- Cisco Community
- Technology and Support
- Security
- Duo Security
- APIs
- Duo Auth API Sample - HMAC Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Duo Auth API Sample - HMAC Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-24-2020 06:41 AM
We are working to implement a the Duo Auth API. We utalize a homegrown application to construct webservice requests. We are attmepting to use that code to construct the sample request found at Auth API | Duo Security. The issue we are having is that the HMAC we are generating does not match the HMAC that is shown in the sample.
To validate our application, we are using the HMAC generator here: https://www.freeformatter.com/hmac-generator.html#ad-output
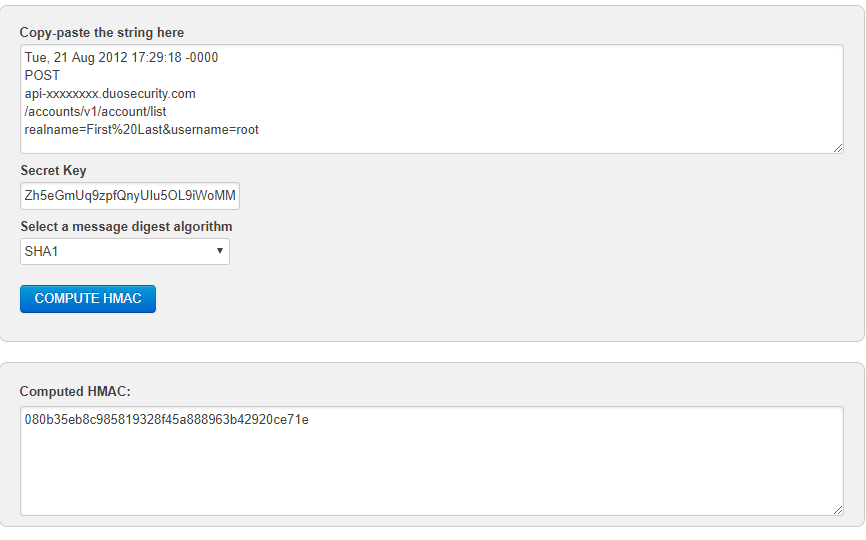
We are then using this tool to Base64 the HMAC output: https://www.base64encode.org/
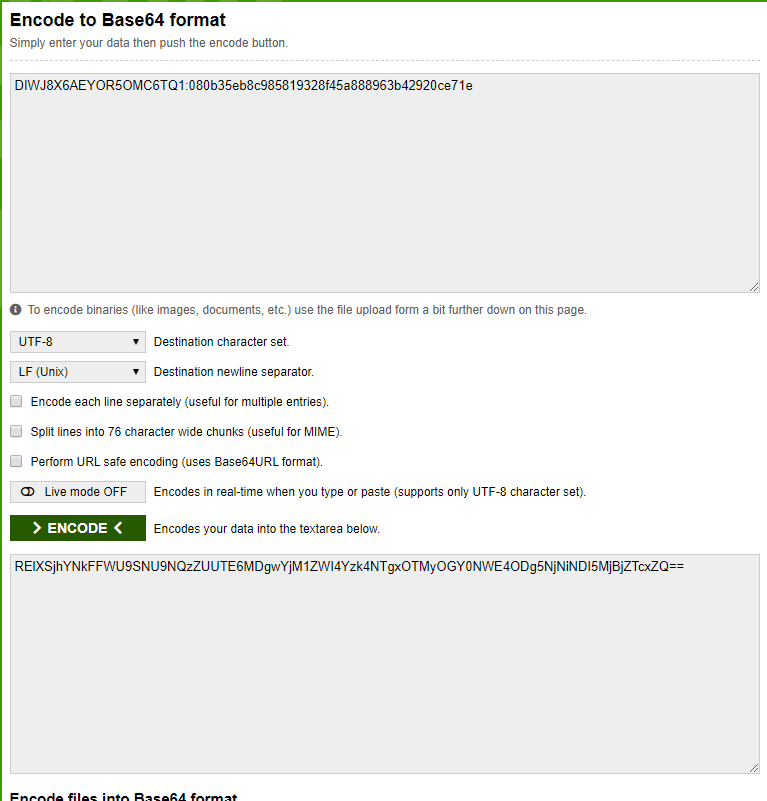
We believe that this output should match what we see as the Basic Auth key in the Duo API sample, but unfortunately it does not.
Date: Tue, 21 Aug 2012 17:29:18 -0000
Authorization: Basic RElXSjhYNkFFWU9SNU9NQzZUUTE6MmQ5N2Q2MTY2MzE5NzgxYjVhM2EwN2FmMzlkMzY2ZjQ5MTIzNGVkYw==
Host: ■■■■■■■■■■■■■■■■■■■■■■■■■■■■
Content-Length: 35
Content-Type: application/x-www-form-urlencoded
Can anyone pinpoint what we are doing wrong here?
- Labels:
-
API - General
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 05:43 PM
I also have the same issue with this one. I’m just not sure which part we are wrong although all our credentials seems to be working with Postman. We are currently implementing using Delphi REST Client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 11:49 PM
We have the same problem here too. Like @lvincent7 we are using Delphi RIO and the TRestClient.
I tried the python script from here https://github.com/duosecurity/duo_client_python with our parameter and it works like a treat.
But what I can see so far it must have something to do with the encoding of the key and the body for the HMAC.SHA1. In the python script it is transforming it to a Bytes literal before running the HMAC.SHA1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 04:38 AM
Yup same problem here too. I am getting invalid signature when I try to run the request. The API documentation sucks. Where I have a question is in the time zone offset. Even though the documenation shows -0000 I do belive you are supposed to put the actual offset there. When I put -0000 as the offset i get “missing credentials” but when i put “-0500” i get invalid signuature. So I am not sure which one is right…
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 07:24 AM
Because of the lack of reply from the Duo team here and no viable path forward, we have given up on Duo and are moving forward with a different solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 09:55 AM
Hi everyone,
Thank you for bringing this to our attention. We will look into fixing the HMAC example in the documentation.
Please contact Duo Support to troubleshoot this issue, and they will be able to help you figure out what’s going on here. As a friendly reminder, while we respond where we can, the community isn’t an official support channel with guaranteed response times.
For anyone reading, we have knowledge base articles on frequently asked questions around our Auth API that might prove useful too: Link to Auth API articles here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-13-2020 05:51 PM
After a lot of exploration we were able to resolve our issue with the help of @NielsMaschmeyer. Basically, if anyone creating a Delphi REST client API that interacts with DUO API you have to look into the encoding. Prior to the signature creation, the parameters must be AnsiString then pass these for generating the signature using the built-in THashSHA1.GetHMAC in Delphi together with the secret key. Bind the result with the Basic Authenticator, in addition you add the query parameters to your REST request parameters. I hope you are able to get that. Will simplify our solution and hopefully share it here.
Cheers!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide