- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Web Application Server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2024 11:18 PM - edited 04-26-2024 02:39 AM
Dear Community,
I'm asking for you guidance. I have come across a challenge on Cisco ASA version 9.8. Need to allow a web server to be access outside(Public) from DMZ Zone to Ouside Zone. Per below configuration template. Nat is transilating but access-list no hits which result that I can ping transilated IP from outside but I am not able to open application (to load a page). Kindly assist to receive the configuration and the packet tracer out form outside and DMZ leg shared.
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 200.100.1.2 255.255.255.248
!
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 192.168.50.1 255.255.255.0
!
interface GigabitEthernet0/2
nameif DMZ
security-level 80
ip address 172.16.10.253 255.255.255.0
!
!
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network LAN
subnet 192.168.50.0 255.255.255.0
object network ASDM
host 155.12.32.90
object network vpn_subnet
subnet 10.6.7.0 255.255.255.0
object network dmz_subnet
subnet 172.16.10.0 255.255.255.0
object network webserver-external-ip
host 200.100.1.2
object network web_server
host 172.16.10.50
object network MONITOR_SRV
host 192.168.50.114
object network SWITCH_HOST
host 192.168.50.2
object network OUTSIDE_INTERFACE
host 200.100.1.2
object network Water_Gateway_NAT
host 200.100.1.70
object network Water_Gateway
host 172.16.10.70
object-group network OBJ-SITE-ASA
network-object host 172.16.10.50
object-group network DMZ_SERVERS
network-object host 172.16.10.51
object-group network DMZ-Network
network-object 172.16.10.0 255.255.255.0
object-group network Outside-Network
network-object 200.100.1.0 255.255.255.0
object-group network NETWORK_Devices
network-object host 192.168.50.1
network-object host 192.168.50.2
network-object host 192.168.50.114
object-group service DM_INLINE_TCP_0 tcp
port-object eq www
port-object eq https
object-group service DM_INLINE_TCP_1 tcp
port-object eq www
port-object eq https
access-list management_access_in extended permit ip any any
access-list management_access_in extended permit icmp any any
access-list outside_access_in extended permit tcp any4 object Water_Gateway object-group DM_INLINE_TCP_1
access-list outside_access_in extended permit tcp any interface outside eq ssh
access-list outside_access_in extended permit tcp any interface outside eq 32007
access-list outside_access_in extended permit tcp any host 41.188.165.190 eq https
access-list outside_access_in extended permit icmp any4 any4
access-list outside_access_in extended permit tcp any object Water_Gateway eq www
access-list outside_access_in extended permit tcp any object Water_Gateway eq https
access-list dmz_access_in extended permit tcp object Water_Gateway any eq https
access-list dmz_access_in extended permit tcp object Water_Gateway any eq www
access-list dmz_access_in extended deny ip any object LAN_network
access-list dmz_access_in extended permit ip any any
access-list ACL_MACOS standard permit host 192.168.50.114
access-list ACL_MACOS standard permit host 192.168.50.2
access-list ACL_MACOS standard permit host 192.168.50.1
access-list ACL_MACOS standard permit 172.16.10.0 255.255.255.0
access-list dmz_access_out extended permit icmp any any
access-list inside_access_in extended permit ip host 200.100.1.1 10.6.7.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu INSIDE 1500
mtu DMZ 1500
mtu MGMT 1500
no failover
no failover wait-disable
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-openjre-7202.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (INSIDE,outside) source dynamic LAN_network interface
nat (outside,any) source static ASDM ASDM destination static interface any
nat (outside,DMZ) source static vpn_subnet vpn_subnet destination static dmz_subnet dmz_subnet
nat (INSIDE,outside) source static NETWORK_Devices NETWORK_Devices destination static vpn_subnet vpn_subnet
nat (DMZ,outside) source static dmz_subnet dmz_subnet destination static LAN_network LAN_network
!
object network LAN_network
nat (INSIDE,outside) dynamic interface
object network dmz_subnet
nat (DMZ,outside) dynamic interface
object network web_server
nat (DMZ,outside) static 200.100.1.51
object network Water_Gateway
nat (DMZ,outside) static Water_Gateway_NAT
access-group outside_access_in in interface outside
access-group dmz_access_in in interface DMZ
access-group dmz_access_out out interface DMZ
access-group management_access_in in interface MGMT
route MGMT 0.0.0.0 0.0.0.0 172.16.5.2 1
route outside 0.0.0.0 0.0.0.0 200.100.1.1 1
route outside 10.6.7.0 255.255.255.0 200.100.1.1 1
route outside 200.100.1.51 255.255.255.255 200.100.1.1 1
crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM
protocol esp encryption aes-256
protocol esp integrity sha-256
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint REMOTE_VPN
enrollment terminal
crl configure
crypto ca trustpool policy
crypto ikev2 enable outside
telnet timeout 5
!
t
webvpn
enable outside
hsts
enable
max-age 31536000
include-sub-domains
no preload
anyconnect image disk0:/anyconnect-macos-4.10.04065-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-win-4.10.04065-webdeploy-k9.pkg 2
anyconnect image disk0:/anyconnect-linux64-4.10.08029-webdeploy-k9.pkg 3
anyconnect profiles profile_macos disk0:/anyconnect_profile.xml
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev2 l2tp-ipsec ssl-clientless
group-policy ASA-TO-FTD internal
group-policy ASA-TO-FTD attributes
vpn-tunnel-protocol ikev2 l2tp-ipsec ssl-client
group-policy REMOTE_L2L_VPN internal
group-policy REMOTE_L2L_VPN attributes
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ACL_MACOS
default-domain value LAN.co.tz
webvpn
anyconnect profiles value profile_macos type user
dynamic-access-policy-record DfltAccessPolicy
tunnel-group REMOTE_VPN type remote-access
tunnel-group REMOTE_VPN general-attributes
address-pool VPN_POOL_MACOS
default-group-policy REMOTE_L2L_VPN
tunnel-group REMOTE_VPN webvpn-attributes
group-alias LAN_ONENET enable
tunnel-group LAN_DEVOPS type remote-access
tunnel-group LAN_DEVOPS webvpn-attributes
group-alias LAN_DEVOPS enable
!
——————————————————————————————————————————————
# packet-tracer input outside tcp 5.5.5.5 1234 200.100.1.70 80
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
MAC Access list
Phase: 2
Type: UN-NAT
Subtype: static
Result: ALLOW
Config:
nat (DMZ,outside) source static Water_Gateway Water_Gateway_NAT
Additional Information:
NAT divert to egress interface DMZ
Untranslate 200.100.1.70/80 to 172.16.10.70/80
Phase: 3
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group outside_access_in in interface outside
access-list outside_access_in extended permit tcp any object Water_Gateway eq www
Additional Information:
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (DMZ,outside) source static Water_Gateway Water_Gateway_NAT
Additional Information:
Static translate 5.5.5.5/1234 to 5.5.5.5/1234
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Phase: 8
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Result:
input-interface: outside
input-status: up
input-line-status: up
output-interface: DMZ
output-status: up
output-line-status: up
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rule
———————————————————————————————————————————————————————————
# packet-tracer input DMZ tcp 5.5.5.5 1234 200.100.1.70 80
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 200.100.1.1 using egress ifc outside
Phase: 2
Type: ACCESS-LIST
Subtype: log
Result: ALLOW
Config:
access-group dmz_access_in in interface DMZ
access-list dmz_access_in extended permit ip any any
Additional Information:
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 5
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Phase: 7
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 3476841, packet dispatched to next module
Result:
input-interface: DMZ
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
#
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 11:08 PM
Hi MHM,
I used Server IP.
Tell me on Cisco version 9.8. The nat rule work when using object-group or network-group.I think is the area I'm facing issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2024 11:44 PM
yes that can be but we must check traffic point by point
NOW
capture CAP1 interface OUT match ip host <the ip of PC you use for test>
Do this capture one time using ping
other using access to web server
Share result here
Thanks for waiting
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2024 08:30 AM
Hi MHM,
Here is the ouput
capture CAP1 type raw-data interface outside [Capturing - 0 bytes]
match ip host x.x.x.x host 200.100.1.70
capture asp-drop type asp-drop acl-drop [Buffer Full - 524276 bytes]
capture CAP2 type raw-data interface DMZ [Capturing - 0 bytes]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2024 08:33 AM
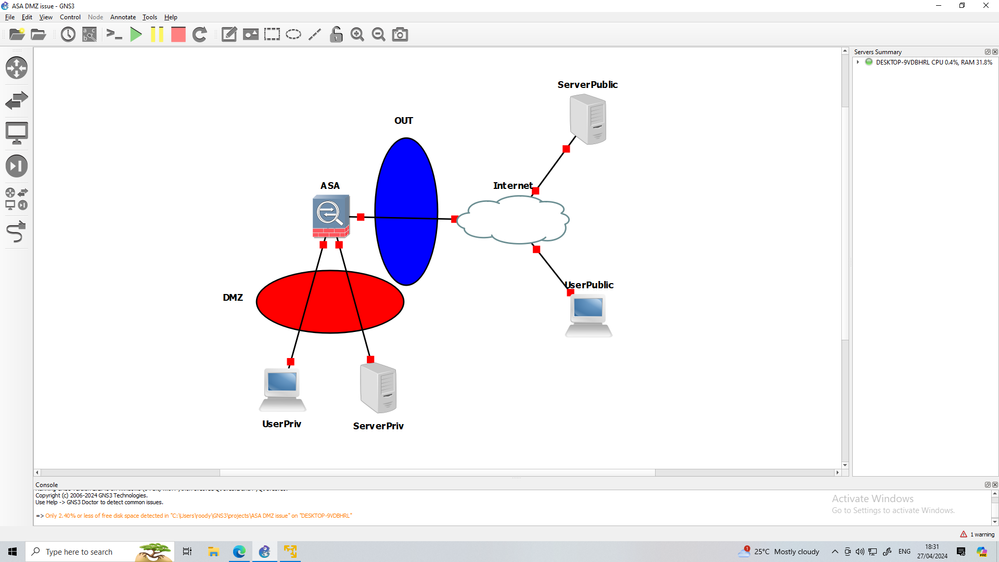
this is your topolgy
you want to access ServerPriv from the UserPublic?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2024 09:13 AM
Yes MHM.
I want to access the ServerPriv from UserPublic using Translated IP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2024 11:22 AM
Yes I get your request
please share the last config you use
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 01:24 AM
Hello MHM,
I wanted to let you know that I have successfully made a web server accessible to the public, and I appreciate your help.However, I have encountered a new problem. I would like to access the INSIDE LAN (192.168.50.0/24) from the DMZ-Network (172.16.10.0/24), but whenever I allow traffic through the below ACL, I end up dropping the traffic for the internet and the web server. Can you please guide me on how to configure the current settings to achieve my goal?
Here is the current configuration to try to apply.:
access-list inside_access_in extended permit ip 172.16.10.0 255.255.255.0 192.168.50.0 255.255.255.0
access-group in interface INSIDE
Below are the currently running configurations.
:
ASA Version 9.8(4)25
!
domain-name WATER.co.tz
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 200.100.10.2 255.255.255.248
!
interface GigabitEthernet0/1
nameif INSIDE
security-level 100
ip address 192.168.50.1 255.255.255.0
!
interface GigabitEthernet0/2
nameif DMZ
security-level 50
ip address 172.16.10.253 255.255.255.0
!
interface GigabitEthernet0/3
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/7
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
nameif MGMT
security-level 100
ip address 172.16.5.253 255.255.255.0
!
ftp mode passive
dns domain-lookup outside
dns server-group DefaultDNS
domain-name WATER.co.tz
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network INSIDE_NETWORK
subnet 192.168.50.0 255.255.255.0
object network dmz_subnet
subnet 172.16.10.0 255.255.255.0
object network webserver-external-ip
host 200.100.10.51
object network web_server
host 172.16.10.50
object network MONITOR_SRV
host 192.168.50.114
object network SWITCH_HOST
host 192.168.50.2
object network OUTSIDE_INTERFACE
host 200.100.10.2
object network WATER_Gateway_NAT
host 200.100.10.70
object network WATER_Gateway
host 172.16.10.70
object-group network OBJ-SITE-ASA
network-object host 172.16.10.50
object-group network DMZ_SERVERS
network-object host 172.16.10.51
object-group network DMZ-Network
network-object 172.16.10.0 255.255.255.0
object-group network Outside-Network
network-object 200.100.10.1 255.255.255.0
object-group network NETWORK_Devices
network-object host 192.168.50.1
network-object host 192.168.50.2
network-object host 200.100.10.1
network-object host 192.168.50.114
object-group service DM_INLINE_TCP_0 tcp
port-object eq www
port-object eq https
object-group service DM_INLINE_TCP_1 tcp
port-object eq www
port-object eq https
object-group network DMZ_HOST
network-object host 172.16.10.70
network-object host 172.16.10.71
network-object host 172.16.10.51
object-group network INSIDE_SUB
network-object 192.168.50.0 255.255.255.0
access-list management_access_in extended permit ip any any
access-list management_access_in extended permit icmp any any
access-list outside_access_in extended permit tcp any interface outside eq ssh
access-list outside_access_in extended permit tcp any interface outside eq 32007
access-list outside_access_in extended permit tcp any host 41.188.165.190 eq https
access-list outside_access_in extended permit tcp any host 200.100.10.51 eq www
access-list outside_access_in extended permit tcp any object WATER_Gateway eq www
access-list outside_access_in extended permit tcp any object WATER_Gateway eq https
access-list dmz_access_in extended permit ip object WATER_Gateway object INSIDE_NETWORK
access-list dmz_access_in extended permit ip host 172.16.10.70 any
access-list ACL_VPN standard permit host 192.168.50.114
access-list ACL_VPN standard permit host 192.168.50.2
access-list ACL_VPN standard permit host 192.168.50.1
access-list ACL_VPN standard permit host 200.100.10.1
access-list ACL_VPN standard permit host 200.100.10.2
access-list ACL_VPN standard permit 172.16.10.0 255.255.255.0
access-list dmz_access_inside_in extended permit ip any any
access-list inside_access_in extended permit ip host 200.100.10.1 10.6.7.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu INSIDE 1500
mtu DMZ 1500
mtu MGMT 1500
no failover
no failover wait-disable
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-openjre-7202.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (INSIDE,outside) source dynamic INSIDE_NETWORK interface
nat (outside,any) source static ASDM ASDM destination static interface any
nat (outside,DMZ) source static vpn_subnet vpn_subnet destination static dmz_subnet dmz_subnet
nat (INSIDE,outside) source static NETWORK_Devices NETWORK_Devices destination static vpn_subnet vpn_subnet
nat (DMZ,outside) source static dmz_subnet dmz_subnet destination static INSIDE_NETWORK INSIDE_NETWORK
nat (DMZ,outside) source static WATER_Gateway WATER_Gateway_NAT
nat (DMZ,INSIDE) source static WATER_Gateway WATER_Gateway destination static INSIDE_NETWORK INSIDE_NETWORK no-proxy-arp route-lookup
access-group outside_access_in in interface outside
access-group inside_access_in out interface INSIDE
access-group dmz_access_in in interface DMZ
access-group management_access_in in interface MGMT
route outside 0.0.0.0 0.0.0.0 200.100.10.1 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 01:36 AM
you have added the access rule to the wrong interface. you need to add the access rule to the DMZ interface.
access-list dmz_access_in extended permit ip 172.16.10.0 255.255.255.0 192.168.50.0 255.255.255.0
access-group dmz_access_in in interface DMZ
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2024 06:25 AM
Please provide a full sanitized running configuration of your ASA device. From your packet-tracer output it looks like the this traffic hitting your outside interface is trying to be encrypted, as indicated in Phase 7, which make me suspect there might be a misconfiguration for your VPN setup and the reason why access is not being granted.
Phase: 7
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Please provide a full running configuration (remove or change all usernames, passwords, and public IPs) for review.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 01:35 AM
Hello Marius,
Thank you for being ready to guide. I managed to get a workaround, but I got a challenge on allowing DMZ Zone to be accessed by Inside Zone.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 01:44 AM
if you are trying to access the DMZ from the inside network then you would need the following ACL entry:
access-list inside_access_in extended permit ip 192.168.50.0 255.255.255.0 172.16.10.0 255.255.255.0
access-group in interface INSIDE
Though I do recommend restricting access to the DMZ to specific IPs and ports if possible.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 01:57 AM
I have put in the command you shared. No response yet on ICMP between the
zone servers.
>From DMZ to INSIDE Zone.
DI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 02:00 AM
OK..I am a little confused...are you trying to access the inside network from the DMZ zone or are you trying to access the DMZ network from Inside zone?
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 02:30 AM
Hello Marius,
For example, I'm on Server 172.16.10.5. I want to be able to reach 192.168.50.10.
DI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2024 02:04 AM
To access from DMZ to Inside you would need the following ACL:
access-list dmz_access_in extended permit ip 172.16.10.0 255.255.255.0 192.168.50.0 255.255.255.0
access-group dmz_access_in in interface DMZ
Please remember to select a correct answer and rate helpful posts
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide