- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- SonicWall SMA200 / [radius_server_auto] only works with Chrome
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SonicWall SMA200 / [radius_server_auto] only works with Chrome
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 11:29 AM
Just got a SonicWALL SMA200 VPN appliance and set up DUO using instructions here https://duo.com/docs/sonicwallsra. When I go to log in using a web browser I click “Send me a Push” and tap “Accept” on my phone using Google Chrome, I am logged in and all is well. But if I do the same thing with FireFox or Internet Explorer, it hangs at “Success! Logging You In” and never advances to the next page. At one point it was doing this with Chrome as well. Not sure what changed that it started working with Chrome.
I opened a ticket with DUO support and was told that this link is only for SRA and SMA100 and I need to use instructions here instead https://duo.com/docs/radius. I did that and it works, but I am not presented with multiple 2FA options (which is what we want). It just does a push without any prompt.
Can anyone suggest how I might get this to work so users are presented with multiple 2FA options?
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2019 01:31 PM
The SonicWALL iframe integration is for the SMA 100 Series, which includes the SMA 200, SMA 400, and SMA 500v. I’m sorry Duo Support gave you incorrect information! It’s possible the support engineer misunderstood our documentation.
I just tried the radius_server_iframe experience on a SMA 200 running 9.0.0.3-17sv firmware in Firefox 65.0.1 and 66.0.2, and in Internet Explorer 110.09600.19036, and I am able to log in by selecting the push option from the Duo Prompt.
Please try contacting Duo Support again to open a case for troubleshooting assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-25-2019 01:00 PM
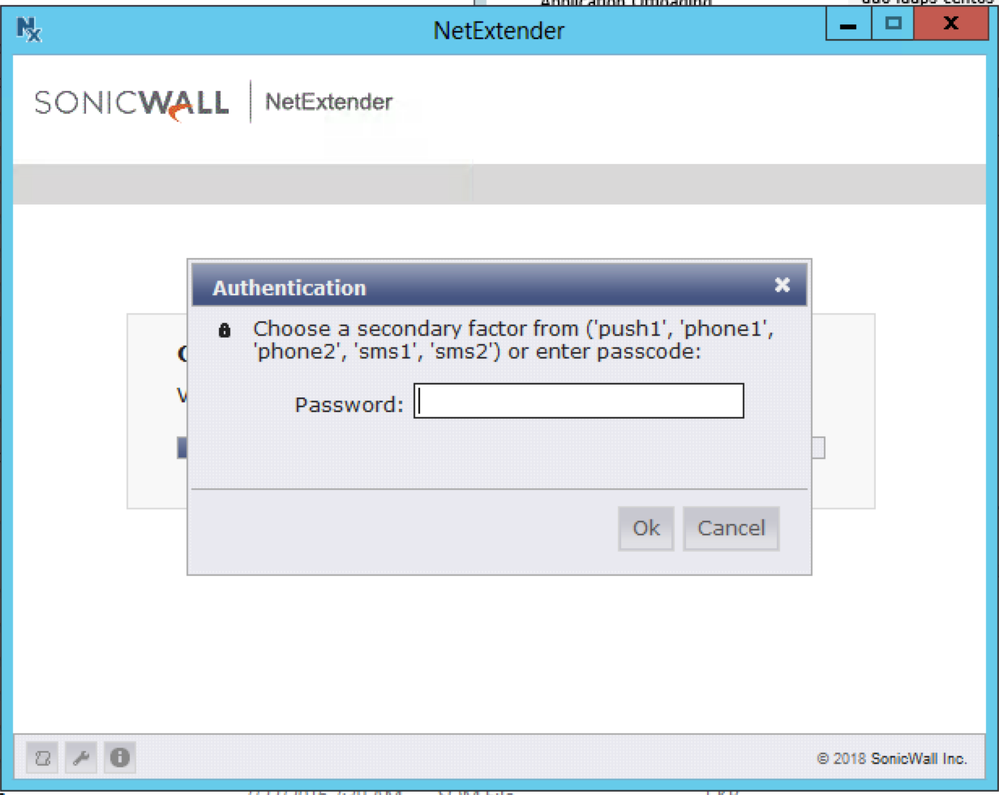
i got it to work using radius_server_iframe when logging in using a web browser but not with Net Extender. With NetExtender, DUO pops up a dialog box that says “Challenge” containing a textbox that says “Password.” Nothing that I can figure out to enter works - but even so, what I want to see is the three 2FA options like now pops up when I log in with a web browser.
The DUO support person has told me that it doesn’t work right with Net Extender and there is nothing he can do. I don’t like that answer! Anyone else have any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2019 06:42 AM
I can double-check with our technical contacts at SonicWall but I believe that is correct that the iframe will not show up in the NetExtender client.
You can follow the SonicWall RADIUS Auto instructions for an auto-push experience, or follow the RADIUS Auto instructions except in the Duo config use [radius_server_challenge] (Duo Authentication Proxy Reference | Duo Security) instead of [radius_server_auto]. This won’t give you the interactive Duo prompt, but will show your users a text prompt that lists their authentication options.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2019 10:27 AM
Thanks Duo Kristina. I could live with that for the few users we have that use NetExtender if they were the only ones who had to do it this way, but really don’t want web browser users to have to do it as well. Is there any way to use [radius_server_challenge] only for NetExtender users bit still allow web browser users to see the radius_server_iframe prompt?
If not, is there any plans to add support for NetExtender for radius_server_iframe?
I can provide NetExtender users with the same 2FA prompts as with radius_server_iframe by having them click “bind” and then scan a QR code but that does not set up a DUO account under my DUO Admin Console. Seems like if I can get it to work this way it should also work via a DUO account I set for users .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2019 12:40 PM
I have relayed your request for Duo iframe prompt in NetExtender to SonicWall. I suggest you also open a support case with SonicWall requesting this, so they can note your interest as a customer.
You could create separate portals/domains on the SMA and separate configs on the Duo proxy for RADIUS iframe and challenge, and instruct users to choose accordingly depending on how they are accessing your SMA? On the Duo Proxy, that would entail having both the [radius_server_iframe] and [radius_server_challenge] sections, using unique ports, and then on the SMA point the right domain to the corresponding port.
I am not sure what you are describing in your last paragraph. Do you mean that the users are scanning the QR code to add your SonicWall device as a third-party OTP account to Duo Mobile (as described here: https://guide.duo.com/third-party-accounts).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2019 01:08 PM
Thanks much DuKristina for your very helpful instructions. I will set up a separate portal for net extender as you described and that should accomplish what
I was asking – to only require NetExtender users to type in “push1” to get a push.
I was mistaken on my last statement. I have another portal set up that works the way your link describes but users have to enter a code via the DUO app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2019 01:39 PM
Thanks again DuoKristina. I got NetExtender working as you described running on a different port. SonicWALL has put in a bug report on NetExtender not working with [radius_server_iframe] so hopefully we’ll be able to do it that way in the near future once fixed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2019 12:07 PM
Is this really not fixed yet? Makes no sense - SonicWALL gives popup to put in challenge code and DUO responds with incorrect RADIUS Challenge.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-20-2019 12:22 PM
We ended up using radius_server_auto with a different SonicWALL domain for NetExtender and users get a push with no other options. I was concerned that the push might fail occasionally and users would not have a fallback option for 2FA but it hasn’t happened yet. So far it’s been a non-issue.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide