- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Duo SSO with multiple Salesforce instances
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2021 08:51 AM
Hello Duo team,
We are looking into Duo-hosted SSO for our Salesforce instances. The “basic” integration works perfectly but we are facing to an issue with username: as we have multiple Salesforce instances (production, sandboxes, etc…), we have multiple username. For example:
- agallez@cameoglobal.com > Production Salesforce
- agallez.mfa@cameoglobal.com > MFA sandbox
- …
I tried to use aliases in Duo but it does not work. Do you have an idea on how I could go forward?
We use have a sync with our AD (on-prem) done with Duo AuthC proxies.
Thank you.
Regards,
Antony Gallez
Solved! Go to Solution.
- Labels:
-
Cloud
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2021 05:11 AM
Hi @antony.gallez,
I think for the custom Mail attribute on the Salesforce page in the Duo Admin Panel you’ll want to put just description not <Description>. description is the name of the attribute in Active DIrectory. Once you’ve updated the value click Save at the bottom of the screen and try to do another authentication to Salesforce.
The <Words> are just our bridge attributes that you can select from the dropdown so that we automatically would map certain attributes if you switched between using Active Directory and a SAML IdP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2021 04:32 PM
Hi @antony.gallez!
Do you have the two different email addresses as attributes in your authentication source? Username aliasing only impacts the usernames that are used when trying to do Duo authentications but are not the values sent to Salesforce.
Ideally you’d have an attribute in your authentication that matches “agallez@cameoglobal.com” and another that matches agallez.mfa@cameoglobal.com. You’d then map the appropriate attribute as your Mail attribute for each Salesforce application in the Duo Admin Panel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2021 01:26 AM
Hi @jamie,
Thank you for your reply.
We have different email addresses between the instances but also different usernames.
I do not get waht you meant with the mapping of attributes. I tried to add the username as alias in the user but it did not work.
Regards,
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2021 05:50 AM
Could you show me what error you’re hitting? Just want to make sure I understand where you’re running into problems.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2021 07:21 AM
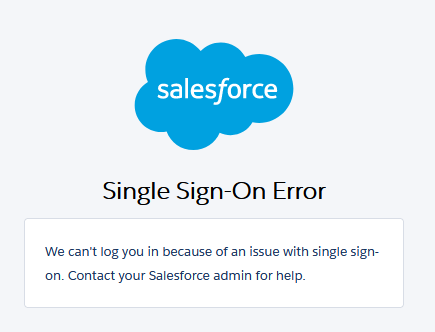
Sure, please find some screenshots below.
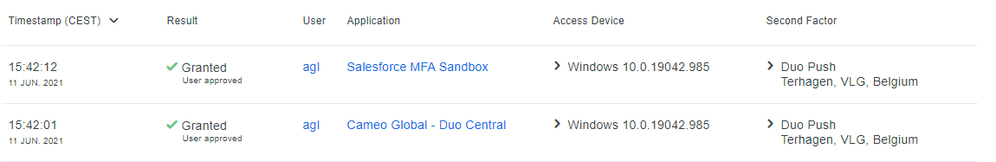
AuthC logs from Duo admin
Error when I am authenticated through SSO
Config of the Duo user
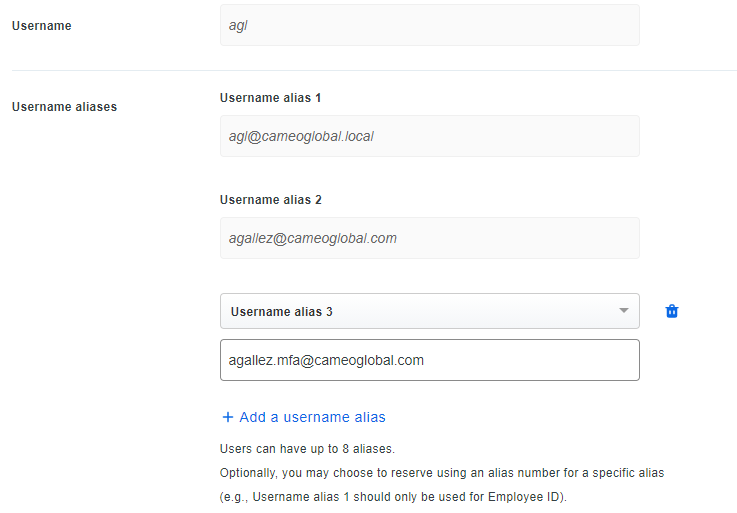
As you may see here, I added an alias matching the SF username but still, it does not work.
Config in SF
On this one, if I change the Username to my email address, SSO works fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2021 11:09 AM
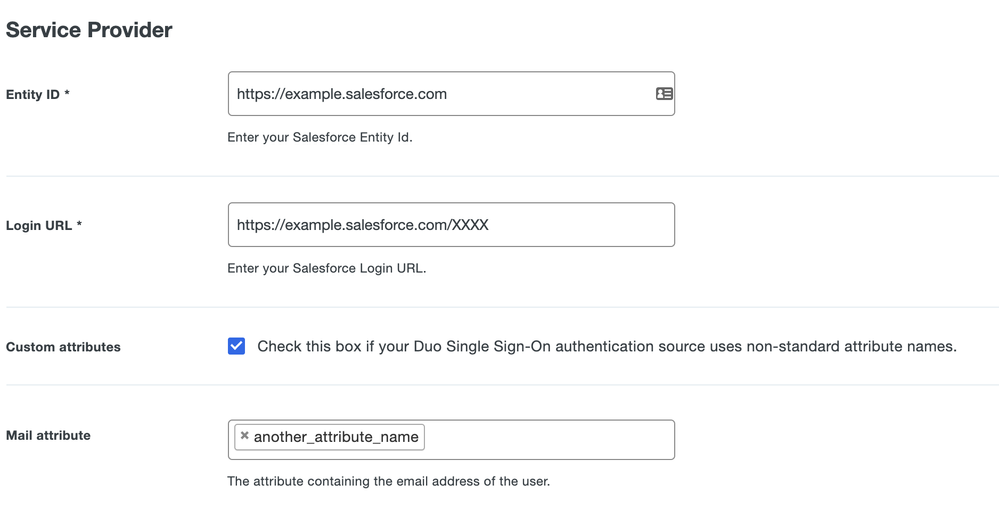
So your username and aliases in the Duo Admin Panel only impact what usernames we recognize when doing things like Duo 2FA. The value that is being sent to Salesforce is the attribute that in your Authentication Source
If you go to your Salesforce application in the Duo Admin Panel under the “Service Providers” section you should see a checkbox next to Custom attributes. Here you can specify a different authentication source attribute to send to Salesforce when authentication. By default we use mail for Active Directory and Emailfor SAML IdPs.
If you have an attribute in your authentication source that matches your different logins you can specify it there per Salesforce application.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2021 01:13 AM
Hi @jamie,
Ok. Sorry for my mistake on the alias, now I got it clear.
I’ll look at this and let you know the outcome.
Regards,
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2021 10:52 PM
Hi @jamie,
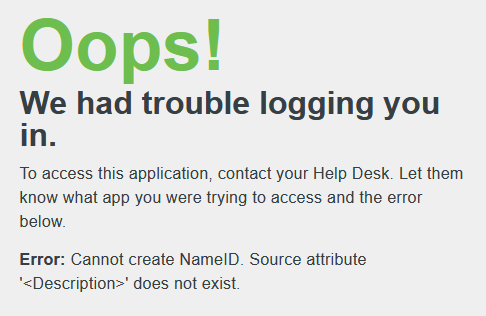
I made a test with the field Description (quick test before altering our AD schema) in our AD but I get an error when I click on the tile in SSO portal:
I looked in our AD sync configuration but I can’t find any settings to import the field description. I also read the docs but same result.
Is it restricted to custom attributes? Or am I using a wrong attribute name?
Regards,
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2021 05:11 AM
Hi @antony.gallez,
I think for the custom Mail attribute on the Salesforce page in the Duo Admin Panel you’ll want to put just description not <Description>. description is the name of the attribute in Active DIrectory. Once you’ve updated the value click Save at the bottom of the screen and try to do another authentication to Salesforce.
The <Words> are just our bridge attributes that you can select from the dropdown so that we automatically would map certain attributes if you switched between using Active Directory and a SAML IdP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-14-2021 06:04 AM
Hi @jamie,
Ok. Got your loud & clear on the bridge attributes.
All is working fine. Thanks a lot for your help!
Regards,
Antony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2023 02:49 AM
To configure Duo Single Sign-On (SSO) with multiple Salesforce instances to 360degreecloud, you would need to follow these general steps:
-
Set up Duo SSO: Firstly, you’ll need to set up Duo SSO for your Salesforce instances. This involves configuring Duo as the identity provider (IdP) and configuring Salesforce as the service provider (SP) in Duo’s admin panel. You’ll generate the necessary SAML metadata and configure the required settings, such as assertion consumer service URL, audience URI, and ACS URL.
-
Configure Salesforce as the SP: In each Salesforce instance, you need to configure it as the SP to accept SAML assertions from Duo. This involves setting up a connected app in Salesforce, specifying the ACS URL, entity ID, and other SAML-related settings. You’ll need to repeat this step for each Salesforce instance you want to integrate with 360degreecloud.
-
Configure 360degreecloud as the IdP: Once Duo SSO is set up in Duo’s admin panel and Salesforce instances are configured as SPs, you’ll need to configure 360degreecloud as the IdP. The specific steps for this will depend on the requirements and configuration options provided by 360degreecloud. You’ll need to provide the SAML metadata generated by Duo, including the entity ID, ACS URL, and certificate.
-
Test the SSO integration: After completing the configuration steps, it’s important to thoroughly test the SSO integration. Verify that users can log in to 360degreecloud by accessing the Salesforce instances, and ensure that the SSO flow is working correctly. Test scenarios such as initiating SSO from 360degreecloud to Salesforce and verifying that the user is logged in seamlessly.
please visit site: https://360degreecloud.com/
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide