- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- Duo Release Notes for October 13, 2017
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-13-2017 07:42 AM
Hello everyone! Here are the release notes for the most recent updates we’ve made to Duo.
You can subscribe to notifications for new release notes by following the process described here.
Features, enhancements, and other improvements
SSO in Duo MFA
- Single Sign-On with the Duo Access Gateway (DAG) is now available to Duo MFA edition customers.
- You can use the DAG/SSO Launcher to collect your applications on a single portal.
- Apply a shared Remembered Devices policy to your web applications to provide an SSO experience.
- This policy, along with other policies available to Duo MFA customers, can be configured using the Policy Engine. This is accessed via the Policies section of the Duo Admin Panel.
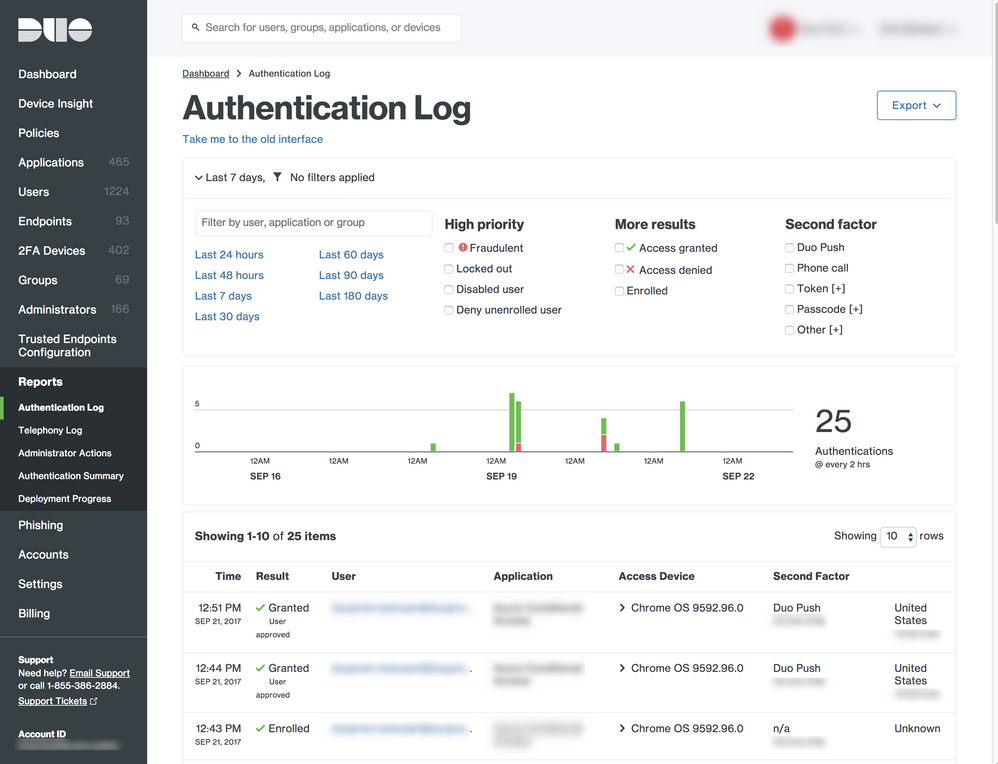
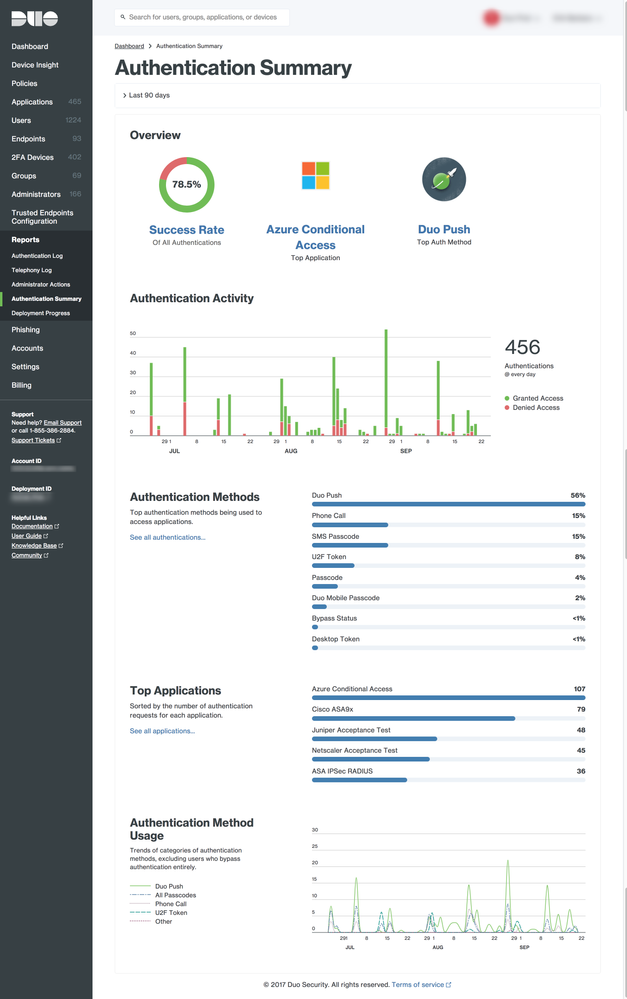
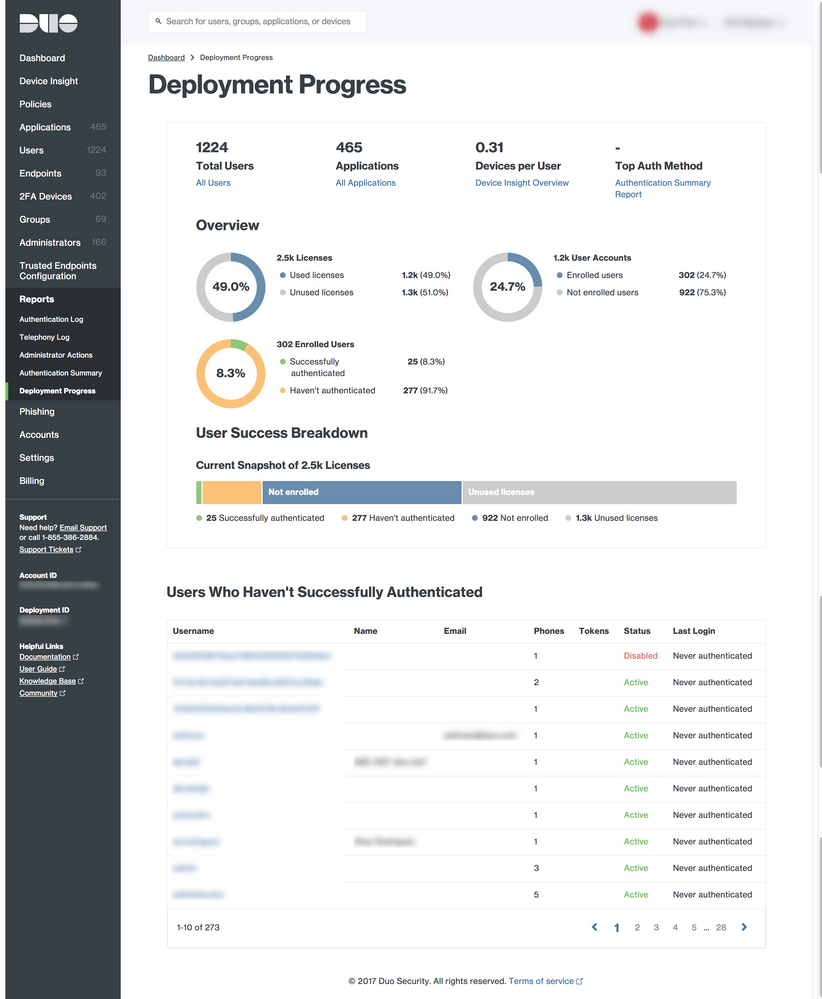
Improved Reports in the Duo Admin Panel
- You can now download reports and logs with filtered results based on what you select in the Admin Panel.
- We’ve implemented a new Authentication Log UI that features context and time-based filtering.
- Added an Authentication Summary report. This report helps you answer the question “Are my users successfully using Duo?”
- Added a Deployment Progress report. This report helps you answer the question “What is my deployment’s health?”
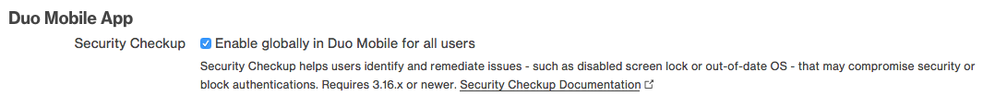
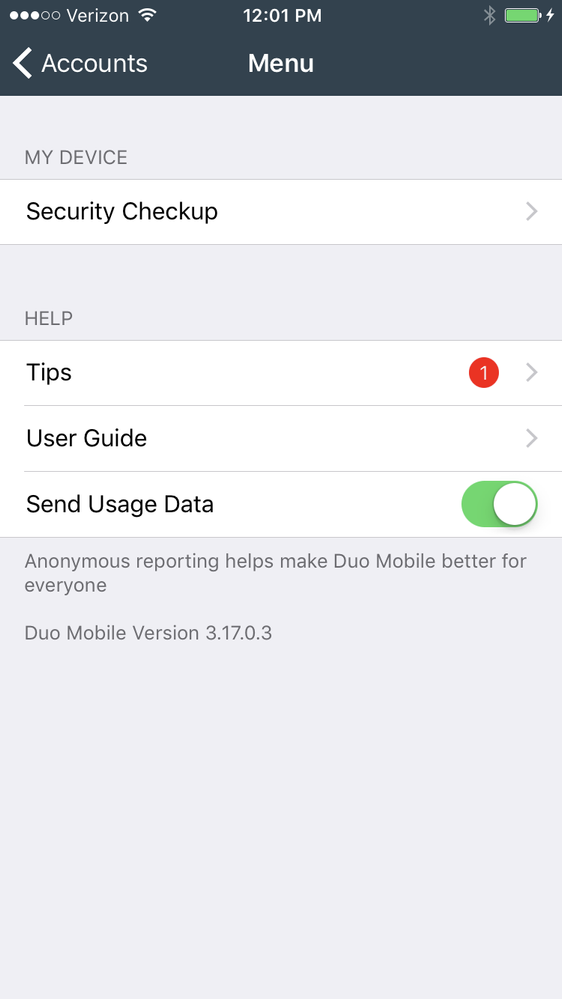
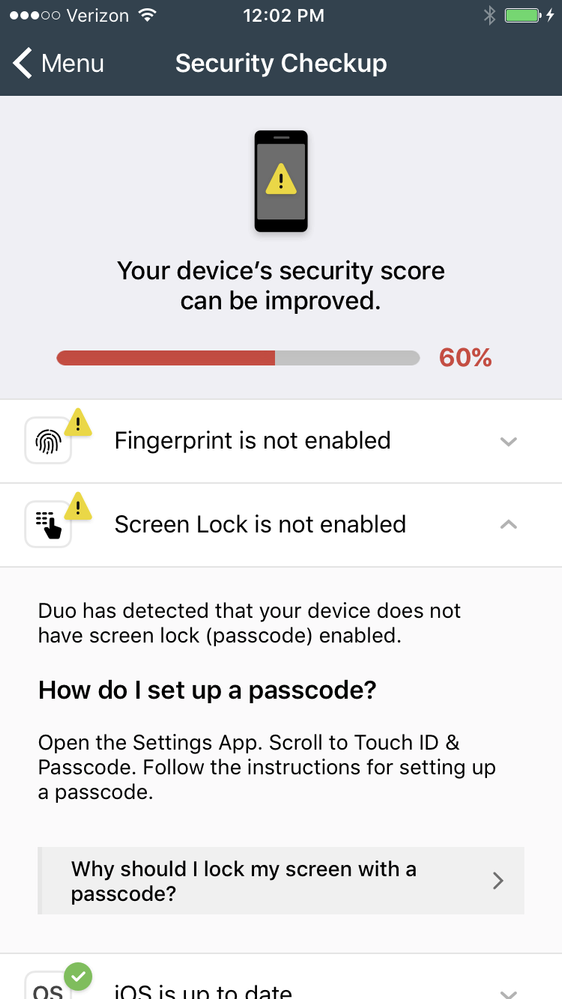
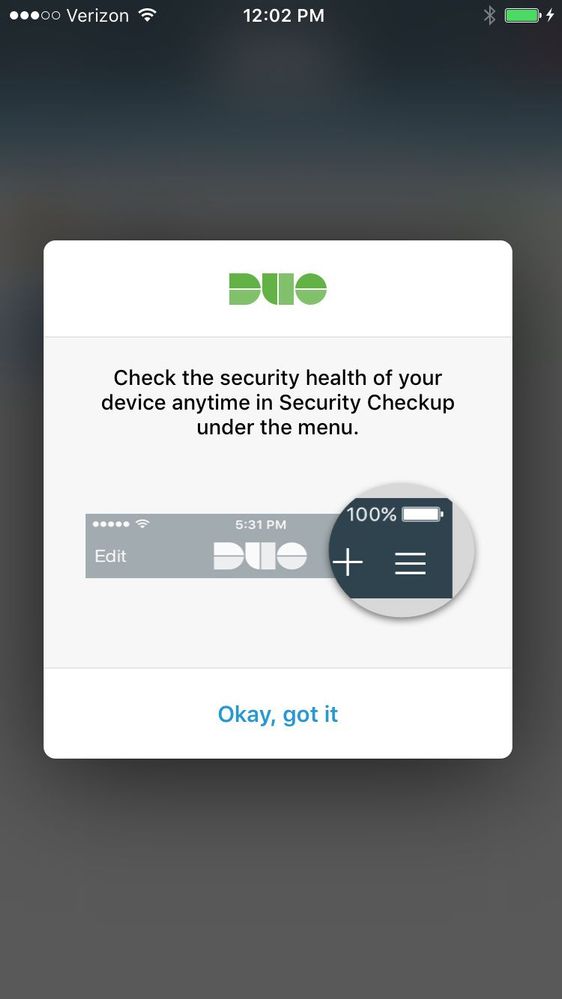
Duo Mobile Security Checkup in Duo Mobile 3.18.0
- Duo Mobile 3.18.0 added the ability for users to view the security health of their 2FA device and learn about ways to remediate any issues from within Duo Mobile.
- The feature will appear within Duo Mobile for all Duo Administrators and the feature has a toggle for end users in the Duo Admin Panel (and is configurable via the Admin API). The toggle will be off by default.
- Once a user has one (or more) accounts with Security Checkup enabled, they will see the feature in the settings menu on their Android or iOS Duo Mobile app.
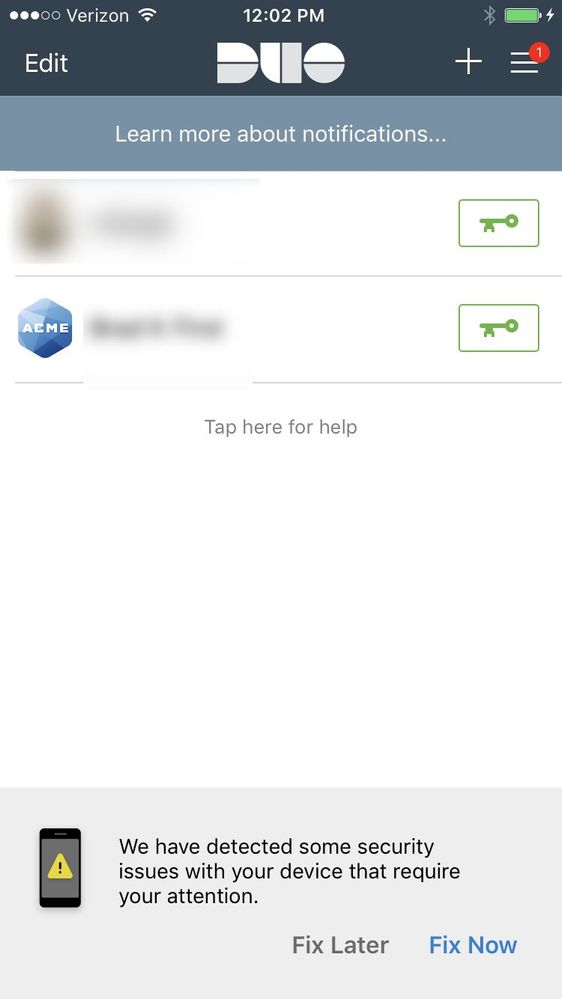
- A notification at the bottom of the Duo Mobile app will be displayed each time a security check changes from pass to fail. The user has the option to either “Fix Later”, which dismisses the footer and highlights that the Security Checkup feature can be accessed from the Settings menu; or “Fix Now”, which opens the Security Checkup page and informs the user of the issue and how it can be remediated. The footer will persist until all the security issues are fixed, or the user dismisses it with “Fix Later”.
Using Duo Mobile to validate the trustworthiness of mobile devices for application access
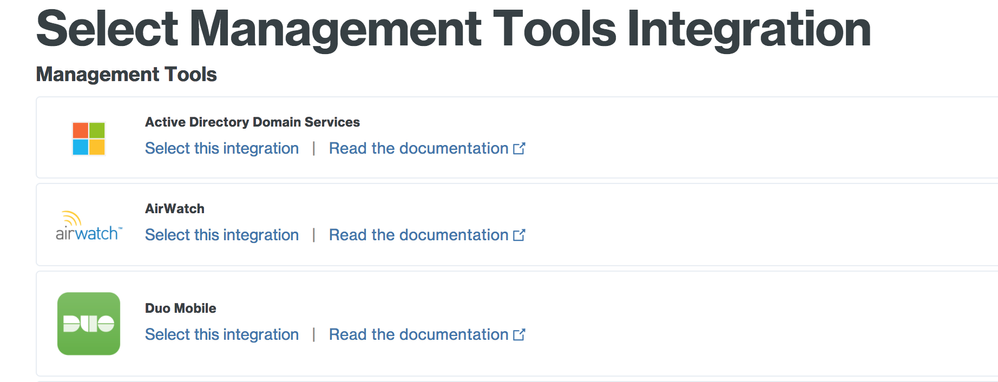
- Duo Beyond edition customers can now use the Duo Mobile app to mark devices as trusted without the need for MDMs like MobileIron and AirWatch.
- To enable this, Duo Beyond edition customers can select the “Duo Mobile” Management Tools Integration in the “Trusted Endpoints Configuration” tab of the Duo Admin Panel.
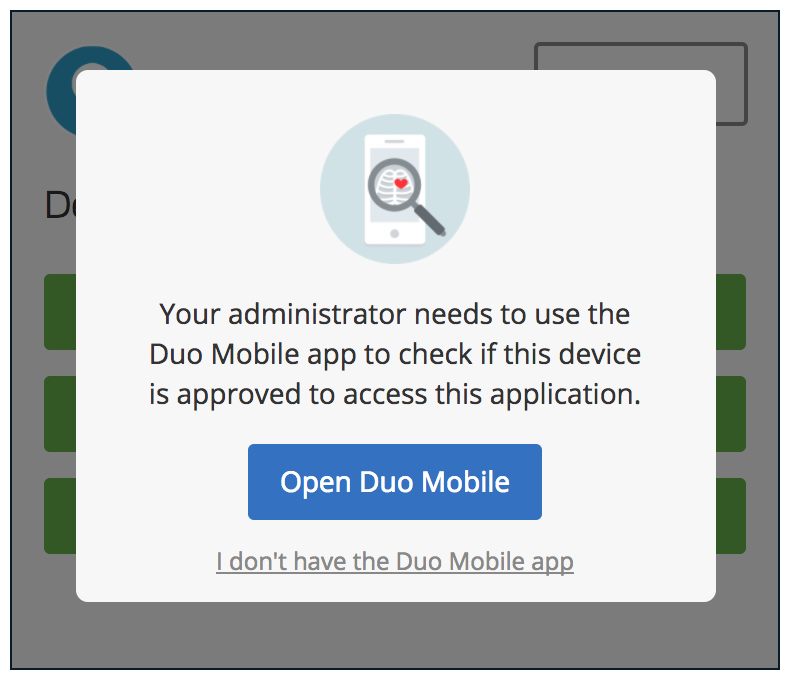
- With this feature enabled, Duo verifies that a 2FA device has an activated Duo Mobile account and that the device is compliant with all of the administrator’s policies even if the device is only used for access.
- Once enabled, users will be prompted to open Duo Mobile to do a health check before they log in to a Duo-protected application. They will be allowed or blocked based on policy, such as Trusted Endpoints, phone passcodes, and so on.
Expanded Management System functionality
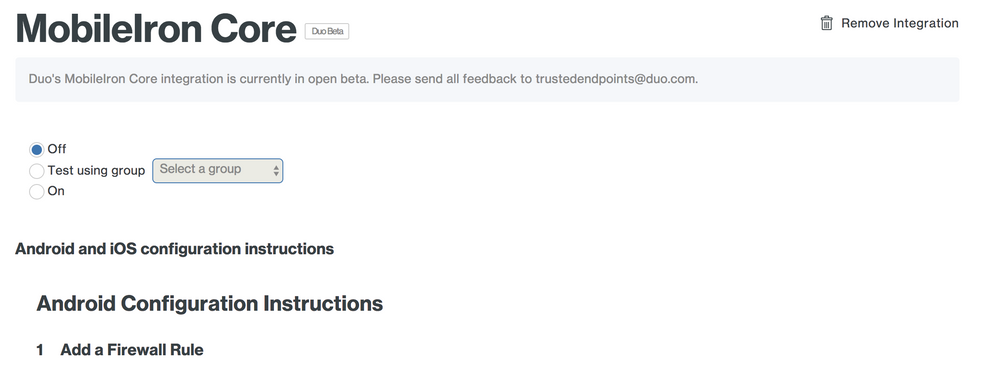
- Management Systems can now be turned off in the Duo Admin Panel. This is to prevent our health checks from starting before admins are ready to check for Trusted Endpoints.
- Management Systems are now off by default when first created. Admins must explicitly turn them on to start checking for Trusted Endpoints.
- A “Test” mode has also been added to MDM integrations. This adds the ability to turn on Trusted Endpoint checks for one group only, for testing purposes.
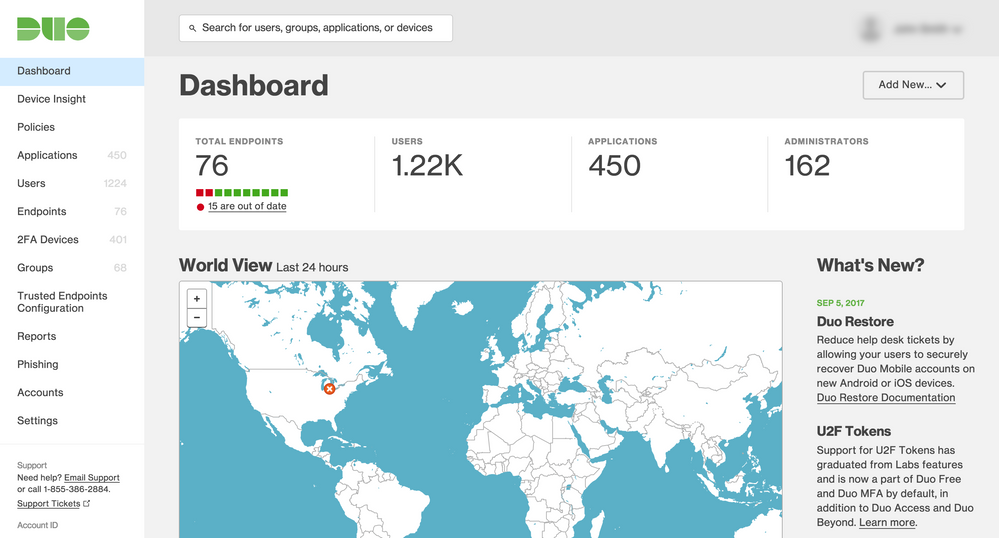
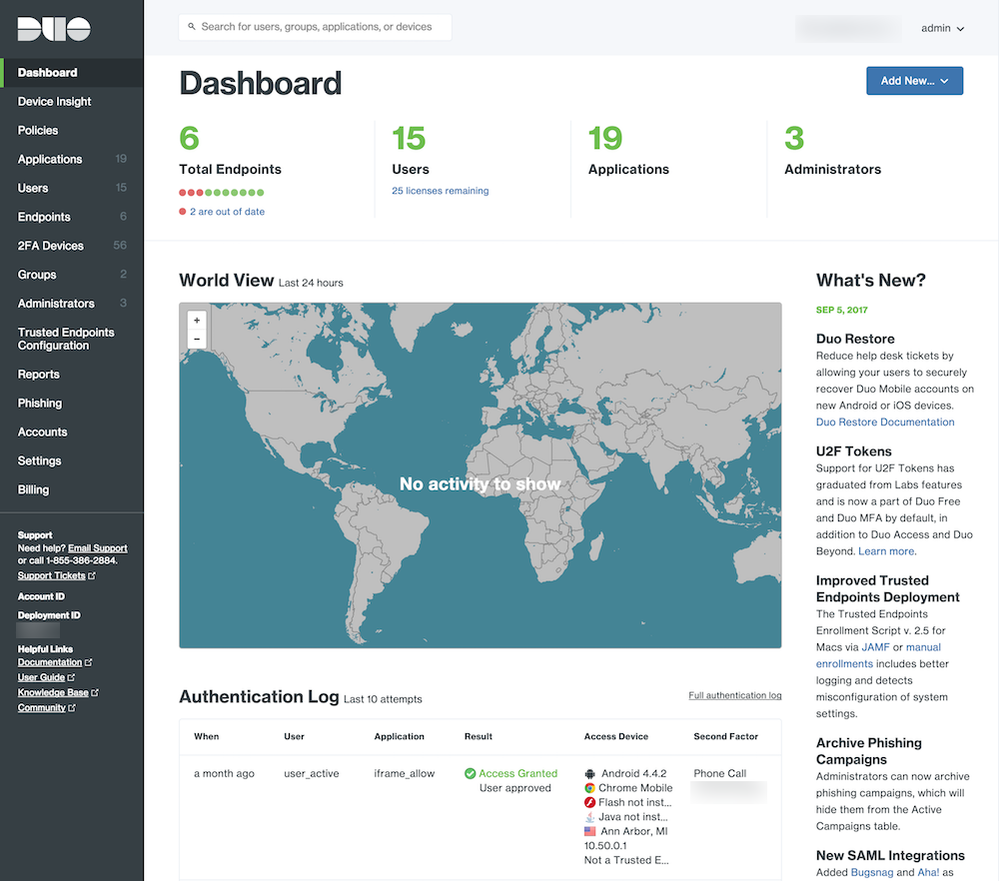
Duo Admin Panel refresh
- The Duo Admin Panel has been made more visually cohesive with the Duo.com website. The UI has also been updated.
- A comprehensive list of changes is available in this Duo blog post.
- The dashboard of the Duo Admin Panel with the old style:
The dashboard of the Duo Admin Panel with the new style:
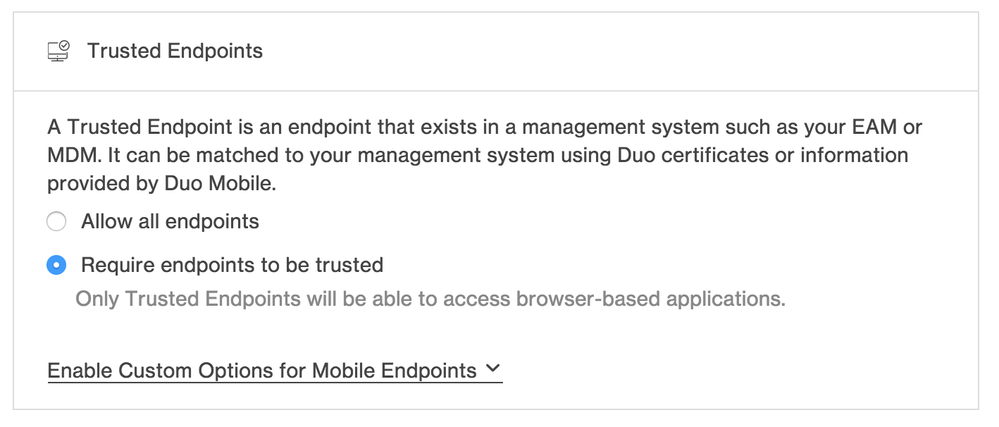
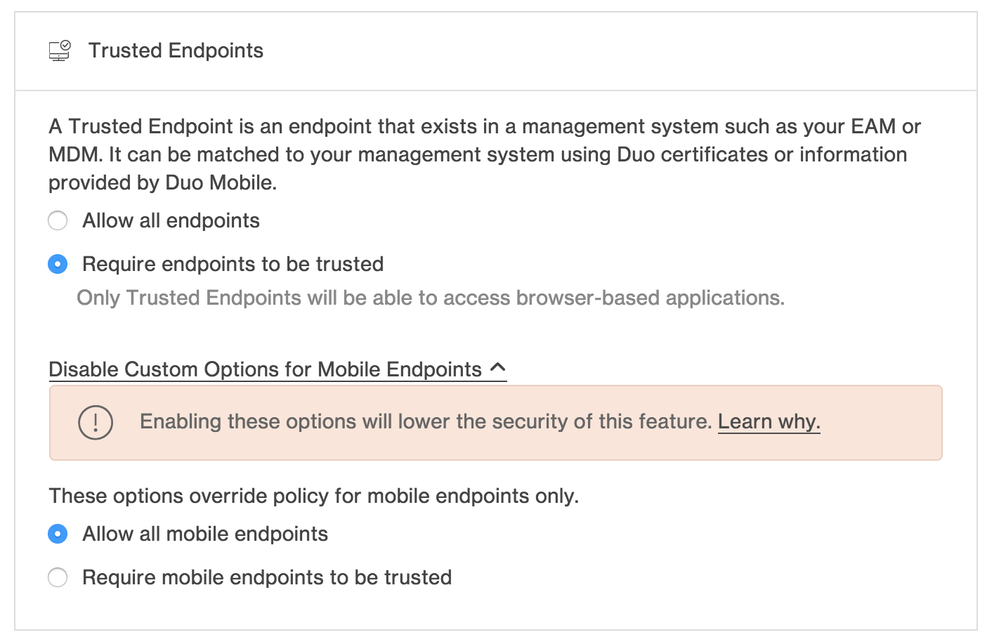
Added mobile-specific Trusted Endpoint policy
- Previously, Trusted Endpoint policy was applied across the board for desktop and mobile devices. Admins can now implement different policies depending on whether a device is a desktop endpoint or a mobile device.
- This feature is accessible via the “Enable Custom Options for Mobile Endpoints” option in the Trusted Endpoints section of the Policy Editor in the Duo Admin Panel.
The additional options are available after clicking the link:
New and updated applications
-
Duo Authentication for Windows Logon and RDP 3.1.1 was released. It features:
- Chaining Duo authentication with smart card logon.
- Configurable username format for Duo.
- Bug fixes.
- Splunk, Meraki, and AWS applications protected by the Duo Access Gateway now support defining custom group prefixes.
- Duo for Outlook Web App (OWA), Duo for RD Web and RD Gateway, and Duo for AD FS 3.0/4.0 have all been updated to support Duo WebSDK 2.6.
Bug fixes
- Added model numbers for new iPhones 8 and X (and some old iPad Pros) so they will now show up correctly in the Duo Admin Panel.
- Fingerprint policy will now be automatically applied to all new iPhone models. The policy no longer needs to be edited with a new release.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: