- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- Duo Release Notes for August 31, 2018
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 08-31-2018 07:07 AM
Hello everyone! Here are the release notes for the most recent updates we’ve made to Duo.
You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
New and updated applications
- CentOS 5 support is deprecated and will be removed in the next release.
- Added support for TLS 1.2.
- Added support for LibreSSL 2.7.0 and up.
- A new package for Ubuntu 18.04 (Bionic Beaver) has been added.
- Minor memory leak fixes.
- Now outputs a message during authentication when a user is locked out.
- Note that releases between 1.10.1. and 1.10.4 contained no code changes.
- The key we use to sign our RPM packages expires September 4. Our newest packages have been signed with a key that extended the expiration date, however in order to take advantage customers will need to import the updated public key with the new expiration into their package management systems. Please see the documentation for more information. You may also want to reference this article in the Knowledge Base and the steps for importing the RPM key.
New features, enhancements, and other improvements
Duo Administrator passwords now validated for domain-specific strings
- Enhanced the security requirements for Duo administrator passwords. Passwords cannot include terms from an administrators name, email address, company name, nor the words “Duo” or “Security”.
Improved Android Trusted Mobile Endpoints workflow
- We have taken new measures to further secure the Trusted Endpoints mobile workflow on Android by no longer using an always-running clipboard service for users authenticating via a WebView (from another app, like Namely). In exchange for better security, users will have to open the Duo Mobile app to start the call out to Duo to see if a device is managed. Then, If the check is successful, Duo Mobile will tell the user to switch back to the calling app.
- The regular use case whereby users are authenticating from a mobile browser (to something like the DAG) will not be altered to tell the user to switch apps. That will continue to function as it does currently.
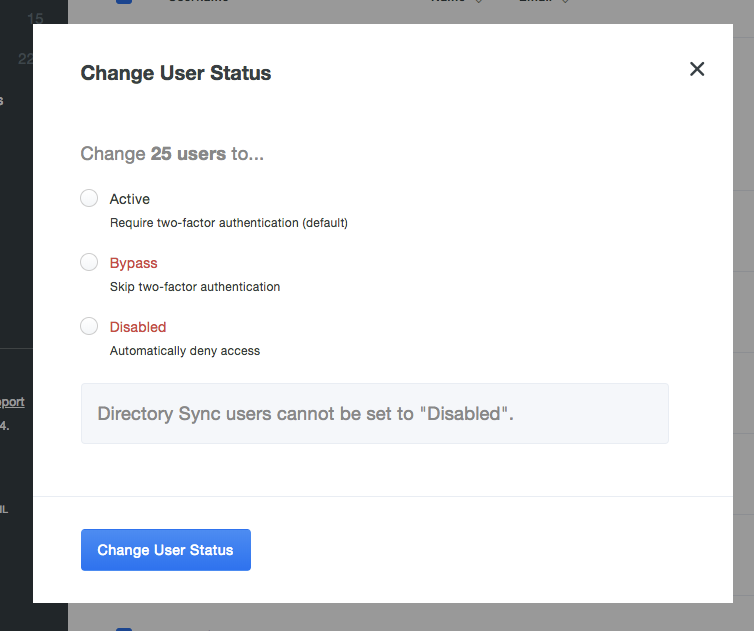
Synchronized users’ status can now be changed in bulk
- Users synchronized to Duo from an external directory can now have their status changed between “Active” and “Bypass” in bulk actions.
- Synchronized users’ status cannot be changed to “Disabled”.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Were there any changes to username canonicalization/normalization? I have several integrations that have started failing today because usernames like A-B@C.com were previously normalized to A, but had normalization completely disabled overnight. Furthermore, even after turning on normalization again, it’s only normalizing to A-B, so authentication still fails.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
If you haven’t already contacted Duo Support please do so we can get more information about your issue.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@DuoKristina - sadly I’m on the free plan, so I don’t have access to open cases. I think the forums/community are all I have access to.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
If you think you’ve found a bug or issue with this release definitely contact Support via phone, chat, or email - no matter what plan you’re on - so we can investigate.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi there,
Just to clarify: As a Duo Free administrator, you do still qualify for unlimited best-effort email support. If you think you’ve discovered a service outage related to Duo, please do feel free to report via phone call. If you believe you have discovered a security-related issue, please follow the process described here: Security Response | Duo Security.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: