- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- RADIUS Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RADIUS Authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 02:28 AM
Hi everyone,
I’m trying to add duo to a RADIUS authentication process to a router client device.
My normal RADIUS implementation works fine, from my DUO auth proxy box (with it all turned off) I can ssh to the router using domain credentials, running a packet capture on the NPS I can see requests and responses and authentication succeeds.
When DUO enters the equation things get a bit more difficult. I have configured the authproxy.cfg as follows:
;CLIENTS:
; Radius #Lab
[radius_client]
host=192.168.254.59
secret=XXXXXXXXXXXXXXX
; port=
; SERVERS:
; Radius #Lab
[radius_server_auto]
ikey=XXXXXXXXXXXXXXXXXXXX
■■■■
api_host=■■■■
radius_ip_1=192.168.254.1
radius_secret_1=XXXXXXXXXXXXXXXX
failmode=safe
client=radius_client
port=1812
The connectivity tool reports the following errors:
[duoauthproxy.lib.log#info] There are no configuration problems related to connectivity.
[duoauthproxy.lib.log#error] We cannot confirm that the Auth Proxy was able to establish a RADIUS connection to 192.168.254.59:1812. In the case of an actual failure this may be due to a misconfigured secret or network issues. This may also happen if the upstream RADIUS Server does not support the Status-Server message
[duoauthproxy.lib.log#debug] Exception:
[duoauthproxy.lib.log#info] -----------------------------
[duoauthproxy.lib.log#info] Testing section ‘radius_server_auto’ with configuration:
[duoauthproxy.lib.log#info] {‘api_host’: ‘■■■■’,
‘client’: ‘radius_client’,
‘debug’: ‘True’,
‘failmode’: ‘safe’,
‘ikey’: ‘XXXXXXXXXXXXXXXXXXXX’,
‘port’: ‘1812’,
‘radius_ip_1’: ‘192.168.254.1’,
‘radius_secret_1’: ‘’,
‘skey’: '[40]’}
[duoauthproxy.lib.log#warn] The RADIUS Server has connectivity problems.
[duoauthproxy.lib.log#info] There are no configuration problems related to connectivity.
I have configured the router with the duoauthproxy server as the RADIUS server and see authentication packets being sent to the NPS by the duoauthproxy server, one Access-Request packet followed by 3 more duplicate requests but no responses.
These are the authentication method settings I’m using on the NPS:

Can anyone ■■■■ist? There are no firewalls involved in this setup as it’s in a lab. Both the Auth Proxy and NPS server have two network interfaces one internal to the VM network and one bridged interface out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 02:28 AM
I’m only allowed one image per post, so here is my packet capture:
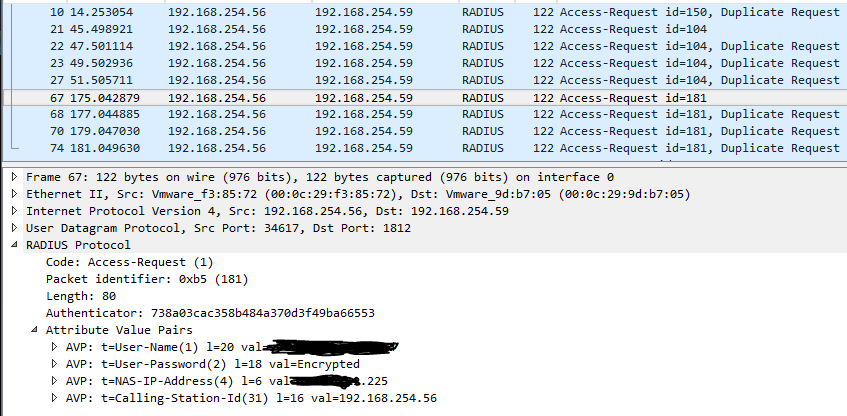
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 08:16 AM
NPS doesn’t support the Status-Server message, so the connectivity tool error you posted is expected.
It sounds like the Duo proxy is sending the requests, but NPS isn’t responding? Have you observed the access requests arriving at the NPS server? Is that packet capture image from the Duo authentication proxy server or NPS?
Did you add the Duo proxy server as a RADIUS client in NPS? If not, NPS might just be dropping the requests from the Duo proxy since it doesn’t recognize it as an authorized client.
Is any relevant information captured in the NPS logs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2019 04:34 AM
The packet capture is from the NPS box. While checking the RADIUS clients I’ve seen I didn’t have the DUO auth proxy box enabled. Nice catch.
This has got me a lot further, however when attempting to connect now with my DUO user I receive a prompt successfully on my mobile device, and hit “Approve” but receive the following error message in the console. (I have confirmed this account is unlocked and not disabled on the NPS/DC)
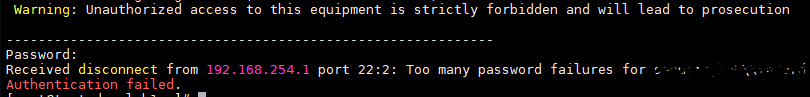
To ensure authentication succeeds we need to pass some vendor specific attributes (26th Vendor Specific Attribute needs to be configured as the username passed back to the router device) In our case the user is “NOC” - a default RADIUS response passes through the username “remote” as you can see from the error log below on the router there is a username of “remote” being passed back to the router and not the VSA as defined on the NPS of “NOC”
Feb 22 12:24:31.148 2019 ROUTERNAME.com sshd[615]: User remote is authenticated successfully but no logical login-id configured.
Feb 22 12:24:31.148 2019 ROUTERNAME.com sshd[613]: error: PAM: user account has expired for securitylab\vaderd from 192.168.254.56
Feb 22 12:24:31.148 2019 ROUTERNAME.com sshd: SSHD_LOGIN_FAILED: Login failed for user ‘securitylab\vaderd’ from host ‘192.168.254.56’
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2019 05:39 AM
Explore setting pass_through_all or pass_through_attr_names in your RADIUS client and server sections. Learn more about that option in the Authentication Proxy reference.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2019 03:09 AM
Thanks Kristina, you’ve been very helpful and I’ve now got a working proof of concept.
There’s just one more niggling issue, once a successful radius request has been made, DUO sends a push notification to the configured mobile device. But the ssh session times out very quickly (less than 10secs) and re-prompt’s you for a password. Once you’ve entered this password the whole process is broken and a 2nd push notification isn’t sent. This makes logging in difficult if you don’t have your phone open and unlocked on the desk at the time and totally ready to go
Is there any way to increase the timeout on the push notification? Or is this more a problem with the SSH prompt provided by the target device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2019 07:01 AM
The push timeout is already 60 seconds. That is likely why a second push isn’t sent, because the first one is still in flight and the Duo proxy may see the second RADIUS request as a duplicate of the first one and therefore doesn’t send another push. You could confirm this by looking a the debug log on your Duo proxy (it will identify duplicate requests).
Your best course of action is to increase the SSH login timeout or log in with an appended passcode instead of waiting to approve a Duo push request (append mode requires PAP).
If you are unable to do so, you could set the api_timeout artificially low, so the login request to Duo times out closer to the SSH timeout instead of waiting the default 60 seconds. I do not recommend this, because the likely outcome is that you’ll get spammed with MANY push requests.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide