- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Need a help with Palo Alto Networks Global Protect configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Need a help with Palo Alto Networks Global Protect configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-12-2022 12:18 PM
Hi.
Guys, I stuck during configuration of PANW GP with SAML IdP usage.
I created support tickets however Duo Support doesn’t response and PANW Support researches an issue for a month ![]()
But to the point: I configured PANW GP portal and Duo SSO with Authentication Proxy running one of our AD server.
Everything (almost) exactly as it is written in manual (Duo Single Sign-On for Palo Alto GlobalProtect | Duo Security). “Almost” because on very beginning I do not use Certificate for Signing Request in GP Portal’s Authentication Profile (honestly speaking I am not sure what are requirements for this cert) however I do not think it is necessary (right now).
My test users is properly authenticated with Duo push/SMS/whatever.
I see it in Authentication Proxy logs:
{“timestamp”: “2022-01-01T14:05:57.934594Z”, “msg”: “Successful authentication against server”, “event_type”: “ldap_query”, “query_type”: “Primary authentication”, “status”: “succeeded”, “server”:…
- and PANW system logs:
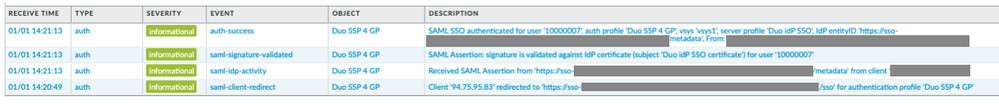
The issue is, that just after authentication my GP agent shows You are not authorized to connect to GlobalProtect Portal ![]()
Uncle Google has found in PANW resources that such message is mostly caused if user does not belong to proper AD group… But he belongs, he was authenticated ![]()
I started to dig and I have found these:
- in PANW GP log entries with error:
Failed to get client configuration
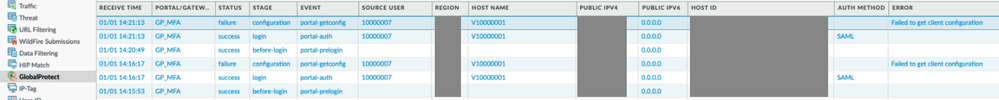
- in PANW authd.log:
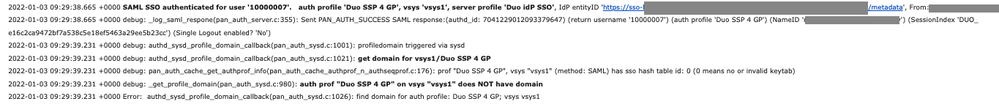
So, IMHO even if user authenticates correctly, for some reasons a domain (I hope it is about AD domain) is not known (how could it be if full DN is visible in Authentication Proxy logs?) ![]() and it makes impossible to match username with AD group bound to configuration created for GP agent (at GP portal).
and it makes impossible to match username with AD group bound to configuration created for GP agent (at GP portal).
User belongs to this group for sure because on same device I have another GP portal which uses exactly same configuration (GP agent, group, user) however without Duo authentication (AD only) and it works correctly…
So, I started to think that maybe it is something about attributes provided by Duo to PANW. Maybe it should be domain/10000007 and not bare 10000007 ?
A few minutes ago I made simple test: using exactly same username I logged in to AD authenticated GP portal then tried to do same to Duo authenticated one.
And you know what? It seems I was right:
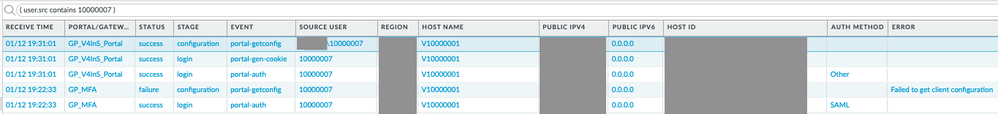
(GP_MFA is Duo authenticated GP Portal name)
Guys, does anybody know how to force Duo to provide this additional domain\ string?
I guessed it is about configuration of attributes passed by Duo to PANW directly. So, I thought I have to change configuration of Duo SSO especially section Duo username attributes but IMHO it is wrong approach regarding to Duo Single Sign-On | Duo Security :
Duo username attribute (Optional)
The email address that users type in during SSO login will be matched to the user in Duo. If your Duo usernames do not match the email address value(s) for your specified Email attributes, you enable the Specify Duo username attribute option and type in the name of an Active Directory attribute that does contain the values that match your Duo usernames.Example: Your users have email addresses in AD with the format
norben.arroway@example.com, but your Duo usernames are thesAMAccountNamevalues with the formatnarroway. AddsAMAccountNameas a Duo username attribute.Default: No alternate username attribute; send email address as Duo username.
…and I ran out of ideas… Maybe there is a way to add some parameters in Authentication Proxy configuration to add domain\ ?
Guys, talking that “I am a bit frustrated” about this case is… hmmmmm… let’s say: not enough…
![]()
![]()
![]()
![]()
Anybody can help me?
thx in adv…
- Labels:
-
VPN
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide