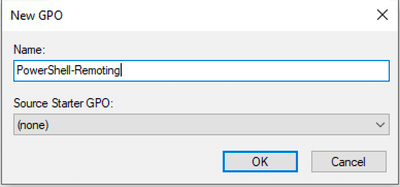
- Provide name of the GPO policy such as PowerShell-Remoting
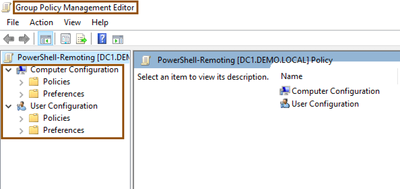
- Edit newly created GPO policy
- Group Policy Management Editor Opens.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > System services and select and edit Wired Autoconfig service. Check the Define this policy settings and select Automatic radio button. Click the OK once configuration is finished.
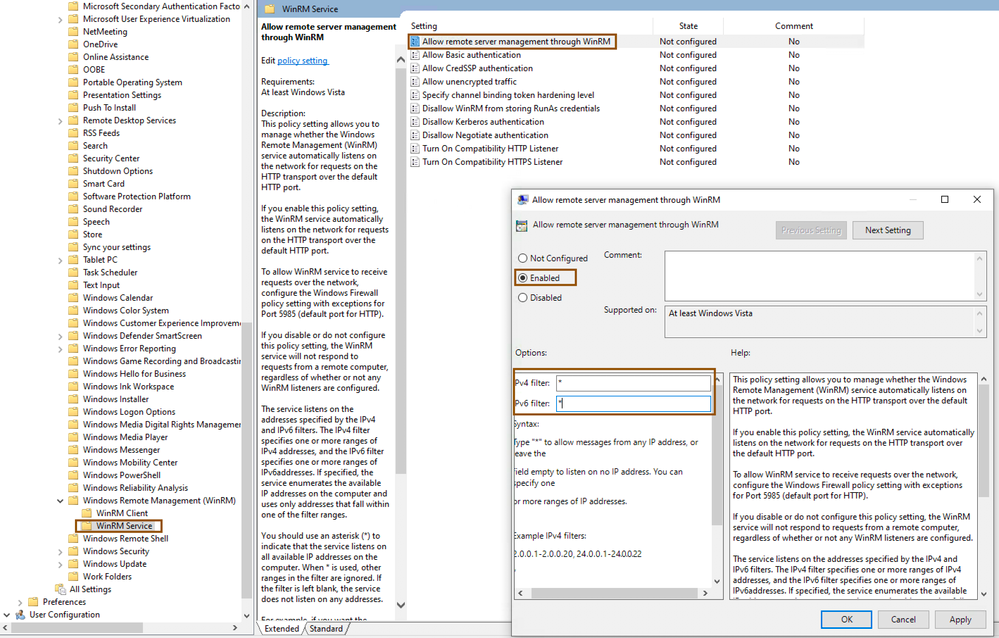
- Navigate to Computer Configuration > Policies > Administrative Templates: Policy definitions > Windows Remote Management (WinRM) > WinRM Service, select and edit Allow remote server management through WinRM, and enable the service by providing IPv4, IPv6 filters as * to allow listen on any IPv4 and IPv6 addresses. Click the OK once the configuration is finished.
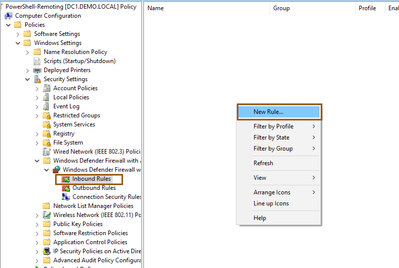
- Navigate to Computer Configuration > Policies > Windows Defender Firewall with Advanced Security > Windows Defender Firewall with Advanced Security > Inbound Rules, create a rule by right click and select New Rule..
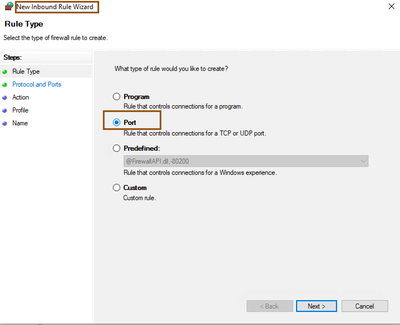
- Select Port from New Inbound Rule Wizard and Click Next.
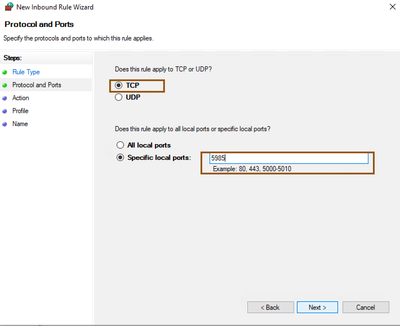
- Make sure to select TCP under the Does this rule apply to TCP or UDP?, Select Specific local Ports from the Does this rule apply to all local ports or specific local ports? and provide the 5985 (default port for PowerShell) then click Next.
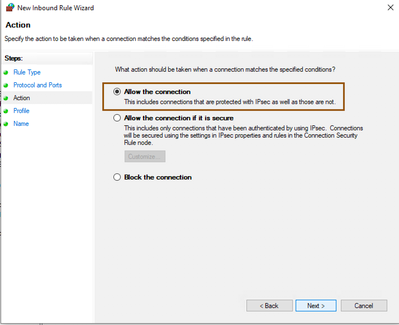
- Select the Allow the Connection from wizard action step and click Next.
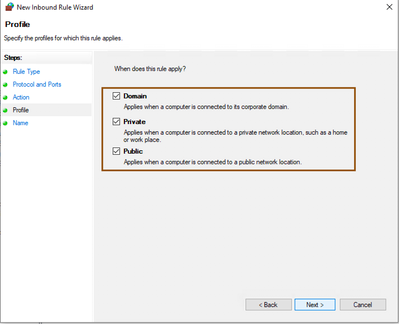
- Select your endpoints profile ..
- Provide some meaningful name to exception rule and click Finish.
Above GPO configuration is going to be helpful in enabling PowerShell remoting on your windows machine and allow incoming PowerShell connection from ISE on your managed Windows endpoints.
Note: You can also setup 802.1X and Wired/Wireless Network Profiles on your managed Windows endpoints from GPO. Refer to Microsoft documentation.
Cisco ISE Configuration
For demo purpose, Standalone Cisco ISE is being used here. It has default configuration. In order to achieve Agentless Posture functionality without agent installation on endpoint, Cisco ISE requires to communicate to endpoints as described in Prerequisites section above.
- Login to the ISE UI using the admin credentials that were created during setup.
- Ensure you have appropriate license (Refer to Licensing ordering guide and documentation of Cisco ISE)
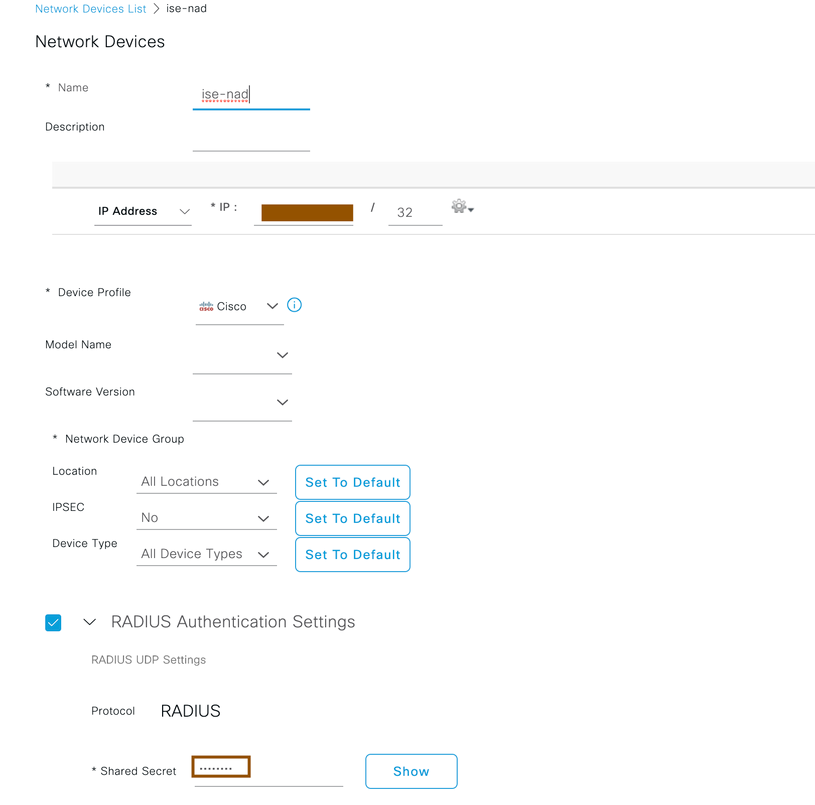
- A network device has to be configured initially to honor the radius requests from network access devices such as WLCs, Access-Switches... Navigate to Administration > Network Resources> Network Devices and configure NAD with shared secret. Provide Name of the NAD in Cisco ISE for reference purpose, provide IP address and shared secret (shared secret should be same in NAD too) then submit the configuration.
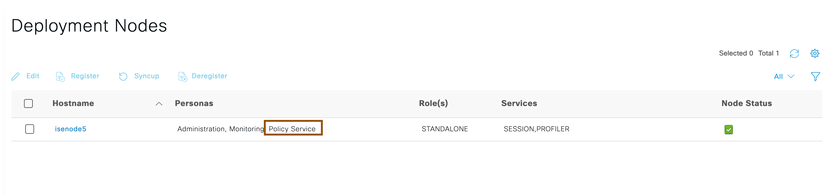
- Ensure Cisco ISE is in standalone mode and Policy service is enabled by navigating to Administration > System > Deployment.
- Ensure you have appropriate licenses enabled in Cisco ISE.
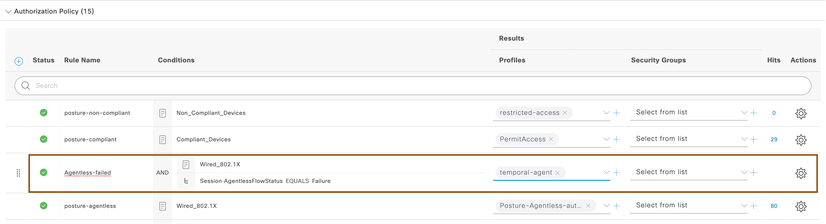
- Create an authorization profile for endpoints which requires Agentless posture flow by navigating to Policy > Policy elements > Results > Authorization > Authorization Profile and click on Add. Ensure to select Agentless Posture flag along with vlan, ACLs, DACLs that you wanted to enforce on the session.
NOTE:
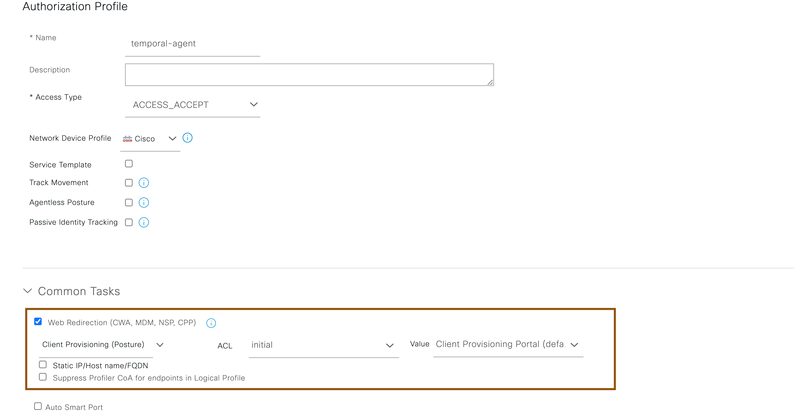
- No need to configure web-redirection as client interaction isn’t necessary for Agentless posture functionality.
- Ensure ACLs/DACLs being enforced allows PowerShell remoting port to windows endpoints and SSH port to macOS.
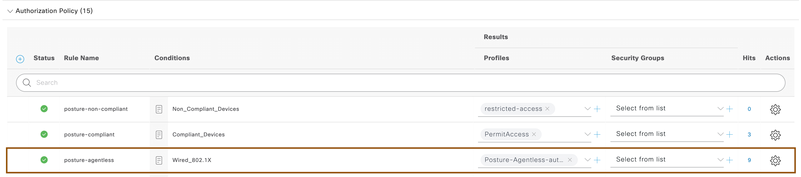
- Configure Authorization Policies under standard authorization policies by navigating to policy > policy sets, select Default policy set. For endpoints authenticating over dot1x, associate above authorization profile created above.
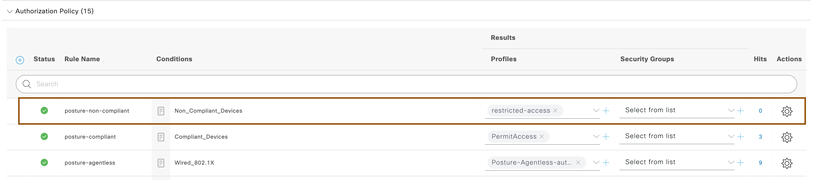
- Configure one more authorization policy on top of above rule for compliant devices to give access privilege.
- Configure one more authorization policy for non-compliant devices to give restricted privileges.
NOTE: In above snapshot, restricted-access authorization profile was given where endpoints has restricted privileges.
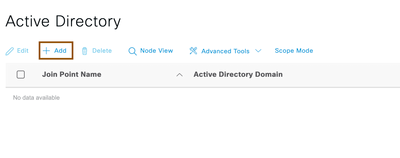
- Configure Active Directory by navigating to Administration > Identity Management > External Identity Sources > Active Directory and click on Add
- Provide Name of the Active Directory and domain name, Cisco ISE will prompt you to configure AD credentials so that Cisco ISE could join to AD. Once AD credentials provided, ensure the Cisco ISE is joined to Active Directory successfully.
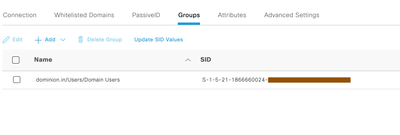
- (Optional)Click on Groups tab of Active Directory and retrieve required groups which requires Agentless posture functionality. In below snapshot, we configured Domain users for demonstration purpose. Once required groups retrieved from AD in Cisco ISE, save the configuration.
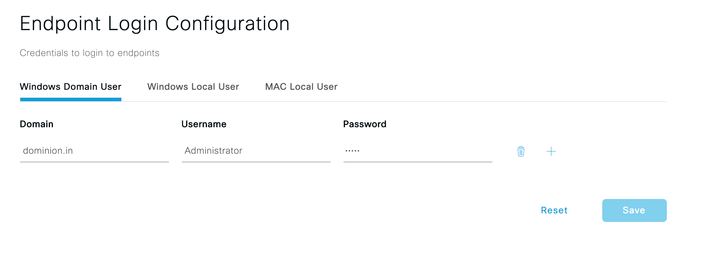
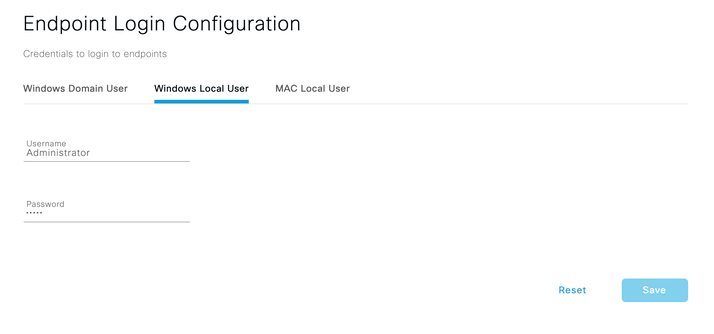
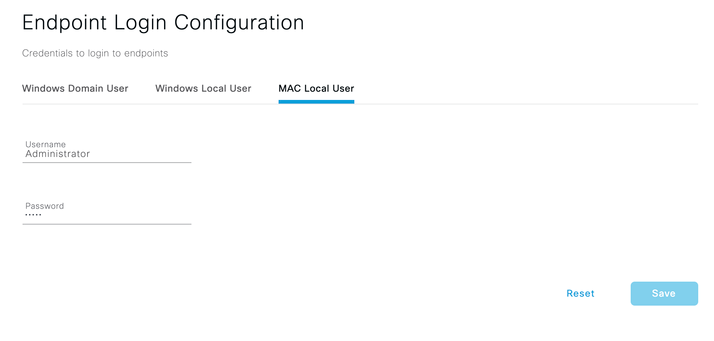
- Cisco ISE requires Endpoint Login Configuration for successful Agentless posture. Navigate to Administration > System > Settings > Endpoint scripts > Login configuration and configure credentials for Windows and macOS endpoints. Cisco ISE uses
- Windows Domain User -- If you are managing windows endpoints which are going through Agentless posture flow via Active Directory domain, provide domain name and credentials which has local administrative privileges.
- Windows Local User – If you are not managing windows endpoints which are going through Agentless posture flow via Active Directory domain, provide credentials which has local administrative privileges. You have to ensure credentials configured are common for all windows operating systems going through Agentless posture.
- Mac Local User – Provide credentials for macOS endpoints. You have to ensure credentials configured are common for all macOS endpoints going through Agentless posture.
Validating the configuration with flow
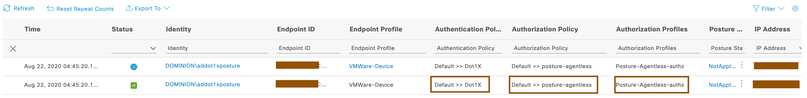
- Authenticate against Cisco ISE using the domain credentials on the endpoint. Ensure that endpoint is matching with authorization policy posture-Agentless written for newly connected endpoints.
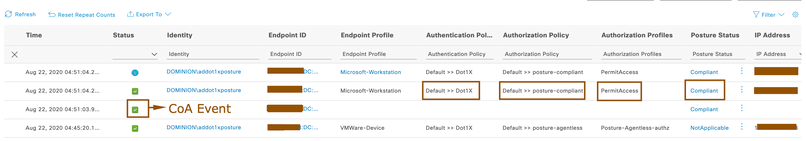
- After couple of seconds, Agentless posture would be successful and Cisco ISE issues CoA to give endpoint required privileges as per the configuration.
NOTE: Endpoint gets compliant access as you haven’t configured any posture policies in above demonstration. You can configure posture policies as per your organizational needs.
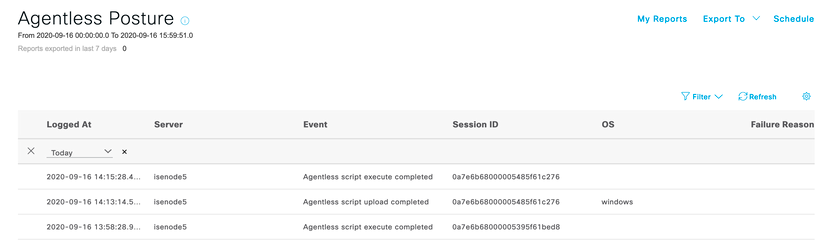
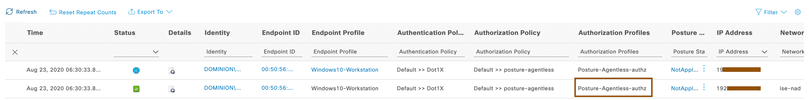
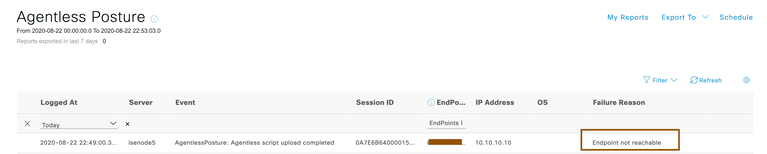
- You will be able to understand whether Agentless posture is successful or not by going to Operations > Reports > Endpoints and Users > Agentless Posture report. You will also get to know failure reason if Agentless posture is failing.
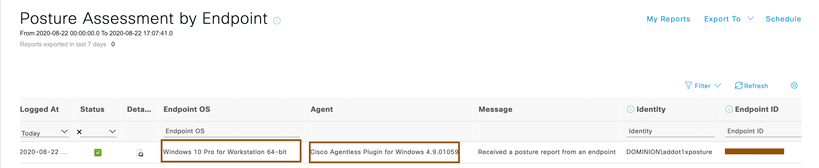
- You can view the posture report received from the endpoint by running report Operations > Reports > Endpoints and Users > Posture Assessment by Endpoint. Notice that Agent version can also be seen in this report allowing you to run Agentless and agent posture in same Cisco ISE deployment using NAD/Location/Groups..etc as a conditions.
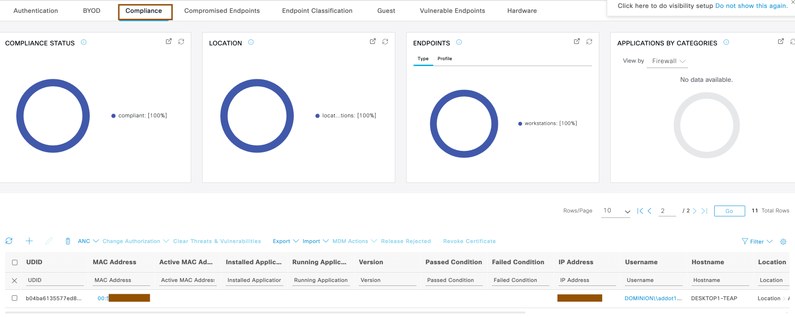
- You can also view context visibility for compliance endpoints in your organization by navigating to Context visibility > Endpoints > Compliance
Solutions when Agentless Posture fails
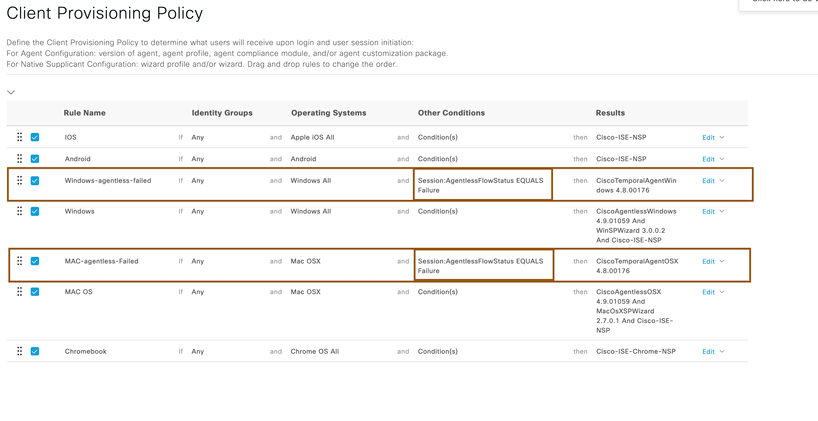
For successful Agentless posture flow, prerequisites mentioned above should be met. Agentless posture flow might fail because of reasons such as endpoint login credentials or privileges issue configured on Cisco ISE, port might not be reachable, client IP might not be reachable…etc. so, if that happens, in order to come out of Agentless posture initial state itself, Cisco ISE gives you flexibility to configure different policies when Agentless posture flow is broken with condition called Session:AgentlessFlowStatus. Below section describes about taking endpoint to different flow such as redirecting him to client provisioning page where client can download temporal agent to do posture assessment instead of stuck in Agentless posture flow itself.
- Configure a client provisioning policy for windows or macOS to give Anyconnect temporal agent when Agentless posture flow is failed. Navigate to Policy > client provisioning and create client provisioning policies for windows and macOS operating systems to provision temporal agent.
- Configure authorization profile for clients to be redirected to client provisioning page to provision temporal agent by navigating Policy > Policy Elements > Results > Authorization > Authorization Profile
- Configure an authorization policy for Agentless posture failed endpoints to be redirected to posture page for provisioning temporal agent.
Verifying endpoint flow if Agentless Posture flow fails
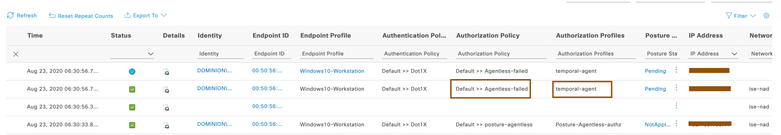
- Authenticate the client over dot1x and ensure it is initially matching with Agentless posture authorization profile.
- Once Agentless Posture is failed on the endpoint, Cisco ISE issues CoA to evaluate authorization policies again and it matches with new authorization policy written above.
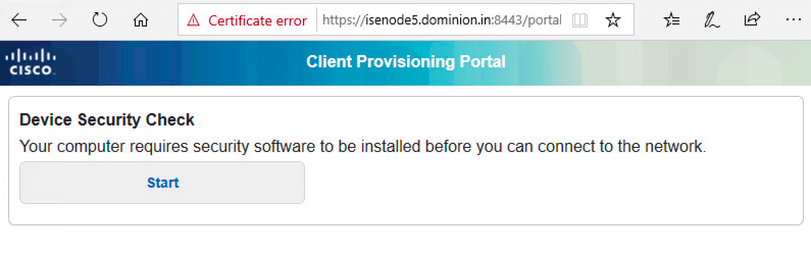
- Try to bring up browser on endpoint and it should get redirected to Posture page to provision temporal agent.
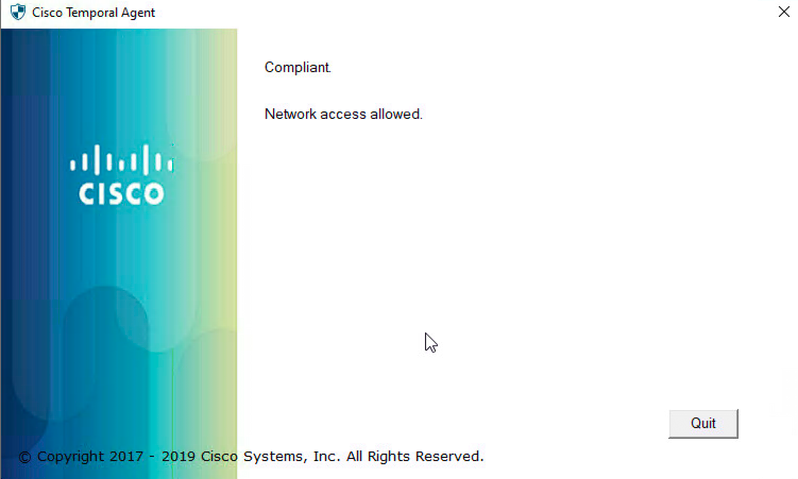
- Download Cisco Temporal agent and run it.
- Cisco Temporal agent evaluates posture policies and submits report back to Cisco ISE.
- Cisco Cisco ISE gives access to clients as per the compliance or non-compliance of an endpoint.
Issues & Troubleshooting
Below are the ways that are available for you to troubleshoot Agentless posture failures in your deployment.
- Agentless Posture Troubleshooting Tool
- Troubleshooting from downloaded logs or debug logs from CLI
- Upload scripts against the endpoints to find the root cause.
Agentless Posture Troubleshooting Tool:
If the endpoint connected is failing for Agentless posture flow, Cisco Identity Services Engine provides inhouse tool for troubleshooting purpose. There are two methods to do this.
Method1: From live logs, find the endpoint live log for which Agentless posture is failing(filter based on MAC address/Userid..etc fields). From Posture Status column of that endpoint live log entry, by clicking onadjacent to PostureStatus, it will automatically take you to Operations > Troubleshoot > Diagnostic Tools > Agentless Posture Troubleshooting section populated with endpoint MAC address.
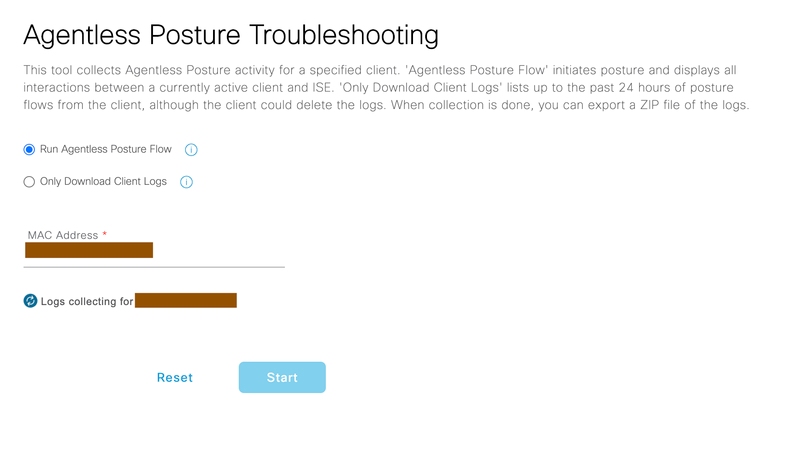
Method2: Second method is to manually navigate to Operations > Troubleshoot > Diagnostic Tools > Agentless Posture Troubleshooting, provide the MAC address of endpoint for which Agentless posture flow is failin
NOTE: MAC address provided here should be connected to the system in order to troubleshoot the endpoint where Agentless posture flow is failing
By either of the method mentioned above, you will have to options gather Agentless posture logs from the system.
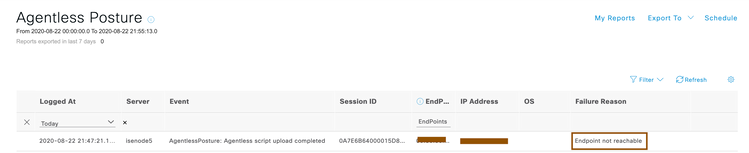
Run Agentless Posture Flow – By selecting this option and providing the MAC address where Agentless posture is failing, Cisco Identity services Engine automatically runs the Agentless posture flow on the endpoint and allows you to download all interaction happened between Cisco Identity Services Engine and Client in zip file.
Only Download Client Logs – By selecting this option and providing the MAC address where Agentless posture is failing, Cisco Identity Services Engine lets you to download all previous interactions happened between Cisco Identity Services Engine and client in zip file.
Click on Export, to download the logs in zip file to your local computer for troubleshooting purposes.
Troubleshooting from downloaded logs or debugging logs from CLI
Case1: If endpoint’s firewall isn’t allowing incoming connections to PowerShell port or PowerShell port isn’t allowed in ACLs/DACLs
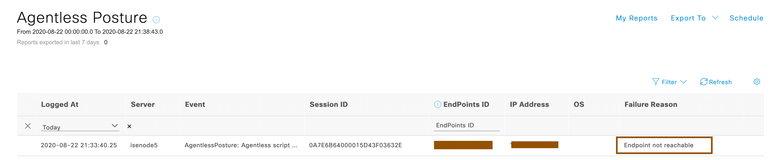
When the Cisco ISE is not able to connect to the endpoints to PowerShell port, below log snippets are going to give you an idea why is it failing. You can rectify this problem by allowing PowerShell port so that Agentless Posture is going to be successful.
You can take a look at the logs (ise-psc.log) downloaded from Agentless Posture Troubleshooting page or if you want to debug the issue in a live environment, From the Cisco ISE PSN CLI, execute command show logging application ise-psc.log to identify the root cause.
---------------------------
2020-08-22 21:30:38,071 INFO [pool-235-thread-96][] cpm.es.service.posture.ESGenericConsumer -::::- Received endpont: 192.168.105.100 from queue: POSTURE-INPUT
----------------------------------------------
2020-08-22 21:33:40,242 INFO [pool-235-thread-97][] cisco.cpm.posture.runtime.AgentlessPostureErrorHandler -::::- Handle error for sessionId=0A7E6B64000015D43F03632E, AgentlessFlowStatus=Failure
----------------------------------------------
2020-08-22 21:33:40,242 INFO [pool-235-thread-97][] cisco.cpm.posture.runtime.AgentlessPostureErrorHandler -::::- Calling triggerPostureCoA for sessionId=0A7E6B64000015D43F03632E
----------------------------------------------
2020-08-22 21:33:40,249 DEBUG [pool-235-thread-97][] cisco.cpm.posture.events.PostureMessagesConsumer -::::- Sending auditLog for sessionId=0A7E6B64000015D43F03632E with attributes: [Posture.MacAddress, 00-50-56-01-02-03, Posture.IpAddress, 192.168.105.100, Posture.OperatingSystem, null, Posture.FailureReason, Endpoint not reachable, Posture.SessionId, 0A7E6B64000015D43F03632E]
2020-08-22 21:33:42,247 DEBUG [Posture-CoA][] cisco.cpm.posture.runtime.PostureCoA -::::- Posture CoA is triggered for endpoint [00-50-56-01-02-03] with session [0A7E6B64000015D43F03632E]
Case2: If credentials are wrong or credentials provided doesn’t have administrative privileges on the endpoint.
When the Cisco ISE is not able to connect to the endpoints because of administrative privileges missing to run the Agentless Posture flow, below log snippets are going to give you an idea why is it failing. You can rectify this problem by providing proper login credentials again so that Agentless Posture is going to be successful.
You can take a look at the logs (ise-psc.log) downloaded from Agentless Posture Troubleshooting page or if you want to debug the issue in a live environment, From the Cisco ISE PSN CLI, execute command show logging application ise-psc.log to identify the root cause.
----------------------------------------------
2020-08-22 21:44:18,033 DEBUG [PrRTEvents-Executor-2][] cisco.cpm.posture.events.NetAccessEventHandler -::::- Published message to POSTURE-INPUT for Agentless session 0A7E6B64000015D83F0FEA54
----------------------------------------------
2020-08-22 21:47:20,163 INFO [pool-3627-thread-5][] cpm.es.service.posture.ESDiscoveryTask -::::- Publishing result for: 192.168.105.100. Task Status: false
----------------------------------------------
2020-08-22 21:47:21,167 INFO [pool-235-thread-99][] cisco.cpm.posture.runtime.AgentlessPostureErrorHandler -::::- Handle error for sessionId=0A7E6B64000015D83F0FEA54, AgentlessFlowStatus=Failure
----------------------------------------------
2020-08-22 21:47:21,167 INFO [pool-235-thread-99][] cisco.cpm.posture.runtime.AgentlessPostureErrorHandler -::::- Calling triggerPostureCoA for sessionId=0A7E6B64000015D83F0FEA54
----------------------------------------------
2020-08-22 21:47:23,170 DEBUG [Posture-CoA][] cisco.cpm.posture.runtime.PostureCoA -:DOMINION\addot1xposture:::- Posture CoA is triggered for endpoint [00-50-56-01-02-03] with session [0A7E6B64000015D83F0FEA54]
Case3: If the endpoint IP isn’t reachable ..
When the Cisco ISE is not able to connect to the endpoints with IP address learned from RADIUS accounting, below log snippets are going to give you an idea why is it failing. You can rectify this problem by modifying your network so that Cisco ISE could reach the endpoint IP address learned from RADIUS accounting.
You can take a look at the logs (ise-psc.log) downloaded from Agentless Posture Troubleshooting page or if you want to debug the issue in a live environment, From the Cisco ISE PSN CLI, execute command show logging application ise-psc.log to identify the root cause.
----------------------------------------------
2020-08-22 22:46:49,057 DEBUG [PrRTEvents-Executor-2][] cisco.cpm.posture.events.NetAccessEventHandler -::::- Published message to POSTURE-INPUT for Agentless session 0A7E6B64000015F83F49274C
----------------------------------------------
2020-08-22 22:49:00,348 INFO [pool-235-thread-107][] cisco.cpm.posture.runtime.AgentlessPostureErrorHandler -::::- Handle error for sessionId=0A7E6B64000015F83F49274C, AgentlessFlowStatus=Failure
----------------------------------------------
2020-08-22 22:49:00,354 DEBUG [pool-235-thread-107][] cisco.cpm.posture.runtime.AgentlessTroubleshootingManager -::::- Started the Collect log process for MacAddress - 00:50:56:01:02:03
----------------------------------------------
2020-08-22 22:49:02,351 DEBUG [Posture-CoA][] cisco.cpm.posture.runtime.PostureCoA -:DOMINION\addot1xposture:::- Posture CoA is triggered for endpoint [00-50-56-01-02-03] with session [0A7E6B64000015F83F49274C]
Running scripts from "Run Endpoint Scripts" feature to find the root cause
Cisco Identity services engine 3.0 onwards supports Run Endpoint scripts feature. Through this feature, administrator can run scripts against the connected endpoints. When Agentless Posture is failing for a connected endpoint, you can make use of Run Endpoint Scripts feature to troubleshoot the issue.
- Once after login to Cisco ISE with super-admin privileges, from top right corner invoke Run Endpoint scripts wizard
- Run the wizard and select OS as category under category page
- Next screen Select Endpoints will show you all connected endpoints with windows/macOS category, Select the windows/macOS and then select endpoint(s) by filtering out with MAC address /IP address where Agentless posture is failing.
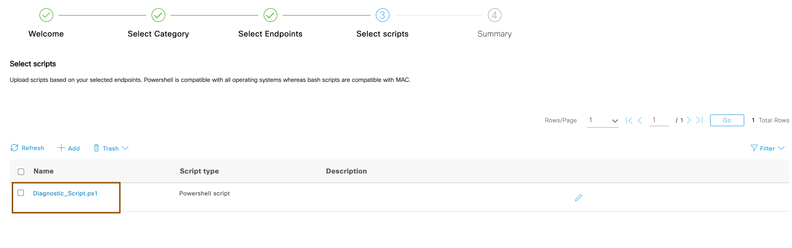
- Download the zip file from this page. Unzip the file and you would find two scripts one is for Windows and another is for macOS. Upload the script based on the operating system that you have selected.
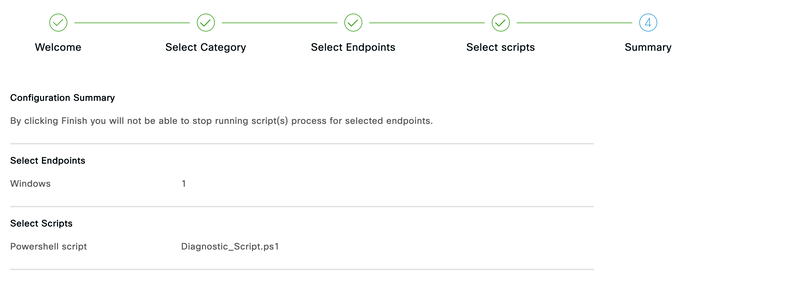
- Select the script and review the summary and submit the job.
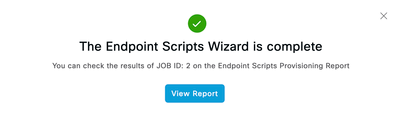
- Cisco Identity services Engine automatically runs this script against the endpoints selected and will give you report to find the root cause of the issue. Click on the View Report button.
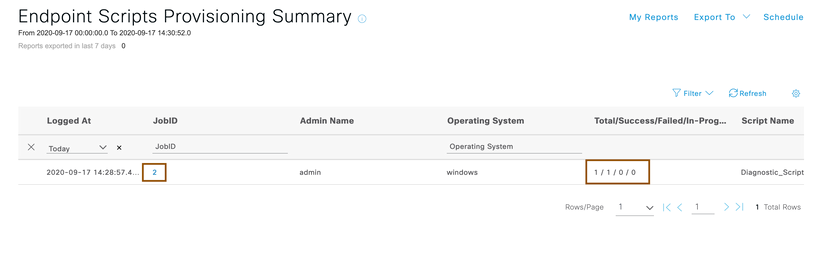
- You will get to know from the report whether diagnostic scripts uploaded was successfully ran on the endpoint or not. Click on the JobID.
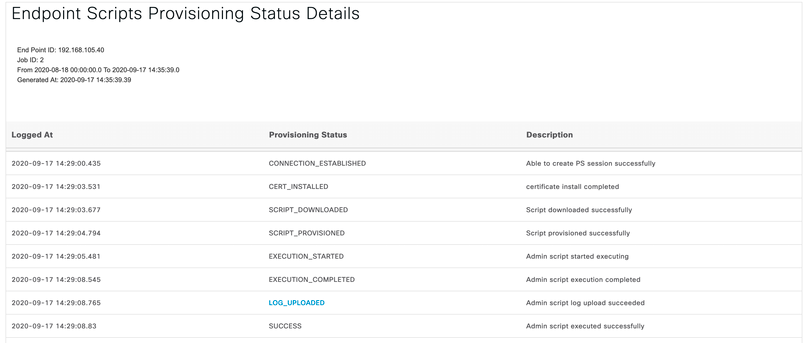
- Click on the endpoint IP
- Find out root cause whether it is an infrastructure issue or not from the details. You would be able to find out whether Cisco ISE is able to connect to the endpoint properly or not from below details
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: