- Cisco Community
- Technology and Support
- Security
- Duo Security
- Managing Users
- Re: Is it possible to protect all interactive logins for a single Windows (AD) account across my net...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Is it possible to protect all interactive logins for a single Windows (AD) account across my network and only affect that account?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2017 11:17 AM
Hello all,
I was highly disappointed to see that the feature for Windows interactive logins was only applicable to all logins on a target workstations. I assumed incorrectly that the credential provider relied on the use of the Auth Proxy, which performed the necessary lookups and bypassed secondary auth or required secondary auth.
I see that it’s possible to administer credential providers in a variety of ways, but do not see a way to redirect login requests from a workstation to an alternate LDAP server (for instance), which is okay and a little bit out of scope.
If I remove the key under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Provider Filters\, with the GUID for Duo, I am able to select “Sign-in Options,” which is unavailable with the Credential Provider Filter present. This is partially acceptable, as once this change is made, the Default Provider falls back to the PasswordProvider (the “regular” provider in Windows), however we would require the enforcement of the use of a Credential Provider for a specific user… something that I’m not sure is possible as Credential Providers are “stand-alone” on local systems and only integrate into systems as they are specifically designed (there isn’t an AD attribute that I have found that would specifically require a credential provider having been used for User N).
I have posted about a hopeful alternative in the MSFT forums: https://social.technet.microsoft.com/Forums/en-US/8e77105c-dcd3-4b10-9660-dff4c7418568/is-it-possible-to-enforce-credential-provider-per-active-directory-user?forum=win10itprosecurity and cross posted on serverfault http://serverfault.com/questions/832570/is-it-possible-to-enforce-a-specific-credential-provider-per-active-directory-us
Is it possible to use Duo for secondary authentication only for specific user accounts for interactive Windows logins across any host on a network? For instance, we wish to protect only certain accounts, let’s say contoso\admmatt, but not bother others, like my user contoso\matt. Is it possible to leverage SAML with ADFS in some way?
Thanks,
Matt
- Labels:
-
Directory Sync
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 07:23 AM
Hello,
With Duo for WinLogin, you can choose which users are prompted for Duo. Depending on the status of other users accessing that host you will need to use either the New User Policy or Group Access Policy to bypass them.
You also can use the authproxy as an outbound http proxy for WinLogin protected hosts if needed,
Unless I’m missing something, the only part that doesn’t quite map how you like is that the Duo Credential Provider would need to be installed on each host, rather than putting in somehow on the account at the directory level. We have an MSI and Group Policy template to help you deploy the package at scale.
edit: typo
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 09:38 AM
Thank you!
New User Policies will be global.
We currently have two policies affecting the following:
- cisco anyconnect
- cisco ipsec
After reviewing the “New User Policy,” and require enrollment or bypass tfa, it looks like this will affect the /user/ globally, not just when the user uses the Application? In this case, this won’t work for us. Is this just my lack of knowledge about Group Policies?
It appears that instead using a “Group Access Policy” and assigning a group of users allows me to declare which users I don’t want to use Duo authentication (by makign them members of a specific group, then apply the group policy to the application). I’d much rather declare which users I do want to have to use Duo to authenticate and leave the other users to bypass for this application.
Is this possible?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 10:22 AM
Hey Matt,
You can do this several ways.
Option 1 - Leave New User Policy set to “Allow Access” and only 2FA enrolled users. This is the easiest and least secure. Non Duo enrolled users are still vulnerable to breach, and bad actors can usually move laterally once they have a foothold.
Option 2 - Enroll all your users in Duo, but use groups (either in Duo or sync them from AD) and Group Access Policy to let users who are enrolled and use Duo for some Duo protected applications, bypass Duo prompts for other Duo protected applications. (Like WinLogin / RDP). https://duo.com/docs/policy#group-access-policy
There are likely more on top of that - Group specific policies are a part of Access Edition, if you are on MFA edition you won’t have that as an option. You can always get a 30 day trial of Access to see if the features meet your needs.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 10:36 AM
The issue is that we have all users enrolled in Duo, but we would wish for them not to be prompted.
I can confirm that we have the Access Edition.
I have applied the policy scoped to an application and a group of users:
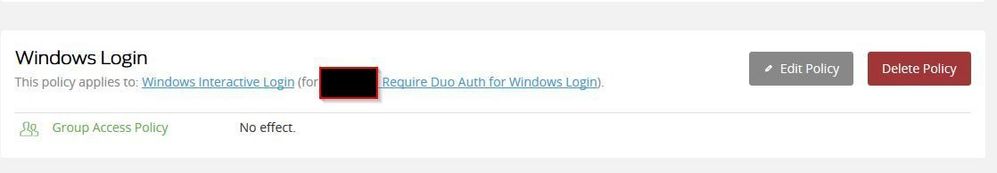
The “Group Access Policy” method works, but we must administer exclusion instead of inclusion, which is error prone and burdensome. Is this our only option?
Thanks,
Matt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 11:01 AM
Hey Matt,
This is intended to be used in conjunction with AD Sync, (https://duo.com/support/documentation/syncing_users_from_active_directory) so you can have a single group in AD of all your users, and just remove the users from that group when they need to be challenged on those Windows hosts. These changes will sync to Duo automatically.
Also, you will want Group Access Policy set to “Allow Access without 2FA”. (Otherwise it wouldn’t do anything)
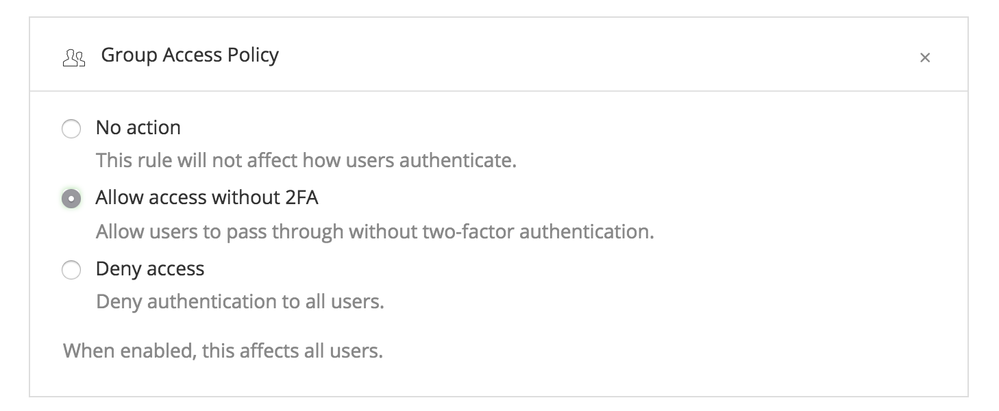
We will be adding the ability to drive these Policies via API in the future if you need to automate them more than that.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 11:49 AM
Thank you!!!1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2017 01:06 PM
Sorry two more concerns here…
-
Once the password is entered, it is still present/it is saved when the attention prompt is hit again. How do I disable this?
-
Even though I set “New User Policy\Allow unenrolled users to pass through without two-factor authentication” on an Application, it doesn’t take effect if/when the Global Policy for “Allow unenrolled users to pass through without two-factor authentication” is set to require enrollment. Is this supposed to happen?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2017 01:01 PM
Hey Mbrown,
- Once the password is entered, it is still present/it is saved when the attention prompt is hit again. How do I disable this?
I don’t totally understand the question. Duo doesn’t save passwords anywhere. Can you provide a screenshot or example?
- Even though I set “New User Policy\Allow unenrolled users to pass through without two-factor authentication” on an Application, it doesn’t take effect if/when the Global Policy for “Allow unenrolled users to pass through without two-factor authentication” is set to require enrollment. Is this supposed to happen?
You should check out:
and
For all the details, but essentially more specific policies (group) should override less specific ones. (global)
Cheers
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide