- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Duo Auth proxy password encryption length
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2023 09:39 AM
Hello. We have the Duo auth prox conf file all setup and works fine. we use the raidus against meraki MX which works fine with the secret. when we try to encrypt the secret password the auth hashes it out into a very long string. meraki only accepts max of 48 characters for the secret. That being said is there anyway to make the duo has the password to only max of 48 characters?
Solved! Go to Solution.
- Labels:
-
Authentication Proxy
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 01:03 PM
Hi @ShawnGaston ,
The encrypted text of the secret from the Auth Proxy should not be entered into the RADIUS appliance. The Auth Proxy hashes the secret but only for its own use.
In this example, the RADIUS secret for the Meraki Client VPN config is radiussecret1
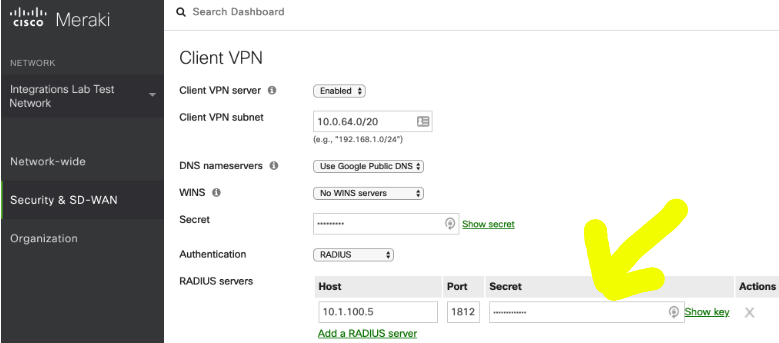
In the Duo Auth Proxy configuration, you would have entered it into the authproxy.cfg as:
[radius_server_auto]
ikey=■■■■■■■■■■■■■■■■■■■■
■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■
api_host=■■■■■■■■■■■■■■■■■■■■■■■■■■■■
radius_ip_1=5.6.7.8
radius_secret_1=radiussecret1
client=ad_client
port=1812
failmode=safe
Then, after performing the encryption command, the output will resemble:
[radius_server_auto]
ikey=■■■■■■■■■■■■■■■■■■■■
skey_protected=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
api_host=■■■■■■■■■■■■■■■■■■■■■■■■■■■■
radius_ip_1=5.6.7.8
radius_secret_protected_1=AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAFAXGTZJdPUuF9JbcuvSwagQAAAAeAAAAdwBpAG4AMwAyAGMAcgB5AHAAdABvAC4AcAB5
AAAAA2YAAMAAAAAQAAAANZiilAGq57x56P7+pdOPLgAAAAAEgAAAoAAAABAAAABdyNk87n/s53Jgyn4X6h+4IAAAADd4goUuz1WL
f6FEHmFZbL0wSxpH6GWFbyFGTw32fedsFAAAAMYIwtQ8Ac2ZalrXaSReUivsdkJ+
client=ad_client
port=1812
failmode=safe
The Meraki RADIUS server secret will remain radiussecret1
Encryption for the Auth Proxy’s secrets helps protect them from being viewable in plain text within the authproxy.cfg file.
Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2023 01:03 PM
Hi @ShawnGaston ,
The encrypted text of the secret from the Auth Proxy should not be entered into the RADIUS appliance. The Auth Proxy hashes the secret but only for its own use.
In this example, the RADIUS secret for the Meraki Client VPN config is radiussecret1

In the Duo Auth Proxy configuration, you would have entered it into the authproxy.cfg as:
[radius_server_auto]
ikey=■■■■■■■■■■■■■■■■■■■■
■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■
api_host=■■■■■■■■■■■■■■■■■■■■■■■■■■■■
radius_ip_1=5.6.7.8
radius_secret_1=radiussecret1
client=ad_client
port=1812
failmode=safe
Then, after performing the encryption command, the output will resemble:
[radius_server_auto]
ikey=■■■■■■■■■■■■■■■■■■■■
skey_protected=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
api_host=■■■■■■■■■■■■■■■■■■■■■■■■■■■■
radius_ip_1=5.6.7.8
radius_secret_protected_1=AQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAFAXGTZJdPUuF9JbcuvSwagQAAAAeAAAAdwBpAG4AMwAyAGMAcgB5AHAAdABvAC4AcAB5
AAAAA2YAAMAAAAAQAAAANZiilAGq57x56P7+pdOPLgAAAAAEgAAAoAAAABAAAABdyNk87n/s53Jgyn4X6h+4IAAAADd4goUuz1WL
f6FEHmFZbL0wSxpH6GWFbyFGTw32fedsFAAAAMYIwtQ8Ac2ZalrXaSReUivsdkJ+
client=ad_client
port=1812
failmode=safe
The Meraki RADIUS server secret will remain radiussecret1
Encryption for the Auth Proxy’s secrets helps protect them from being viewable in plain text within the authproxy.cfg file.
Hope this helps!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2023 01:51 AM
TY for the clarification. That def makes sense!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

