- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE failing user check using TEAP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE failing user check using TEAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 05:32 AM
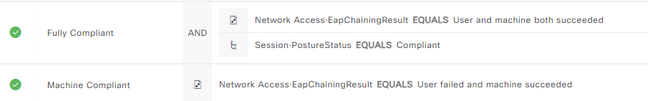
We have successfully deployed the TEAP policy using Cisco's documentation . The challenge seems to be that the Machine Compliant policy is the only hit we are getting. Never hits the Fully Compliant policy.
- Windows supplicant is provisioned as per documentation to use EAP-TLS for both primary and secondary EAP methods.
- Both computer and user root cert providers are the same
- User certificate is provisioned for "Client Authentication" and located in the Personal->Cert store on the workstation
We are seeing this in the log - any ideas on what to look for?
| 11627 | Starting EAP chaining | |
| 11573 | Selected identity type 'User' | |
| 11564 | TEAP inner method started | |
| 11521 | Prepared EAP-Request/Identity for inner EAP method | |
| 11596 | Prepared EAP-Request with another TEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 11595 | Extracted EAP-Response containing TEAP challenge-response | |
| 11567 | Identity type provided by client is equal to requested | |
| 11522 | Extracted EAP-Response/Identity for inner EAP method | |
| 11806 | Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge | |
| 11596 | Prepared EAP-Request with another TEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 11595 | Extracted EAP-Response containing TEAP challenge-response | |
| 11515 | Supplicant declined inner EAP method selected by Authentication Policy but did not proposed another one; inner EAP negotiation failed | |
| 11520 | Prepared EAP-Failure for inner EAP method | |
| 11566 | TEAP inner method finished with failure | |
| 22028 | Authentication failed and the advanced options are ignored |
- Labels:
-
AAA
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 09:36 AM
Yes, but if the cert has multiple, and maybe the one that ISE picks doesn't match the identity on the AD. To avoid this, you can select the right attribute manually in the certificate authentication profile and see if that fixes the issue.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide