- Cisco Community
- Technology and Support
- Security
- Duo Security
- Managing Users
- Deny external access to shared/ service accounts
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2021 03:38 AM
Hi all, Sorry if this has been asked before!
im looking for the correct way to manage shared or general O365 email accounts scanner@ dispatch@ etc . These are accounts used for users or devices who don’t have a phone or 2FA token. I would like them to be used within the trusted network without authentication prompt, if accessed from outside the network then deny completely
currently they are synced from AD and exisit as not authenticated within Duo
many thanks
Mike
Solved! Go to Solution.
- Labels:
-
Managing Users - General
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2021 06:26 AM
The Authorized Networks policy setting for Access and Beyond Duo plans has a “Deny access from all other networks”, so what you want could be implemented like…
-
Create a group in Duo with these shared accounts as members (if you are syncing these accounts into Duo that means creating a group in your source directory with these accounts as members and then adding that group to your sync to import it into Duo.
-
Apply a custom group policy to whichever Duo application protects O365 access (Azure CA, O365+DAG, M365+Duo SSO, etc). The group policy should target the group of these service accounts you imported into Duo in step 1, and in that policy configure the Authorized Networks setting to allow access from your trusted network and deny access from other networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2021 06:26 AM
The Authorized Networks policy setting for Access and Beyond Duo plans has a “Deny access from all other networks”, so what you want could be implemented like…
-
Create a group in Duo with these shared accounts as members (if you are syncing these accounts into Duo that means creating a group in your source directory with these accounts as members and then adding that group to your sync to import it into Duo.
-
Apply a custom group policy to whichever Duo application protects O365 access (Azure CA, O365+DAG, M365+Duo SSO, etc). The group policy should target the group of these service accounts you imported into Duo in step 1, and in that policy configure the Authorized Networks setting to allow access from your trusted network and deny access from other networks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 12:44 AM
thanks for that - its on the right lines as i was thinking but am i right to assume that the account has to be enrolled? If so how is this best way to do this without a mobile phone or hardware key ?
thanks for your time
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 06:06 AM
The accounts that you want to bypass Duo MFA when connecting from the internal trusted network do not need to be enrolled in Duo if you do not check the “Require enrollment from these networks” option in the authorized networks policy, as described in the documentation I linked in the earlier response.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 06:53 AM
thanks again Kristina - im obviously getting something wrong.
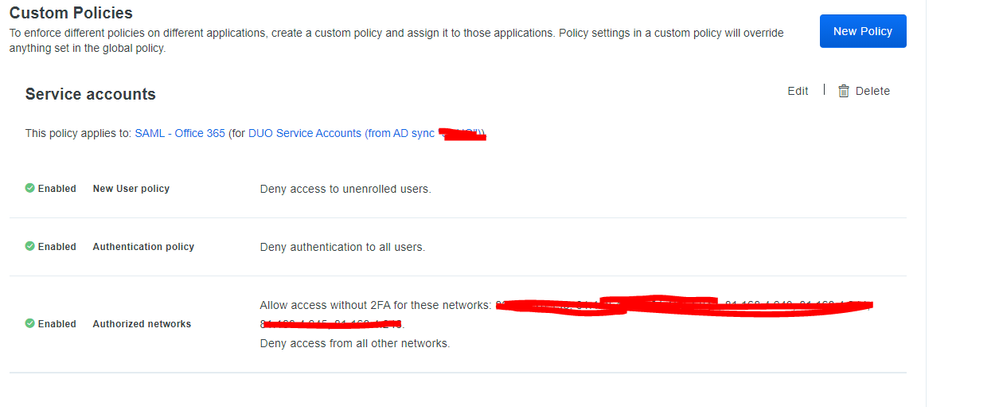
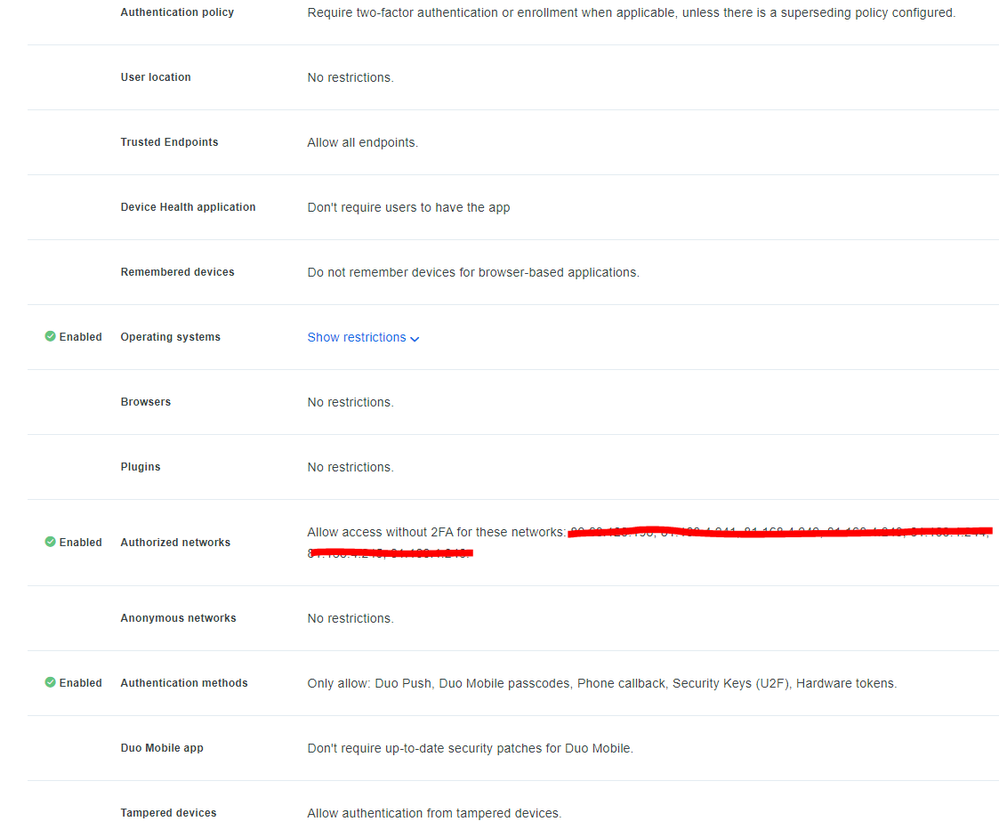
the test user is showing in the portal as ‘Active’ the group he’s a member of the new ‘service accounts’ group only - this is synced and shown in duo , ive attached the global & custom policy. When i login as that user from out of a trusted IP it just prompts me to setup Duo , i can add a mobile then it logs in
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 11:34 AM
What is it like on the Microsoft side? Does it require 2FA and how is that set up? My domain is federated within Microsoft and directed to use Duo MFA.
Be sure to uncheck “solved” because it thinks @DuoKristina’s answer is the solution and the post then becomes somewhat less active. Obviously, it’s not solved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 12:34 PM
Ah, ok.
So in Duo an “enrolled” user is a user that is known to Duo (username exists) and has an associated authentication device (able to complete 2FA).
A user that is known to Duo but has no devices is partially enrolled. Duo doesn’t care for this state because the user can’t complete 2FA, so it will have partially enrolled users try to complete enrollment.
When I answered the second question about enrollment in the networks policy, I forgot that I had already recommended creating the users in Duo to be able to apply a group policy to them (because you don’t want all users on that network to get in without 2FA and blocked elsewhere, right?
![]()
So yeah, you need a dummy authenticator on those service account users in Duo to get them into fully enrolled state.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 01:01 PM
Ah OK thanks to both…this sounds like where my confusion is. I shall go ahead and find a device to complete the authentication.
Mike
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-09-2021 01:30 PM
Like, if you just go into the Duo Admin panel and attach a phone to one of those service account users with a fake number like 213-555-1212, that completes enrollment and then the service account should slide right in past Duo.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 12:41 AM
Thank you , that has now worked as required. Allowing access with no prompt ‘inside’ the network, straight deny from everywhere else
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2021 09:12 AM
Glad to hear it! Thanks for following up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-21-2021 02:33 AM
Just for anyone else in the same situation… this can be achieved as per above if you have the correct Duo Plan (Access / Beyond) . If you have the Duo MFA plan you cannot block other networks except trusted. What i did was to create a new policy for the users to
Deny access to unenrolled users (new user policy)
Require 2FA or enrollement (Auth Policy)
Enable authorised networks (customers IP’s)
uncheck all options for authentication methods
set the policy to the application , create a AD group (ie deny external access), add required users and sync. - i didn’t bother adding a device to any user in this group.
now they can access applications within trusted network without duo prompt , access external shows a Duo denied message
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: