- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Tracking an IP address through the IPSEC VPN Tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Tracking an IP address through the IPSEC VPN Tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2023 10:57 AM
Hello,
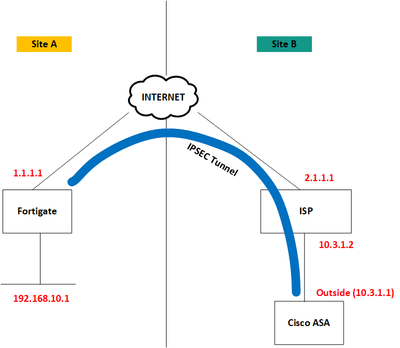
I have built an IPSEC site to site VPN tunnel from one of our Cisco ASA to Fortigate firewall. The tunnel is up and running and traffic is passing though the tunnel as expected. Now I have a requirement to track the tunnel status via SLA monitor in the ASA and the track destination I want to use an IP address at the other site. The setup is as shown below.
The IPSEC tunnel is built between 10.3.1.1 and 1.1.1.1. I need to track the IP address 192.168.10.1. Since the track destination is a protected network, what will be source interface that I can put in the sla monitor configuration?. If it is not possible, can I use the management interface in the SLA monitor configuration to source ICMP packets?.
Thanks
Shabeeb
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2023 11:49 AM
@SHABEEB KUNHIPOCKER you cannot specify the source interface using SLA. You could amend the crypto ACL to include the outside interface IP address as a source for interesting traffic.
Why do you need to track the IP address 192.168.10.1 from the ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2023 04:22 PM
Hi Rob,
We have two data centers, I need to track the protected network from the DC ASA and remove the routes from DC1 ASA when the tracker goes down. Then the routes will be injected from DC2 and the traffic will pass through DC2 ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2023 12:26 AM
@SHABEEB KUNHIPOCKER amend the crypto ACL (as previously suggested) will work or migrate to a route based VPN using VTI's with a routing protocol, which would be a better design.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide