- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE failing user check using TEAP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE failing user check using TEAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 05:32 AM
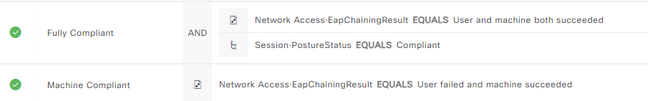
We have successfully deployed the TEAP policy using Cisco's documentation . The challenge seems to be that the Machine Compliant policy is the only hit we are getting. Never hits the Fully Compliant policy.
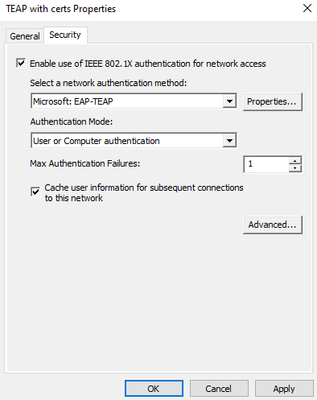
- Windows supplicant is provisioned as per documentation to use EAP-TLS for both primary and secondary EAP methods.
- Both computer and user root cert providers are the same
- User certificate is provisioned for "Client Authentication" and located in the Personal->Cert store on the workstation
We are seeing this in the log - any ideas on what to look for?
| 11627 | Starting EAP chaining | |
| 11573 | Selected identity type 'User' | |
| 11564 | TEAP inner method started | |
| 11521 | Prepared EAP-Request/Identity for inner EAP method | |
| 11596 | Prepared EAP-Request with another TEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 11595 | Extracted EAP-Response containing TEAP challenge-response | |
| 11567 | Identity type provided by client is equal to requested | |
| 11522 | Extracted EAP-Response/Identity for inner EAP method | |
| 11806 | Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge | |
| 11596 | Prepared EAP-Request with another TEAP challenge | |
| 11006 | Returned RADIUS Access-Challenge | |
| 11001 | Received RADIUS Access-Request | |
| 11018 | RADIUS is re-using an existing session | |
| 11595 | Extracted EAP-Response containing TEAP challenge-response | |
| 11515 | Supplicant declined inner EAP method selected by Authentication Policy but did not proposed another one; inner EAP negotiation failed | |
| 11520 | Prepared EAP-Failure for inner EAP method | |
| 11566 | TEAP inner method finished with failure | |
| 22028 | Authentication failed and the advanced options are ignored |
- Labels:
-
AAA
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 05:43 AM
@Chris S the logs imply there is a problem with the EAP method, is the supplicant configured correctly?
You are using a Posture compliant condition in the rule (this is not a requirement for TEAP), I assume the device has actually passed the posture compliance check without problem?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 05:47 AM
@Rob Ingram Agree - but I can't see anything setup differently than the recomended settings. If I switch the supplicant to be MSCHAP, it works just fine.
Yes, posture is working ok.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 05:57 AM
One item to add that i'm working on - when the computer is turned on (no user logged in), it's only using MAB (which fails). Doesn't look like any EAP auths are being done until a login event occurs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:01 AM
@Chris S wrote:
One item to add that i'm working on - when the computer is turned on (no user logged in), it's only using MAB (which fails). Doesn't look like any EAP auths are being done until a login event occurs.
@Chris S that should not be the case, it should at least authenticate the machine, so it should match your "Machine Compliant" AuthZ rule.
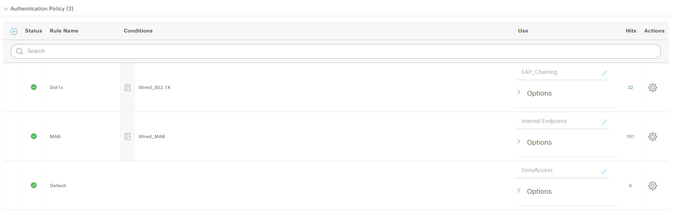
Can you provide a screenshot of your Authentication Policy, CAP and Allowed Protocols please?
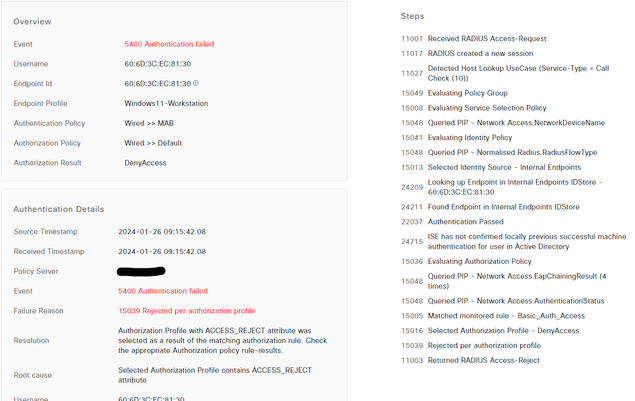
And a screenshot of the machine failing MAB.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:24 AM
I'm not sure what CAP is?
Auth Policy:
Allowed Protocols :
Computer MAB Failure:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:31 AM
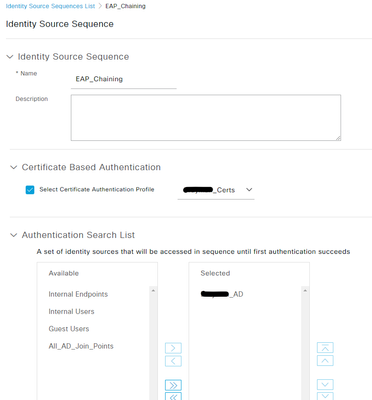
@Chris S CAP = Certificate Authentication Profile. What is EAP_Chaining and how is it configured?
I would suggest the supplicant is misconfigured, please provide screenshots of how the windows supplicant is configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:46 AM
EAP_Chaining uses the certificate auth profile referencing our domain certs then active directory. The cert profile looks in the subject or alternative name attirbute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:33 AM
@Rob Ingram My apologizes - the MAB issue was due to the wired auto config service not starting. That is now fixed. So the computer will pass the machine cert successfully before login .. but after the user logs in, it still complaining about that error in the first posting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:53 AM
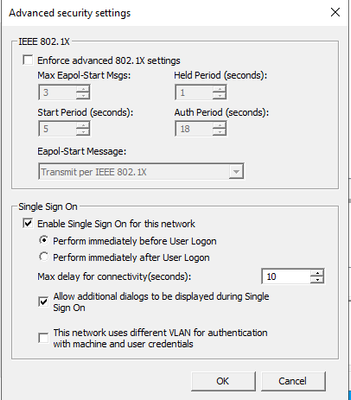
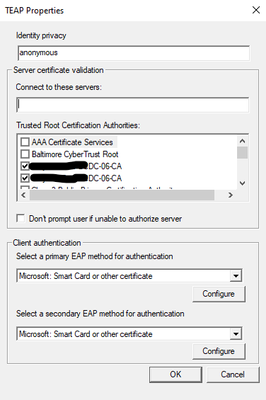
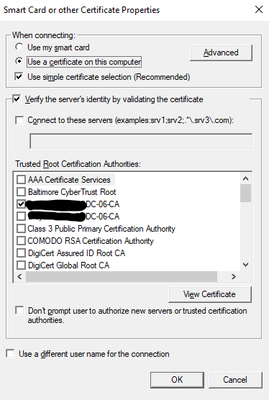
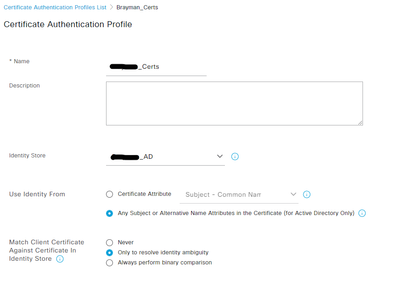
Could you please share ISE certificate authentication profile settings and the identity source sequence "EAP_Chaining" for review?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 06:57 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 07:27 AM
@Rob Ingram If I change the supplicant to be MSCHAP and the user types their credentials, I hit the "Fully Compliant" policy. With how ISE evaluates, would the policy care between cert based or password based?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 07:39 AM - edited 01-26-2024 08:06 AM
@Chris S the authorisation policy rule does not discriminate between authentication protocol, merely whether user and computer succeeded (and posture compliance). So there is some reason why user TEAP with TLS certificate is failing then.
Check the user certificate store and confirm the certificate is valid and using the correct template.
Take a tcpdump on ISE of the user authentication attempt and confirm the user identity being sent and the protocol etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 07:36 AM
I would try to change the "Use Identity From" in the certificate authentication profile to be "Certificate Attribute" and select the attribute from the dropdown menu. The attribute you selected should be the one you see on the user certificate, typically it would be the DNS SAN value.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-26-2024 07:39 AM - edited 01-26-2024 07:40 AM
@Aref Alsouqi But wouldn't the "Any subject or Alternative Name.." checkbox cover that? And also - would I have to create two separate profiles - 1 for users and 1 for machines?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide