- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Inline password reset for RRAS VPN, need clarifications
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2022 07:58 AM
Hi,
Preparing to deploy DUO MFA for a remote access VPN (SSTP) based on MS RRAS.
Going to install DUO Authentication Proxy on the RRAS VPN server (member of our AD domain), primary authentication method will be Active Directory, planning authentication between the Proxy and AD to be SSPI.
I have read a lot of documentation and it’s still not clear to me, in the above conditions, when DUO Authentication Proxy is going to be a domain joined server and the authentication protocol to be SSPI, is anything else required to be configured to support expired domain accounts’ passwords change during the VPN connection to RRAS server?
Thank you.
Solved! Go to Solution.
- Labels:
-
Microsoft
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 08:50 AM
Password reset via the Authentication Proxy is not supported over RADIUS with LDAP primary authentication. Your proposed configuration will not allow password reset for RRAS connections.
Please read this help article to learn your options: https://help.duo.com/s/article/5797
Also review some potential issues you may experience if you choose to install the Duo proxy on your RRAS server (not recommended): https://help.duo.com/s/article/2970
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 08:50 AM
Password reset via the Authentication Proxy is not supported over RADIUS with LDAP primary authentication. Your proposed configuration will not allow password reset for RRAS connections.
Please read this help article to learn your options: https://help.duo.com/s/article/5797
Also review some potential issues you may experience if you choose to install the Duo proxy on your RRAS server (not recommended): https://help.duo.com/s/article/2970
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 09:23 AM
Hello DuoKristina,
According to the article 5797:
Both the server and client sections in the Duo Authentication Proxy configuration file will need to use certificates.
To support password resets while using ldap_server_auto, the connection between the Authentication Proxy and the domain controller must use LDAPS or STARTTLS.
So it’s not clear for me, why do you say it’s not supported for LDAP configuration.
Concerning proxy installation on a dedicated server, ok, I will plan a separate server for that to avoid problems.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 09:53 AM
The Duo Authentication Proxy supports inline password reset when it is configured with both primary and secondary LDAP or both primary and secondary RADIUS (using MS-CHAPv2). This is described in the first KB article I linked (5797).
The RRAS configuration documented here is using LDAP for primary and RADIUS for secondary. This configuration does not support inline password reset.
You mentioned using SSPI for the Duo proxy to perform primary authentication. That means configuring LDAP for primary authentication. I am not aware of a way you can add an external LDAP server for authentication to RRAS, which would exclude an LDAP + LDAP deployment.
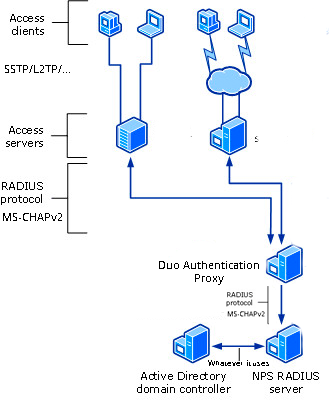
Therefore the option left would be RADIUS + RADIUS. Some customers achieve this for RRAS by having RRAS point to the Duo Authentication Proxy using RADIUS, and then point the Duo proxy to an NPS server in the domain to perform RADIUS primary authentication against Active Directory. Such a deployment is described in this article which is linked from article 5797.
Is capable of password reset:
ad_client + ldap_server_auto (often the authenticating device requires requires SSL)
radius_client + radius_server_*nnn* (requires MS-CHAPv2 all the way through)
Is not capable of password reset:
ad_client + radius_server_*nnn*
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 10:18 AM
Sorry, I don’t understand, in which case is then LDAP + LDAP possible?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 10:24 AM
The case where you are not trying to protect RRAS, but you had something else that supported external LDAP authentication. ![]()
For RRAS the only possibility (unless you are aware of a way to add an external LDAP directory for RRAS authentication) is RADIUS + RADIUS, with MS-CHAPv2 all the way through, probably via NPS.
ETA: this article might help you too https://help.duo.com/s/article/3687
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 10:29 AM
It seems I can’t get the whole schema. At minimum in my case we have VPN client - RRAS - DUO Auth Proxy - AD DC.
At which section which protocol should be used to allow password reset?
As I understand, between [VPN client - RRAS server] it should be either PAP or MS-CHAP v2. And for the latter a few additional restrictions apply, so PAP is preferred.
Thus LDAP-LDAP means sections RRAS to DUO AP and DUO AP to AD DC. Right?
Are you saying, that RRAS to DUO AP can’t be LDAP (without additional RADIUS servers)? So with the minimalistic schema for password reset support you must use RADIUS-RADIUS and MS-CHAPv2 with it’s restrictions?
That’s pretty disappointing, I was hoping it’s possible to support password reset while keeping the deployment simple. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 10:33 AM
RRAS has some limitations, and the Duo Authentication Proxy has some limitations, and unfortunately in this use case the limitations do not mesh.
Yes, exactly.
VPN solutions from other vendors provide more flexibility with external authentication servers - supporting more protocols, options to chain different primary and secondary authentication servers, etc. - but RRAS, as a Windows Server product, is optimized for that environment (which one would reasonably expect).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 11:05 AM
So it’s going to be:
VPN client - {MS-CHAPv2} - RRAS - {RADIUS + MS-CHAPv2} - DUO AP - {RADIUS + MS-CHAPv2} - NPS - {LDAP + NTLMv2} - AD DC
Is that correct? Additional RADIUS server should be used here as well?
Also with RADIUS protocol in both places, which authentication protocol should be used, PAP or MS-CHAPv2 everywhere?
The alternative is:
VPN client - {PAP} - RRAS - {LDAP + NTLMv2} - DUO AP as a transit - {RADIUS ? + ?} - NPS - {LDAP + NTLMv2} - AD DC
Is that correct?
I read all the articles you referenced and many more, have a mess in my head. I want to get principal schemas of the two possible options (as I understand there are just two options for RRAS with expired password change support), then decide which one to use or just drop it and deploy the simplest option without password change support. But honestly, I can’t imagine how people can live without it, users never change passwords in time, even with two weeks prior notice every time they sign into their machines. Then you will end up with a lot of stuck users and necessity to reset their passwords…
Thank you. Please help me to get the principal schema and used protocols in each section.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2022 11:18 AM
hastily edited image from Network Policy Server (NPS) | Microsoft Docs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2022 01:15 AM
So for MS-CHAPv2 (RADIUS+RADIUS) option the schema is close to what I expected. Much clearer now, thank you.
The only thing is you did not say which authentication protocol should be used between the VPN client and RRAS server in that case, MS-CHAPv2?
Can you provide similar schema for the PAP, i.e. LDAP+LDAP option (with password reset support) please?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2022 01:25 AM
I have a couple of other questions:
-
I saw, that it’s explained that for SSTP and L2TP over IPSec VPN options PAP is still secure, because a protected encrypted tunnel is established first and only then credentials are transferred. Is that true for RRAS based SSTP and L2TP over IPSec VPNs?
And is that true for IKE v2 RRAS based VPN or not? -
Is it anyhow possible to deploy DUO with password reset support in RADIUS+RADIUS and\or LDAP+LDAP options, but using just a single Windows server for RRAS, DUO AP and NPS? I know it’s not recommended, but deploying two additional Windows servers is costly, it would be good if we can install RRAS\DUO AP\NPS on a single machine. Can’t it be achieved by using differentiating port numbers and NPS policies?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2022 04:04 AM
Reading more and more, I finally realized, that LDAP+LDAP option is not possible with RRAS at all and that’s what you were saying before ![]() , I was not able to understand, because I did not have a clear schema of all connections.
, I was not able to understand, because I did not have a clear schema of all connections.
As I understand now, LDAP+LDAP is not possible because in that case RRAS - DUO AP communication should use LDAP (not only DUO AP - AD DC should use LDAP, which is not a problem) and as RRAS is not possible to configure to use any other LDAP server except AD DC, that’s not possible. Is everything correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2022 10:15 AM
Another question,
Note that the RRAS clients should still use PAP authentication. Passwords and usernames will still be sent over an encrypted channel via L2TP or SSTP as long as you have this configured (https://duo.com/docs/rras#modify-vpn-client-access). When conf...
It’s not clear, if the two sentences are connected to each other. Can we still use MS-CHAPv2 on the VPN client?
If we use PAP authentication on the VPN client, but RADIUS-RADIUS with MS-CHAPv2 between RRAS and DUO AP & DUO-AP and NPS server, will append mode work?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2022 11:03 AM
Can we still use MS-CHAPv2 on the VPN client?
Are you using MS-CHAPv2 now? If you are you shouldn’t need to change that, but if you aren’t you don’t have to.
LDAP+LDAP is not possible
Correct. It is not possible for anything that doesn’t support external LDAP authentication (as in, not directly against the domain controller).
If we use PAP authentication on the VPN client, but RADIUS-RADIUS with MS-CHAPv2 between RRAS and DUO AP & DUO-AP and NPS server, will append mode work?
MS-CHAPv2 and append mode are mutually exclusive on the Duo Authentication Proxy in all scenarios, so no.
If you have further questions please contact Duo Support. This has gone well beyond a typical community post.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide