- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- Duo Release Notes for September 28, 2018
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 09-28-2018 06:18 AM
Hello everyone! Here are the release notes for the most recent updates we’ve made to Duo.
You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
New features, enhancements, and other improvements
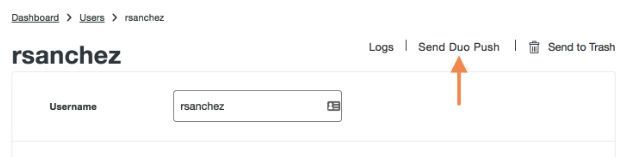
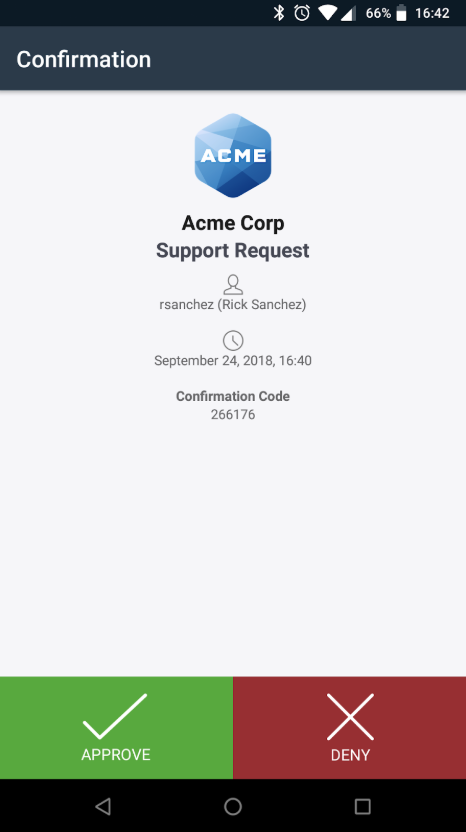
- You can now verify the identity of an end user by sending them a Duo Push request via their User page in the Duo Admin Panel.
- A help desk push displays text that indicates it is a help desk request, including a confirmation code. When the user approves the push, the Duo Administrator will see that in the Duo Admin Panel.
- See help desk push in action in this video.
Updates to Trusted Endpoints Manual Enrollment
- Trusted Endpoints Manual Enrollment has been expanded and simplified. Each supported software has its own tab on the Manual Enrollment configuration page.
- To enable a software the integration must be active and the specific software must be enabled. If you enable a specific software but the integration isn’t active, you will be prompted to activate it.
- It is no longer necessary to create a dummy integration for certificates to function properly on iOS devices. Simply follow the instructions on the iOS tab.
New and updated applications
- CentOS 5 support is deprecated and will be removed in the next release.
- Fixed a bug that caused a segfault on systems on which the hostname wasn’t retrievable.
- FORM challenge method now supports the request_id parameter.
Duo Network Gateway 1.4.0 released
- Added the ability to configure Duo Network Gateway without having to use the Admin UI. Read more at Scripted Configuration for Duo Network Gateway.
- Fixed Let’s Encrypt bug that would cause Duo Network Gateway to not renew certificates.
Duo Authentication Proxy 2.10.1 released
- Corrected an installation issue on Linux systems.
Bug fixes
- The Duo Admin Panel dashboard no longer displays “up to date” endpoints, in order to improve clarity.
- The “out of date” and percent change values under “Endpoints” in the Duo Admin Panel dashboard now only apply to OSes.
- Numerous fixes for our Azure Active Directory integration:
- The Directory name field now properly shows the field label and help text in read-only mode.
- The Enrollment email, Import phones, and Normalize usernames fields now display their values in the correct format in read-only mode.
- Fixed a bug where group OIDs were displayed instead of group names when viewing the Azure AD Sync page in read-only mode.
- Fixed a bug with the Users page in the Duo Admin Panel whereby the table could get too wide if the data displayed was sufficiently wide. The data is now truncated if necessary.
- Fixed a bug on the Settings page in the Duo Admin Panel that prevented specifying a minimum password length greater than 12.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I love the helpdesk push verification function. Can someone explain the utility or benefit of the confirmation code?
The code appears to be generated for that interaction and not actually tied to a code available through the user’s app anywhere else. If someone is able to get the push notification, they should be able to hit the approve button.
My users typically use the code for MFA when they are in a location where they don’t have cell phone connectivity. If this is to be used for verification when calling in for support (from a landline for example) the confirmation code doesn’t seem to add any benefit since they wouldn’t be able to get the push anyway when they’re in a no wireless dead zone.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @DZag
A Duo admin can use the confirmation code to establish that it is a legitimate push initiated by that admin, and not just some spurious auth request.
If a user doesn’t have the connectivity to receive a push or is calling about an issue receiving pushes on their device, simply fall back to your already established verification questions.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: