- Cisco Community
- Technology and Support
- Security
- Duo Security
- Duo Release Notes
- D265: Duo Release Notes for May 12, 2023
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 05-12-2023 06:32 AM
Hello everyone! Here are the release notes for our most recent updates to Duo.
Public release notes are published on the Customer Community every other Friday, the day after the D-release is completely rolled out. You can subscribe to notifications for new release notes by following the process described here. If you have any questions about these changes, please comment below.
What’s in this release?
New features, enhancements, and other improvements
- Duo Trusted Endpoints Now Available to Duo Essentials, Advantage and Premier Editions
- Available in Public Preview: Device Activity Notifications
- Duo Central Self-Service Portal: Clearer Language for Settings
- Improved Passwordless Administration in the Duo Admin Panel
- Risk-Based Authentication Now Reports More Information about Trust Assessment
- Update to Duo Admin API
New and updated applications
- Five New Named Applications with Duo SSO
- Duo SSO: New Password Change Options Available
- Duo for Microsoft Outlook Web App (OWA) version 2.0.0
- Universal Prompt Now Available for OneLogin and Microsoft OWA
- Duo Authentication Proxy Version 5.8.1
- Duo Mobile 4.40.0 for Android
- Duo Mobile 4.40.0 for iOS
Bug fixes
New features, enhancements, and other improvements
Duo Trusted Endpoints now available to Duo Essentials, Advantage and Premier editions
- Effective May 8, 2023, all Duo customers of paid editions will be able to use Trusted Endpoints to block access from unknown devices and allow only trusted devices to gain access to resources. Duo Trusted Endpoints features were previously available only to our highest pricing tier. Check out these resources to get started:
- Level Up your skills with the course, Getting Started with Trusted Endpoints.
- Follow our Best Practices for Implementing Trusted Endpoints.
- Read our Deployment Setup Tips. Which scenario describes your organization?
- To learn more, register for the upcoming webinar, Block Unwanted Access with Duo Trusted Endpoints. We have scheduled three sessions to make this event available globally:
- Also effective May 8, we renamed our editions:
- Duo MFA is now Duo Essentials
- Duo Access is now Duo Advantage
- Duo Beyond is now Duo Premier
- Duo pricing has not changed.
- Duo began updating Documentation on May 1 to reflect new feature availability and edition names.
- Trusted Endpoints will not be made available to Duo Free and Duo Federal editions.
- Duo’s Premium Customer Success service is available to support your strategic efforts and provide technical expertise.
Available in public preview: Device activity notifications
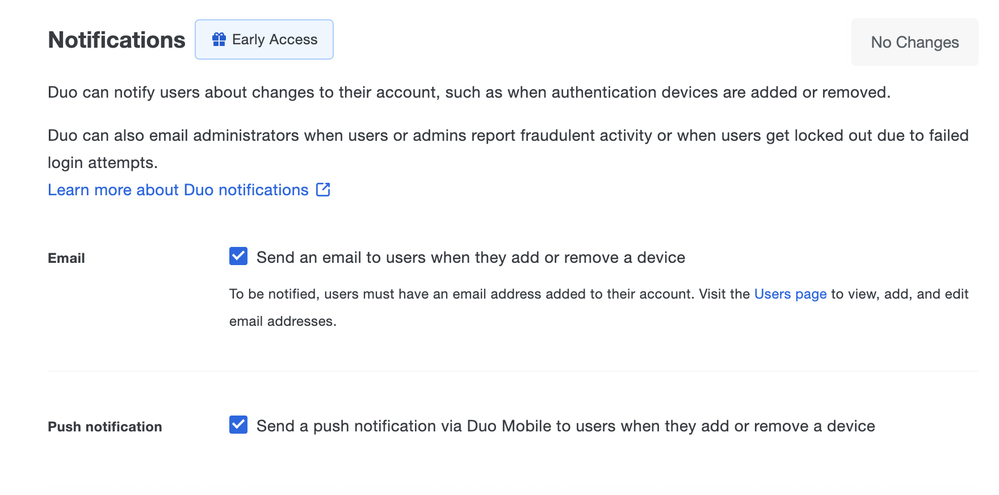
- Duo can now send device activity email and/or Duo Push notifications to end users when a device is added or removed from their account.
- Users can respond to the notification by confirming the change or reporting it as fraudulent. If the user reports a fraudulent change, Duo administrators receive an email notification.
- To participate in this public preview, enable device activity notifications in Duo Admin Panel > Settings > Notifications.
Duo Central Self-Service Portal: Clearer language for settings
- We made language changes to the Self-Service Portal settings under Duo Single Sign-On > Duo Central in the Duo Admin Panel to improve clarity.
Improved Passwordless administration in the Duo Admin Panel
- Users with Administrator and Owner roles can now enable passwordless authentication and view passwordless reporting in the Duo Admin Panel; previously only Owners could do so.
- Owners can customize their Duo Single Sign-On (SSO) subdomain to improve branding and help users recognize phishing attacks. Adjust the subdomain under Single Sign-On > Customize your SSO subdomain.
Risk-Based Authentication now reports more information about Trust Assessment
- For Duo Advantage and Premier customers who have applied risk-based policies, the Authentication Log Trust Assessment column will now show one of the following reasons for a a step-up authentication decision: Consecutive failures; Credential stuffing; Push harassment; Previously marked fraud; Country code mismatch; Unrealistic travel; Multiple reasons.
Update to Duo Admin API
- In order to improve our overall security posture, Duo no longer supports server-side key generation for authenticator enrollments. We removed server-side key generation in 2016, and we’ve now removed the ability to activate from instances of Duo Mobile released prior to 2016.
New and updated applications
Five new named applications with Duo SSO
- There are now named applications to protect 1Password, Snowflake, Notion, Syncplicity and Tableau Online using Duo SSO, our cloud identity provider.
- Reminder: Duo Access Gateway will reach end of life in October 2023. Please see the Guide to Duo Access Gateway end of life for more details.
Duo SSO: New password change options available
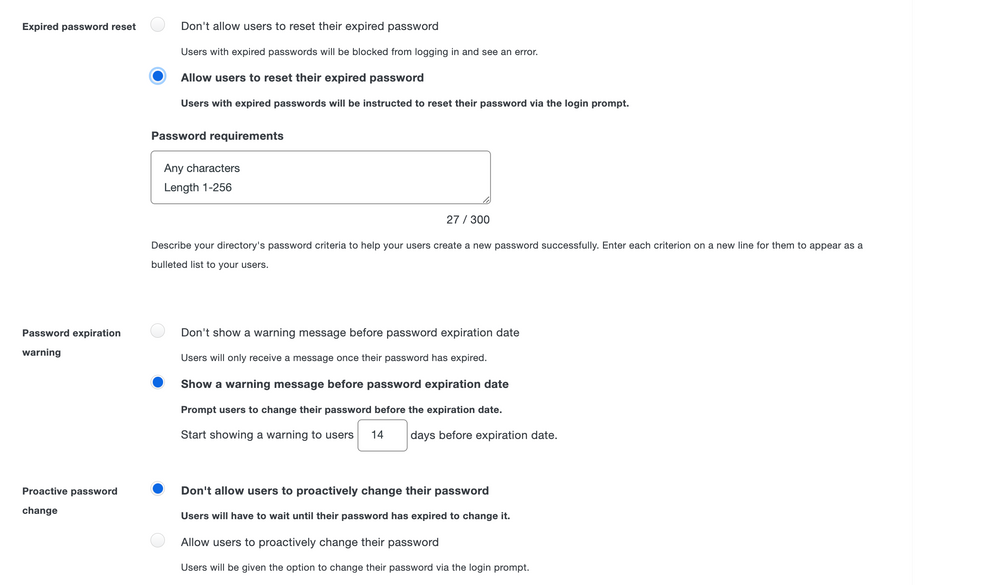
- Admins can now enable two new password settings in addition to Expired password reset:
- Expiring password warnings: Users will receive a notification during login and authentication when their password is expiring within a customizable number of days.
- Proactive password reset: Users can change their password from the login page at any time.
- Administrators can adjust these settings in Duo Admin Panel > Settings > Admin Password Policy.
Duo for Outlook Web App (OWA) version 2.0.0 released
- The installer now defaults to “fail closed” for new installations and upgrades from v1.x to v2.0.0. Upgrades from v2.0.0 to future releases will preserve the installed fail mode selection.
- TLS 1.2 is now the minimum supported version; drops support for TLS 1.1, 1.0, and SSLv3.
- Now supports WinHTTP proxy server configurations that use a bypass-list.
- Corrects an issue where ECP logout did not expire the Duo session cookie created after MFA success at login.
- Changes the Duo OWA registry key location to HKLM\Software\Duo Security\DuoOwa and the registry values IKey and SKey to Client_Id and Client_Secret.
Universal Prompt now available for OneLogin and Microsoft OWA
- To enable Universal Prompt for OneLogin:
- Navigate to Settings > Account Settings in OneLogin.
- Check the box for Enable Duo Universal Prompt (OIDC flow) under the Duo Universal Prompt setting on the Basic page.
- Select Save.
- Authenticate once with Duo after saving.
- To enable Universal Prompt for Microsoft OWA, upgrade to Duo OWA v2.0.0 and authenticate once with Duo after upgrading.
Duo Authentication Proxy version 5.8.1 released
- Fixed an issue where SSO logins that timed out would be incorrectly interpreted as bad credentials.
- Fixed an issue where the configuration check would no longer incorrectly report a problem with the transport value of an ad_client section if ssl_verify_hostname is not specified.
Duo Mobile for Android version 4.40.0 released
- Miscellaneous bug fixes and behind-the-scenes improvements.
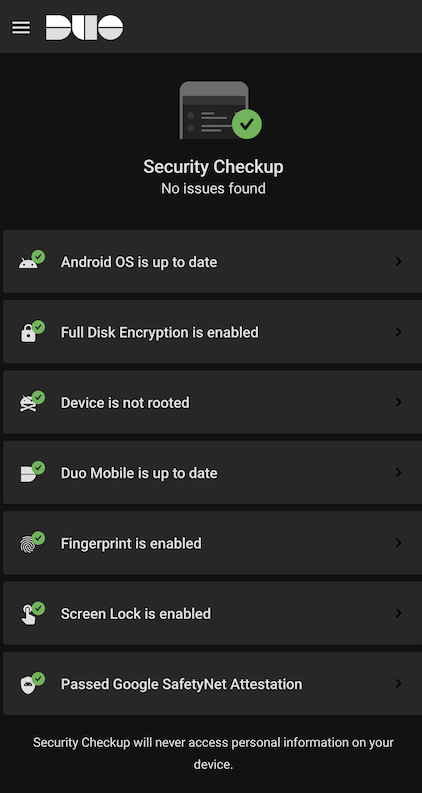
- Please note that Android devices will stop using SafetyNet for device attestation (pictured below) before June 2024, which will result in devices running Duo Mobile Android version 4.40.0 and below to stop receiving updates about tamper status.Versions of Duo Mobile for Android released after 4.40.0 will use Play Integrity attestation to update Duo tamper status. Keep your Duo Mobile for Android up to date with new versions to avoid disruption.
Duo Mobile for iOS version 4.40.0 released
- Pages selected from the left-hand navigation launch as popups; selecting the X on the page returns you to the main screen.
- Miscellaneous bug fixes and behind-the-scenes improvements.
Bug fixes
- When logging in to the Duo Admin Panel, selecting Use Passkey when locked out for ten invalid passcode authorization attempts no longer circumvents the lockout.
- Fixed a bug for the Citrix NetScaler named SAML application with Duo SSO that caused redirections to an error page or a failed login.
- Passcode factor error messages during authentication now specify what caused the error instead of showing the message “Unknown error.”
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: