- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Unifi USG L2TP VPN with DUO 2FA setup - Need help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Unifi USG L2TP VPN with DUO 2FA setup - Need help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2020 05:58 AM
I am struggling on setting up DUO 2FA on the L2TP VPN with DUO proxy on Windows server. The settings between Unifi and Windows DUO proxy is pretty straight forward. I have experience in setting DUO using Cisco ASA <> Windows but I was unable to make it happen on Unifi. Anyone has experience on this? I’ve seen this post: https://community.ui.com/questions/Duo-Security-Proxy-for-Windows-works-on-Unifi-a-few-notes/ceb6c9bb-73f4-4a38-83f3-c604323bfdbd
and somehow I got error every time when I connecting to VPN.
The error in the DUO authproxy.log:
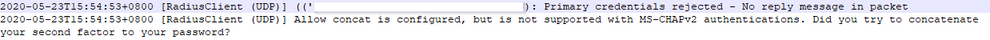

Any help would be appreciated. Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2020 01:25 PM
I too experienced the same error, but have partial workaround. I have yet to resolve completely, but my theory is how the USG is formatting the RADIUS packet across to the Duo Authentication Proxy (DAP). The authentication string is not being recognized by DAP. I tried with MS-CHAPv2 on and off, I tried with allow_concat=false, and pass_through_all=true, without any change in behavior.
I do have a partial workaround, but must use the USG RADIUS server for the first authentication factor. Good news - I get MFA; Bad news - I can’t use LDAP authentication (yet… , but going to keep trying).
Here is a snippet from my authproxy.cfg file:
[radius_client1]
; IP address of my USG
host=172.31.0.1
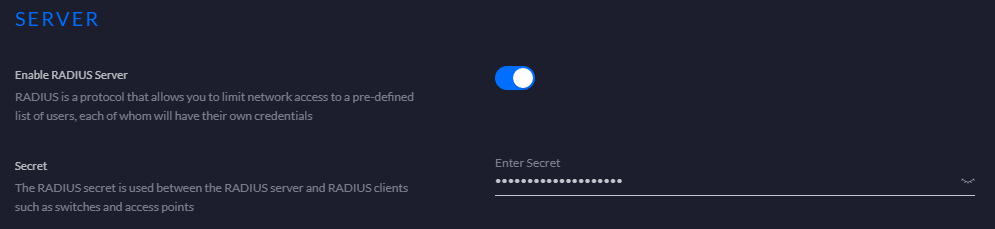
; RADIUS Secret from Unifi Controller in section Gateway > RADIUS > SERVER > Secret. This allows DAP to connect to RADIUS on the USG.
secret_protected=
[radius_server_auto3]
client=radius_client1
; Duo.com Application ‘Type: RADIUS’
ikey=*
skey_protected=*
api_host=*
; IP address of Unifi USG interface. This allows the L2TP requests to come from this IP address.
radius_ip_2=172.31.0.1
; RADIUS Secret from Unifi Controller in section Configuration Profiles > RADIUS > Create New RADIUS Profile. This allows the L2TP VPN request to be sent to the DAP server.
radius_secret_protected_2=
factors=auto
failmode=secure
;Need to set a unique port from my other sections. This must match the RADIUS Server profile in screenshot below.
port=1816
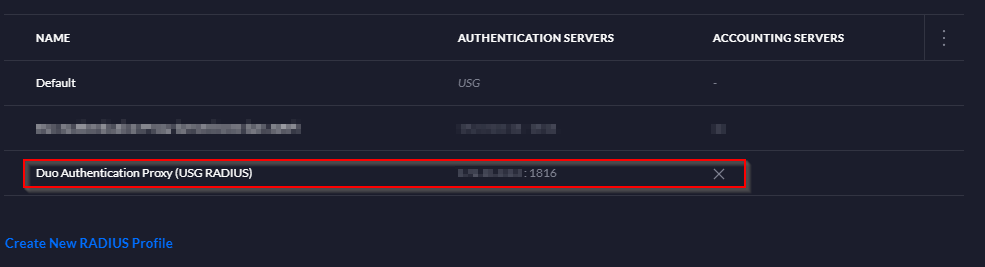
This RADIUS Server, is then bound to the L2TP User VPN configuration on the Unifi Controller under VPN > VPN Servers > Type L2TP.
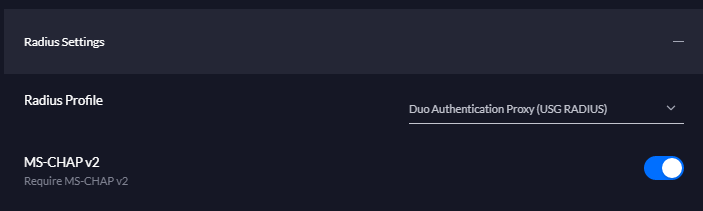
Here is what happens:
- I establish L2TP VPN to USG providing credentials within USG RADIUS Server.
- USG gets the connection request, forwards RADIUS authentication to the DAP.
- The DAP receives the authentication, then forwards primary authentication back to the USG RADIUS server.
- Primary authentication passes, and the DAP proceeds with Duo secondary authentication using push, SMS, etc.
- Connection established!
It works only because the DAP doesn’t need to interpret the RADIUS authentication string from the USG, instead it simply passes it through back to the USG RADIUS server.
It isn’t exactly what we are looking for, but it does allow Duo MFA with my Unifi USG.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2020 08:09 AM
I was able to get the USG and Duo working together by using the Duo Auth Proxy and having it connect to the Network Policy Server (NPS) running on my windows server. I talked with support because I couldn’t get the above working and they gave me the suggestion to use the NPS instead. Here’s what I did:
I am assuming a VPN is already in place with the USG, just moving it to work with Duo.
In the USG controller go to Profiles --> Create new RADIUS profile
Profile Name : Primary Domain Controller (PDC) name
Place both check marks under VLAN support: Enable RADIUS assigned VLAN for Wired network, Enable RADIUS assigned VLAN for Wireless network
RADIUS auth Server IP address set IP address of PDC
Port 18120
Generate a secure password and store it
Save the profile.
Under networks edit the VPN network and set it to use the RADIUS profile just created
Save
On the PDC
• From Server Manager Add Roles and Features. Select Network Policy and Access Services. Select Add Features to include the management tools. Next several times and then install.
• Once the feature is installed you can select NPAS or NAP depending on server version on the left. Then right click on the local server and choose Network Policy Server.
• Expand RADIUS Clients and Servers right click on RADIUS Clients and new.
1. Set check for Enable this RADIUS Client
2. Friendly name: Duo Auth Proxy (DAP)
3. Set IP Address of the machine with DAP.
4. Set Manual Share secret and paste in the shared secret you created above.
5. Press OK
• Leave your window open and go to Active Directory. Make a new security group VPN-Users. Add users who will access the VPN.
• Switch back to the Policy Server. Expand Policies --> Network Policies.
1. Right click on Network Policies on the left, select New.
2. Set Policy name as Unifi VPN, leave Type of network access server as Unspecified. Click Next
3. Click Add to put in a condition: Select Windows Groups and click Add
4. Click Add Groups and put in the VPN-Users group we created before. Click OK, Click Next.
5. Make sure Access granted is selected and press next.
6. On the Configure Authentication Methods remove check mark for MS-CHAP. Click Next.
7. Set Idle Time out to disconnect after the maximum idle time of 30 minutes. Click Next.
8. Select the Encryption table and remove check marks so only Strongest encryption (MPPE 128-bit) is selected. Click Next.
9. Click Finish
• For the users you’ll only need to add them to the VPN-Users group. If you’re converting from a PPTP VPN you may need to edit the users and set the Dial-In tab to "Control access through the NPS Network Policy.
Still on the PDC edit the Duo Auth Proxy config and add these sections
[radius_client]
host=local host IP
secret=generated secret from above
port=1812
[radius_server_auto]
ikey=from Duo application
skey=from Duo application
api_host=from Duo application
radius_ip_1=Firewall IP
radius_secret_1=generated secret from above
client=radius_client
failmode=safe
port=18120
Restart the Duo Auth Proxy service
Test. This had it working for me. You’ve got a bit under 30 seconds to respond to the Push on your phone before the connection times out. If there is a way to control this it would be via SSH and I don’t know the specifics.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 04:38 PM
Matthew I tried to get 2FA working with ADSelfService Plus from Manage Engine and it was a failure. Ubiquiti told me it does not currently work at all. WOuld you be willing to talk me through some of this??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2021 05:52 AM
I’m not at all familiar with ADSelfService Plus from Manage Engine so I’m not sure how much help I can be but I’m willing to give it a go. Honestly you might be better served by creating your own forum post with as many details as you can - link me to it and I’ll respond there and that way you also potentially get help from others who might be more familiar with your setup. Good Luck!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-28-2020 04:34 AM
You can setting up DUO 2FA towards other vpn like Nord, Circuit Vpn here you can easily setup DUO 2FA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2021 01:51 PM
Not sure if it still relevant but I wrote a full blog how to enable Remote Access (VPN) with Duo Security and NPS (Network Policy Server).
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: