- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Firewall ports to open so secure duo works correctly?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2018 10:43 AM
Hello !
I am new to the solution. I need to secure 4 servers, those servers have no access to the internet whatsoever. I need the solution to work, what is the bare minimum I need to open on my firewall so the solution works correctly ? the servers are allowed to talk only to the internet for this solution to work only.
Thank you ![]()
Guillaume
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 06:48 AM
Hey there!
We have a public knowledge base at https://help.duo.com that has answers to frequently asked questions like this one.
The article reiterates that we may change the IP ranges at any time, so to avoid disruption it is better to permit traffic using Duo API hostname FQDN if your firewall has that option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 11:27 AM
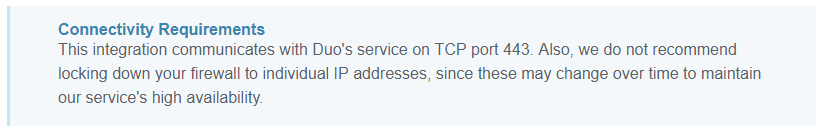
You should only need https (tcp port 443) open outbound to 0.0.0.0/0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 11:52 AM
I figured out the TCP 443 part. But I created the ACL toward the single IP of my API.
Instead of 0.0.0.0/0
Do you have a /16 or /24 I could restrain the destination ? Your API are maybe all on the same public subnet ? I will be challenge internally for opening 443 to 0.0.0.0./0
Thank you for your reply. I understand I’m using the free version because I only need 7 account secured, but I would pay for this fantastic solution if you would tell me to.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2018 01:10 PM
that’s a question for Duo support if they have ranges you can lock down to. My guess is they don’t have ranges or static IPs which is why they are telling you to open to 0.0.0.0/0.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2018 06:48 AM
Hey there!
We have a public knowledge base at https://help.duo.com that has answers to frequently asked questions like this one.
The article reiterates that we may change the IP ranges at any time, so to avoid disruption it is better to permit traffic using Duo API hostname FQDN if your firewall has that option.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2021 05:38 AM
This document needs to be updated as there are missing IPs. I had to add this humongous subnet (40.126.x.x) to get it to work. I guess I could spend the day watching WireShark for the exact IP’s but I would rather you guys tell me. Is it possible to get this document updated?
https://help.duo.com/s/article/1337?language=en_US
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2021 05:55 AM
I’ll pass that feedback on, but keep in mind that as we expand our operations globally and add more capacity in areas where we already host services it is more likely that the IPs could change at any time.
Using the API hostname in outbound rules is a flexible and recommended solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-22-2021 06:09 AM
Unfortunately, my firewall can’t use an API hostname only IP addresses.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2021 08:50 AM
Hi @twalker
What feature are you trying to connect to? Our internal team confirmed that the help article seems to be complete based on the information we have. As it says, however, Duo only has IP ranges for the MFA API. If you are trying to connect to something like the Duo Admin Panel or SSO, then it’s expected that the IP will not be listed in that article. We have a feature request to implement stable IP ranges for that, which we can add you to if you’d like. Anyone else reading who is interested can request to be added by contacting Duo Support or your Customer Success Manager or Account Executive if you know who that is. That’s one of the most common reasons people encounter this issue of IPs not being listed.
The other common reason you might run into this is if you have a configuration that causes traffic to go somewhere else instead of the Duo MFA API, like a proxy or perhaps a typo in the configuration. This is something you will need to work with Duo Support on, as we don’t do advanced troubleshooting of configurations here in the Community.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2021 10:17 AM
No, just trying to login to a server using multi-factor. If I don’t put in the 40.126.x.x range I never get the DUO Security screen for the Push, Call Me or Passcode. It just times out. We don’t use a proxy. I have a ticket open with Support, but they have been giving me the run around for weeks now. Support ticket 00775986
I have captured the following IPs in the logs when I don’t have the 40.126.x.x range in my firewall whitelist. I’m sure there are more. I just hate leaving such a huge subnet open like that. It has to be 40.126.0.0/19 for it to work until I can get the exact IPs. (Plus the one’s in the doc of course).
40.126.28.20
40.126.28.19
40.126.7.35
40.126.7.32
40.126.24.146
40.126.28.11
Thanks for trying.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2021 10:37 AM
The internet tells me that the 40.126.0.0 block is owned by Microsoft. Are you by any chance using an Azure integration?
Edited to add this Microsoft KB article that shows 40.126 in their ranges: Office 365 URLs and IP address ranges - Microsoft 365 Enterprise | Microsoft Docs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2021 10:57 AM
Our ADFS lives there. Interesting. But, I thought DUO did a directory sync of our AD creds to authenticate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2021 11:18 AM
Duo does not sync any credentials. Duo does not store any primary password information. Duo Active Directory sync creates users in Duo using information from AD, but the sync does not include actual credential information.
If your AD FS is in Azure and you installed Duo for AD FS on it, it makes sense that you would need to permit access to the Azure ranges for login to work. But, none of Duo’s cloud services as covered by Duo’s article 1337 exist in that Microsoft-owned subnet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2021 11:13 AM
I checked and our ADFS Azure IP doesn’t match anything in the 40.126.0.0/19 subnet, so it’s not us. Do you guys have servers at Azure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2021 11:19 AM
I think our replies crossed. Are you using Office 365? Do you have clients that contact Office 365 services that slo now log in through a Duo-protected application?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
