- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Anyconnect username USERNAME
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Anyconnect username USERNAME
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 12:47 PM
ASA version 9.14(4)7 | Anyconnect 4.10 | ISE 2.6
ISE is authenticating our Annyconnect Clients that connect via a Cisco ASA. We'll get hit with hundreds of connection attempts from questionable countries with the username USERNAME (or at least that's what ISE reports). Typically we'll lose the ability to service any new anyconnect sessions for about 15 minutes after. I created a local user USERNAME specifically to reject the attempts and when I try to authenticate it does just that. Then later, I see that rejection isn't working against this attack. Anyone else see this? Any working solutions?
Attached are events that represent when I tried to auth vs the attack.
- Labels:
-
Identity Services Engine (ISE)
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 12:56 PM
@anthony.mchie best option would be to filter the traffic from those questionable countries before they even attempt to authenticate. You can do this with geolocation filtering on NGFW firewall placed in front of the ASA. You do have the option to use a control-plane ACL on the ASA itself, to restrict IP addresses initating traffic to the ASA.
What is causing the loss of service for 15 minutes, the ASA itself?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 01:18 PM
@Rob Ingram wrote:
@anthony.mchie best option would be to filter the traffic from those questionable countries before they even attempt to authenticate. You can do this with geolocation filtering on NGFW firewall placed in front of the ASA. You do have the option to use a control-plane ACL on the ASA itself, to restrict IP addresses initating traffic to the ASA.
What is causing the loss of service for 15 minutes, the ASA itself?
My answer would only be a guess since I don't see any logging events that clue me into the cause.
Don't have an NGFW in front (unfortunately) so I'll have to find another way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 01:12 PM
Use control-plane'
Allow only vpn pool subnet access to ISE.
Note:- allow management IP if you use it with ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 01:17 PM
Not entirely sure how to protect your VPN from outside actors. I have seen some customers put their VPN on non-standard TCP ports. You don't have to run your SSL VPN on TCP/443. Choose a tricky port number like 50443
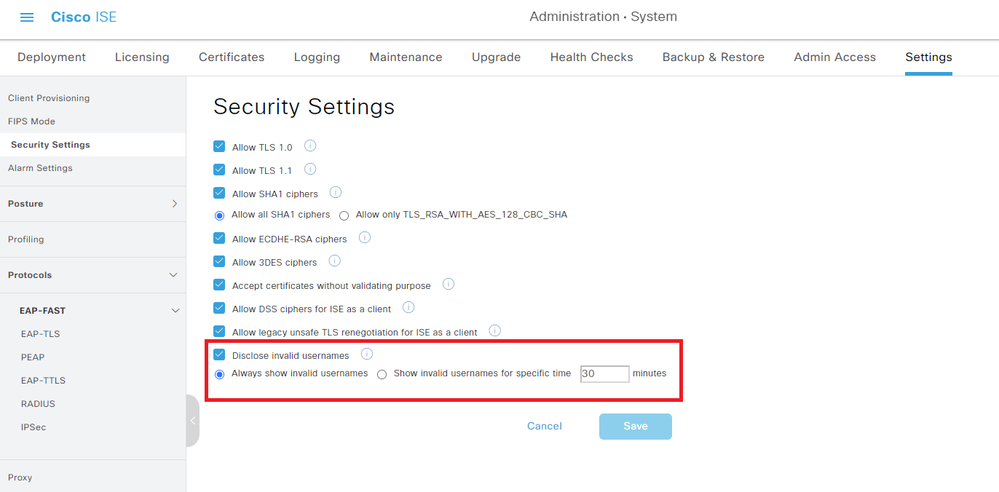
USERNAME is just a standard string that ISE displays when it doesn't want to reveal the real username. By default, failed authentications have their username obfuscated with the string 'USERNAME' to protect the innocent (e.g. a user accidentally entering their password into the username field ... it happens
You can reveal the username by navigating to Administration > System > Settings > Security Settings
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 01:19 PM
Not issue with username only'
The user is fialed to auth to Asa via ISE.
So I think he under some ddos.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2023 01:21 PM
@Arne Bier That's going to help quite a bit. Thank you!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide