- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Pleasant Password server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Pleasant Password server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 06:06 AM
Hello,
I would like to configure the Pleasant Password server for 2FA. On its site is described that it uses the RADIUS authentication. I have added the RADIUS App in our DUO Admin panel. Here is the configuration file:
[radius_client]
host=10.255.9.16
secret=**************
[radius_server_auto]
ikey=*******************
skey=******************
api_host=****************
radius_ip_1=10.255.9.13
radius_secret_1=***************
failmode=safe
client=radius_client
pass_through_all=true
allow_concat=true
port=1812
[main]
debug=true
10.255.9.16 is the Active Directory RADIUS
10.255.9.13 is the Pleasant Password server
I’m getting the following errors:
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] Packet dump - received from 10.255.9.13:
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] ‘\x01\xdf\x00?25\xbf\xc2\x10\xfb\xca\xdf\xe9\x1b\x9c\xb6\x1fQ\x1e\xfb\x01\x13USER\x04\x06\n\xff\t\x15\x02\x12\x88*B\xe4\xc1\xf0\x0f\t\xff.R\xb5$2\x87?’
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] Sending request from 10.255.9.13 to radius_server_auto
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] Received new request id 223 from (‘10.255.9.13’, 59705)
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] ((‘10.255.9.13’, 59705), 223): login attempt for username u’USER’
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] Sending request for user u’USER’ to (‘10.255.9.16’, 1812) with id 138
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] Packet dump - sent to 10.255.9.16:
2018-10-16T14:51:06+0200 [DuoForwardServer (UDP)] ‘\x01\x8a\x00?\x11\xc6F\xaf\xa0\x1fv\xd5\xdfj\x1f\xb3\xf4!\x92#\x01\x13USER\x02\x12%\xcd\x87\xe2\xd7a9\xe7z\x80c\xa7\xeb\xbf\xb2q\x04\x06\n\xff\t\x15’
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] Packet dump - received from 10.255.9.16:
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] ‘\x03\x8a\x00\x14jj\xd4\xf4\x11O@)x]M\xec\x83!\xb6\x97’
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] Got response for id 138 from (‘10.255.9.16’, 1812); code 3
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] ((‘10.255.9.13’, 59705), 223): Primary credentials rejected - No reply message in packet
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] ((‘10.255.9.13’, 59705), 223): Returning response code 3: AccessReject
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] ((‘10.255.9.13’, 59705), 223): Sending response
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] Packet dump - sent to 10.255.9.13:
2018-10-16T14:51:06+0200 [RadiusClient (UDP)] ‘\x03\xdf\x000v\xe1\xfa\x86\xd0\x06\xc0l\x9bX\xe2\xe6C\xcaM\xbe\x12\x1cNo reply message in packet’
Also I don’t see any logs related to the RADIUS App in the DUO Dashboard…
from the MS RADIUS server:
“10.255.9.16”,“IAS”,10/16/2018,14:55:18,1,“USER”,“DOMAIN\USER”,“10.255.9.21”,0,“10.255.9.21”,“DUO Proxy”,1,0,“311 1 10.255.9.16 08/21/2018 21:00:43 14714”,“Use Windows authentication for all users”,1,
“10.255.9.16”,“IAS”,10/16/2018,14:55:18,3,“DOMAIN\USER”,0,“10.255.9.21”,“DUO Proxy”,1,16,“311 1 10.255.9.16 08/21/2018 21:00:43 14714”,“Use Windows authentication for all users”,1,
from Pleasant Password server:
Invalid two-factor token Please try again
Thank you in advance!
- Labels:
-
Microsoft
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 07:59 AM
Hi!
Can I ask what authentication protocol you’ve set in Pleasant Password? Is it something other than PAP?
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 08:23 AM
It uses PAP now. Otherwise I get an error:
2018-10-16T14:41:41+0200 [DuoForwardServer (UDP)] ‘\x03J\x00,\x0ek\xe0\xfb\xf7\xfb5`\xc0\xef0\t\xdc*\x9dd\x12\x18Cannot decode password’
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 05:12 AM
Can I ask whether such scheme is actually supported?
Probably the Pleasant Password Server has to communicate to Duo directly without involvement of the Microsoft Radius? or it doesn’t matter?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 07:14 AM
We’ve tested all sorts of RADIUS integrations where the Duo Authentication proxy uses NPS as the upstream RADIUS authenticator, so that alone shouldn’t be an issue.
The RADIUS 2FA documentation page for Pleasant Password Server doesn’t indicate that you’re required to use RADIUS as the primary authenticator for the Duo proxy server. Did you already try this with [ad_client] pointing directly to your domain controller (as described at Two-Factor Authentication Using RADIUS | Duo Security)? I’d suggest you do give that a try, unless you’ve identified some compelling reason to use NPS for RADIUS auth in-between the Duo proxy server and AD.
If you must use NPS, ensure that both the NPS RADIUS client config for the Duo server AND the Pleasant Server RADIUS config are set to use PAP. Were you trying to log in with a concatenated password (e.g. password,123456)? Did you try just using the auto-push functionality, where you only enter the password and then receive an automatic Duo Push request on your phone?
If these suggestions don’t help, I’d suggest you contact Duo Support directly to open a case, or maybe Pleasant Password support, since their RADIUS page indicates they’ve tried it with Duo. They may have a better idea of the requirements on the Pleasant Password server side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 09:12 AM
Hello Kristina,
no, I didn’t try the AD authentication, because the Pleasant Server has users imported from AD and this is the primary authentication. I will try this. Thank you.
Is it possible to configure DUO without using a primary authentication? I mean the primary authentication is performed with Pleasant Server and then approves by Duo?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 09:55 AM
Yes, if Pleasant Password is already performing primary authentication then you can configure the Duo proxy to only perform secondary authentication via RADIUS with the [duo_only_client]configuration described at Duo Authentication Proxy Reference | Duo Security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2018 02:04 AM
Is it correct config?
[duo_only_client]
[radius_server_auto]
ikey=***********
skey=**************
api_host=*********
radius_ip_1=10.255.9.13
radius_secret_1=123456
failmode=safe
client=radius_client
pass_through_all=true
allow_concat=true
port=1812[main]
debug=true
with such config I can’t start the Duo Proxy service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2018 09:03 AM
No, that is not correct. The [radius_server_auto] section should include client=duo_only_client. You still have it using the radius_client that you removed from the config.
You might want to read through all the options for RADIUS Auto at Duo Authentication Proxy Reference | Duo Security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2018 09:34 AM
Thank you so much, Kristina!
Now it works but after entering my password I had to type the Token and then approve the Duo Push… it is ok? Can I use Token only? Actually, it is not a problem, but…
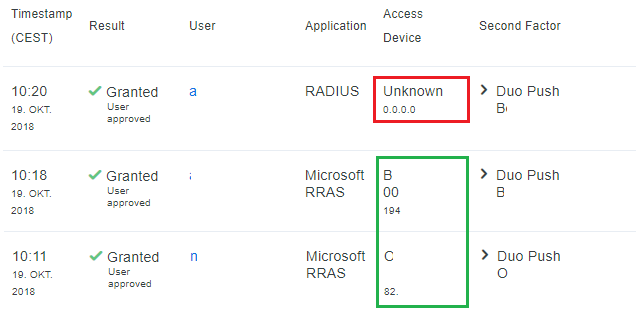
Also, I don’t see the remote IP…
2018-10-18T18:25:05+0200 [DuoForwardServer (UDP)] Packet dump - received from 10.255.9.13:
2018-10-18T18:25:05+0200 [DuoForwardServer (UDP)] ‘\x01\x05\x00?\xad\xf7\xf8\x93\x157:\xa8Cn\xadGh\x9a\x12\xdc\x01\x13USER\x04\x06\n\xff\t\x15\x02\x12\x8e\xe2\xceCZ\x97)\x1a"a\xd5\x97\x06\xe
0;k’
2018-10-18T18:25:05+0200 [DuoForwardServer (UDP)] Sending request from 10.255.9.13 to radius_server_auto
2018-10-18T18:25:05+0200 [DuoForwardServer (UDP)] Received new request id 5 from (‘10.255.9.13’, 59914)
2018-10-18T18:25:05+0200 [DuoForwardServer (UDP)] ((‘10.255.9.13’, 59914), 5): login attempt for username u’USER’
2018-10-18T18:25:05+0200 [DuoForwardServer (UDP)] http POST to https://XXXXXX.duosecurity.com:443/rest/v1/preauth: user=USER
2018-10-18T18:25:05+0200 [duoauthproxy.lib.http._■■■■#info] Starting factory <_■■■■: https://XXXXXX.duosecurity.com:443/rest/v1/preauth>
2018-10-18T18:25:05+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] ((‘10.255.9.13’, 59914), 5): Got preauth result for: u’auth’
2018-10-18T18:25:05+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] Invalid ip. Ip was None
2018-10-18T18:25:05+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] http POST to https://XXXXXX.duosecurity.com:443/rest/v1/auth: auto=push1&factor=auto&ipaddr=0.0.0.0&user=USER
2018-10-18T18:25:05+0200 [duoauthproxy.lib.http._■■■■#info] Starting factory <_■■■■: https://XXXXXX.duosecurity.com:443/rest/v1/auth>
2018-10-18T18:25:05+0200 [duoauthproxy.lib.http._■■■■#info] Stopping factory <_■■■■: https://XXXXXX.duosecurity.com:443/rest/v1/preauth>
2018-10-18T18:25:08+0200 [DuoForwardServer (UDP)] Packet dump - received from 10.255.9.13:
2018-10-18T18:25:08+0200 [DuoForwardServer (UDP)] ‘\x01\x05\x00?\xad\xf7\xf8\x93\x157:\xa8Cn\xadGh\x9a\x12\xdc\x01\x13USER\x04\x06\n\xff\t\x15\x02\x12\x8e\xe2\xceCZ\x97)\x1a"a\xd5\x97\x06\xe
0;k’
2018-10-18T18:25:08+0200 [DuoForwardServer (UDP)] Sending request from 10.255.9.13 to radius_server_auto
2018-10-18T18:25:08+0200 [DuoForwardServer (UDP)] ((‘10.255.9.13’, 59914), 5): Received duplicate request
2018-10-18T18:25:09+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] ((‘10.255.9.13’, 59914), 5): Duo authentication returned ‘allow’: ‘Success. Logging you in…’
2018-10-18T18:25:09+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] ((‘10.255.9.13’, 59914), 5): Returning response code 2: AccessAccept
2018-10-18T18:25:09+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] ((‘10.255.9.13’, 59914), 5): Sending response
2018-10-18T18:25:09+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] Packet dump - sent to 10.255.9.13:
2018-10-18T18:25:09+0200 [HTTPPageGetter (TLSMemoryBIOProtocol),client] ‘\x02\x05\x000T7I\n\xedb\xa8<\x9bB+\x11j\x950\\x12\x1cSuccess. Logging you in…’
2018-10-18T18:25:09+0200 [duoauthproxy.lib.http._■■■■#info] Stopping factory <_■■■■: https://XXXXXX.duosecurity.com:443/rest/v1/auth>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-18-2018 10:06 AM
The log you shared doesn’t show that a token passcode was received at the Duo proxy during authentication. Does Pleasant Password have separate password and token fields in the client UI? If I understand your setup correctly, you should need to provide two “passwords” when logging in: one for primary authentication, which is sent directly to AD, and one for 2FA, which should be sent to the Duo RADIUS server and can be a numeric OTP code from a token or the name of a Duo factor (e.g. push or phone). That you received an automatic push sounds like no second password (in the form of the OTP code) was sent to Duo. You may need to review your login policies to ensure that the right information is sent to Duo.
If Pleasant Password does not send the client IP address in the RADIUS packet as the calling-station-id then no client IP will get reported to Duo. You will need to verify this with Pleasant Password.
I encourage you to open a case with Duo Support if you need more 1:1 assistance. This forum is not a substitute for support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2018 01:34 AM
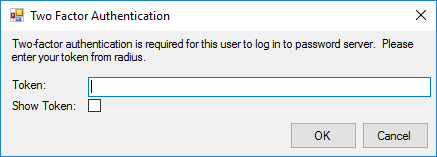
Yes, firstly I provide my password and then the Password Manager Client asks me for the token:
Having entered the token I get Duo Push notification. If I don’t enter the Token - I don’t get any DUO Push notification and I can’t log in.
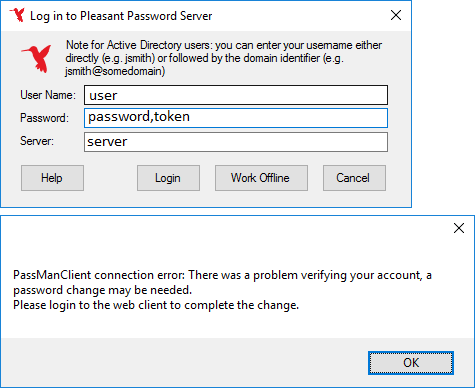
If I try to enter “password,token” as described in the DUO Documentation I get the error:
I meant this IP. I thought it is client independent. The DUO just monitors where the request came from. Doesn’t it? (Microsoft RRAS is configured on an another DUO Proxy server and is used for a VPN)
Yes, i will open a case too. Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-25-2018 07:38 AM
Hello,
accidentally I have known that the window with the Token request is useless. You can type there anything you want even wrong characters. The real 2FA goes via Push Notification only.
Thank you for your help!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide