- Cisco Community
- Technology and Support
- Security
- Duo Security
- Managing Devices
- Duo Checkpoint package
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 12:28 AM
Hi Team
We have configured checkpoint to work with Duo. At present we getting through secondary authentication through the App using DUO Push. This is default feature. How ever, we are looking for Secondary Authentication mode to be selected by the post primary authentication with our DUO. I have seen docs for Cisco integration where the docs calls-out of getting a Duo Cisco package for getting the secondary authentication page.
Do we have a similar package developed for Checkpoint Mobile Blade Remote Access. Suggestions/guidence/directions will be appreciated.
Thanks
Solved! Go to Solution.
- Labels:
-
Managing Devices - General
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2019 12:25 PM
We are pleased to support CheckPoint mobile access with our “auto push” experience via RADIUS authentication. There are no plans to support another authentication experience.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 04:43 AM
Hello! Our Check Point integration does not offer the ability to use the Duo Prompt, which is what I believe you are referring to when you write “secondary authentication page.”
However, as indicated in the documentation for our Check Point integration, you can append “push”, “phone”, or “sms” to your password. “Push” and “phone” send an immediate 2FA request to your device, while “sms” delivers passcodes to your main phone number. You can then append an SMS-delivered passcode to your password to complete login.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 10:24 AM
Hello there,
I got your point and agree with. However, when the package for Cisco was developed for such requirement, then, why not for checkpoint?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2019 12:25 PM
We are pleased to support CheckPoint mobile access with our “auto push” experience via RADIUS authentication. There are no plans to support another authentication experience.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2020 01:30 AM
Hi @ganeshhonakeri,
Sorry to interrupt. Can you please share the configuration done on Checkpoint and Duo Auth Proxy? I have explained below regarding the problem I am currently facing.
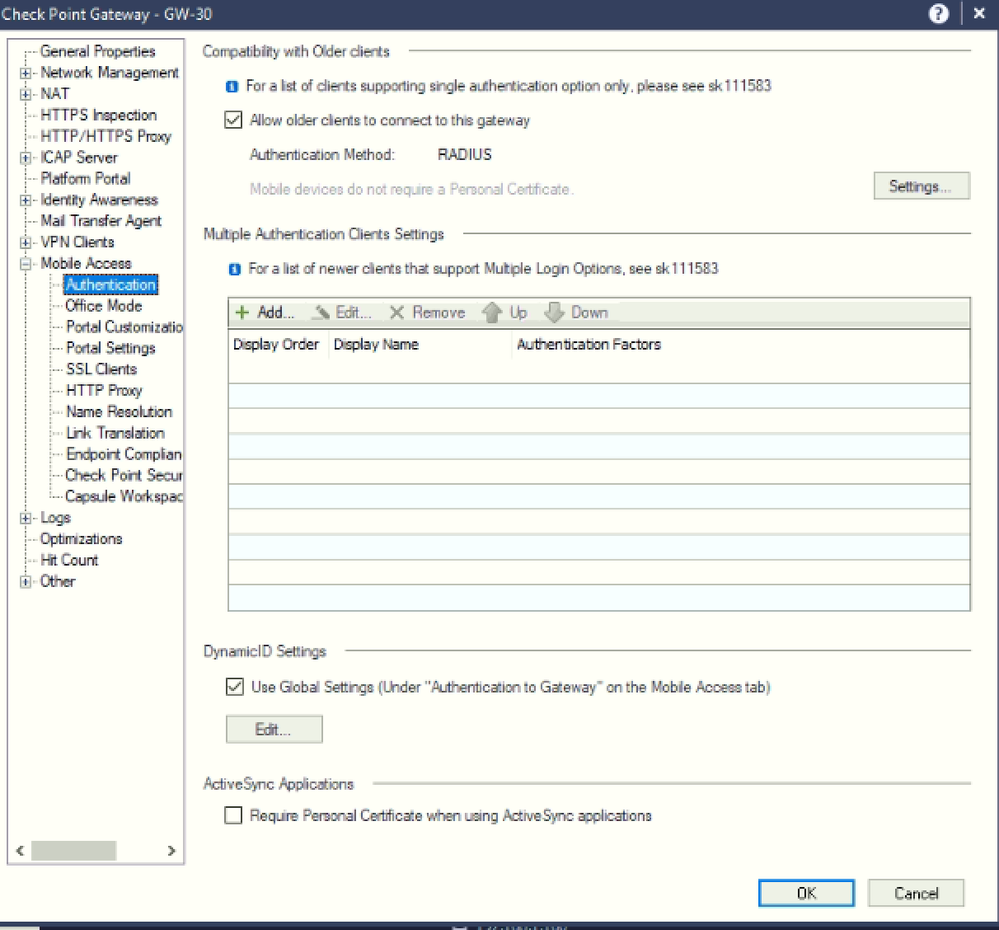
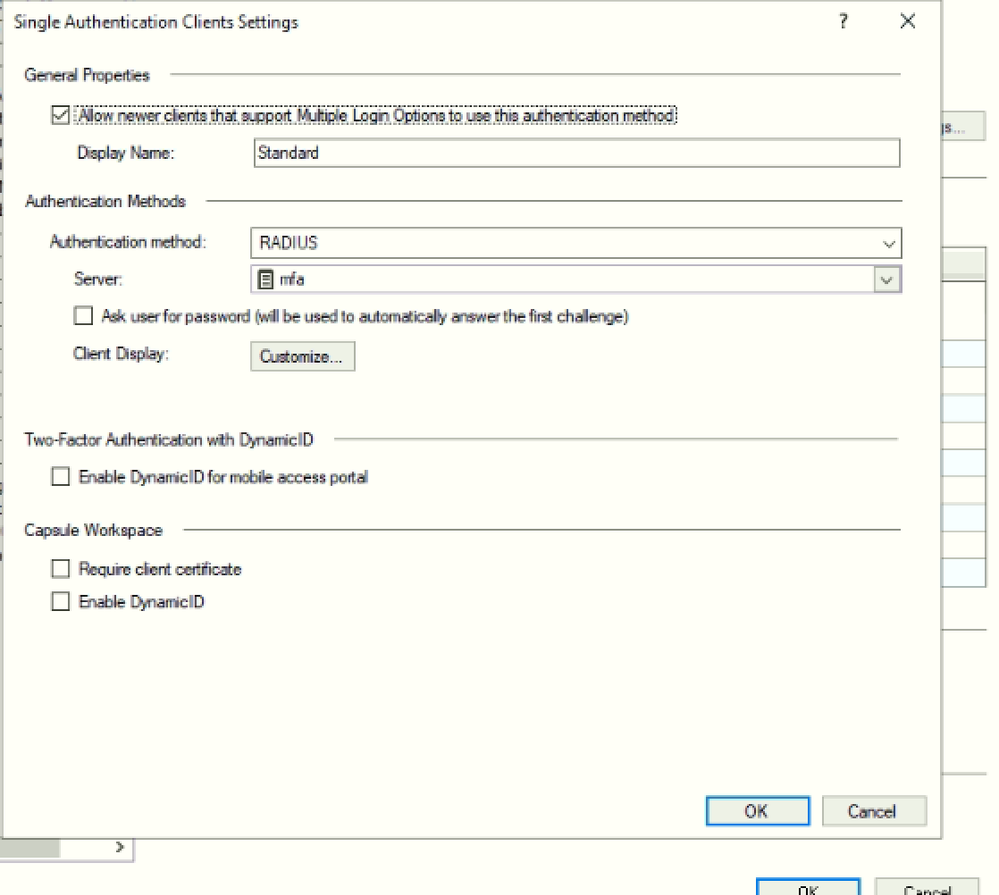
I have configured the Checkpoint to work with Duo. Followed the Checkpoint mobile access documentation of Duo. I have configured DUO as our authentication proxy and the DUO auth proxy is synced with AD for a primary authentication. I have enabled mobile access and in my case, VPN traffic first comes to a gateway —> Radius (Duo)----> AD and I am able to connect to the VPN.
The problem that I am facing, VPN authentication request goes to DUO auth proxy and it gets authenticated with AD and gets connected straight away. So, my secondary authentication is not working i.e. I dont receive Duo Push or SMS
Please note that the Internet connectivity is fine in my Duo Proxy (reachable to all the Duo Cloud services) and I have enrolled the user and added on my duo mobile app as a duo protected app. Also, the configuration done on the checkpoint is good as the authentication traffic is going to Duo and it validates the credentials from the AD and gets connected.
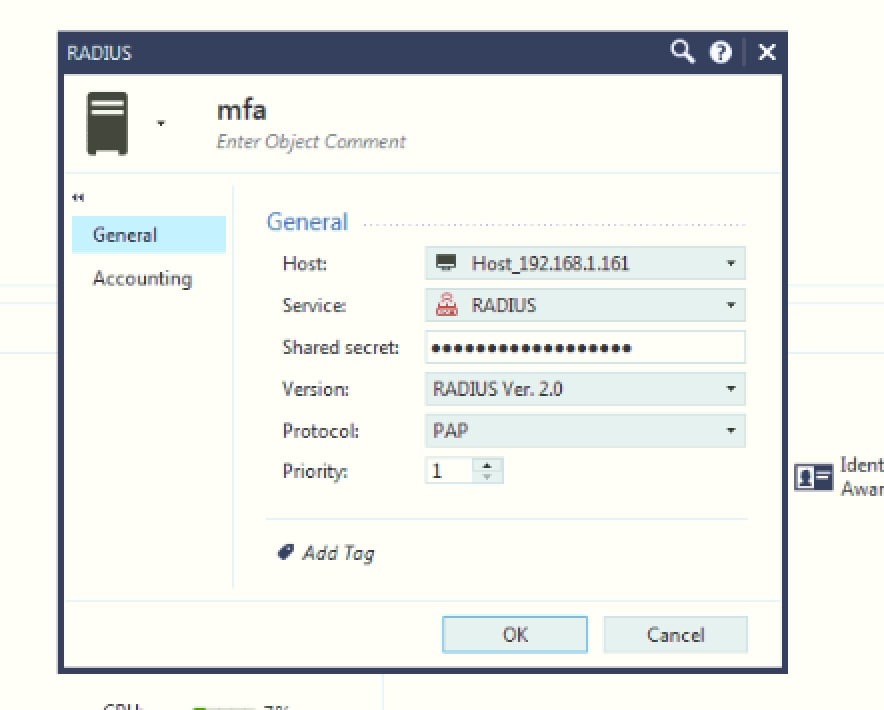
I have attached the configuration done on the Checkpoint. Also, the one I have shared both the auth proxy configuration and logs:
AuthProxy Config:
[ad_client]
host=192.168.1.161
service_account_username=administrator
service_account_password=COVIDCOVID
search_dn=DC=test,DC=local
[radius_server_auto]
ikey=xxxxxxxxxxxxxxxxxx
skey=COVIDCOVID
api_host=xxxxxxxxxxxxxxxxxxxxxxxxxx
radius_ip_1=192.168.1.160
radius_secret_1=covid
client=ad_client
debug=true
failmode=secure
AuthProxy Connected Logs
2020-04-22T00:22:47-0700 Duo Security Authentication Proxy 3.2.4 - Init Complete
2020-04-22T00:25:52-0700 (UDP Port 1812 Closed)
2020-04-22T00:25:52-0700 Stopping protocol <duoauthproxy.lib.forward_serv.DuoForwardServer object at 0x03110850>
2020-04-22T00:25:52-0700 Main loop terminated.
2020-04-22T00:25:56-0700 DuoForwardServer starting on 1812
2020-04-22T00:25:56-0700 Starting protocol <duoauthproxy.lib.forward_serv.DuoForwardServer object at 0x031898F0>
2020-04-22T00:25:56-0700 FIPS mode is not enabled
2020-04-22T00:25:56-0700 AD Client Module Configuration:
2020-04-22T00:25:56-0700 {‘host’: ‘192.168.1.161’,
‘search_dn’: ‘DC=test,DC=local’,
‘service_account_password’: ‘’,
‘service_account_username’: ‘administrator’}
2020-04-22T00:25:56-0700 [-] RADIUS Automatic Factor Server Module Configuration:
2020-04-22T00:25:56-0700 [-] {‘api_host’: '’,
‘client’: ‘ad_client’,
‘debug’: ‘true’,
‘failmode’: ‘secure’,
‘ikey’: '’,
‘radius_ip_1’: ‘192.168.1.160’,
‘radius_secret_1’: '’,
‘skey’: ‘*****[40]’}
2020-04-22T00:25:56-0700 Duo Security Authentication Proxy 3.2.4 - Init Complete
Please find the attached configurations done on the Checkpoint
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2020 09:18 PM
Make sure to change the service to new-radius
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide