- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Cisco SSL VPN + AD RADIUS authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco SSL VPN + AD RADIUS authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-20-2017 08:43 AM
Hi,
currently we are using MS RRAS VPN but we are going replace it to Cisco ASA 5510-X with Cisco AnyConnect. I would like to know whether I have right understood the authentication process. I have the following schema:
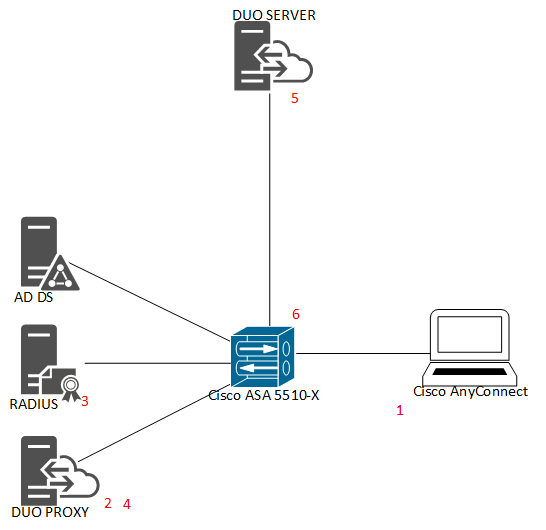
- VPN client connects to Cisco VPN
- Cisco VPN asks DUO Proxy for the authentication
- Duo Proxy asks MS RADIUS for the authentication
- RADIUS says to Dup Proxy “OK”
- DUO Proxy asks DUO server for the authentication and User approves it by DUO Mobile
- DOU Proxy answers Cisco VPN “OK” and Cisco VPN establishes VPN connection.
Is everything right?
- Labels:
-
VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2017 10:12 AM
Take a look at the networking diagram and accompanying description at the bottom of this page:
Your upstream RADIUS server (NPS or whatever) would be #3. Alternatively, you could point the Duo proxy straight at AD, so your domain controller would be #3.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2018 02:59 AM
Hello Kristina,
this is my configuration file of DUO Proxy:
[radius_client]
host=10.255.9.16
secret=******
[radius_server_auto]
ikey=XXXXXXXXXXXXXXXXXXX
skey=YYYYYYYYYYYYYYYYYYYYYYYYYYYYY
■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■■
radius_ip_1=10.254.1.200
radius_secret_1=******
failmode=safe
client=radius_client
pass_through_all=true
allow_concat=true
port=1812
[main]
debug=true
then I try to check VPN in Cisco, I get an error:
test aaa-server authentication Duo host 10.254.1.114 username vpn_asa password 1q2wazsxDCFV
2018-01-02T11:31:29+0100 [-] Duo Security Authentication Proxy 2.7.0 - Init Complete
2018-01-02T11:31:29+0100 [-] RadiusClient starting on 56935
2018-01-02T11:31:29+0100 [-] Starting protocol <duoauthproxy.lib.radius.client.RadiusClient instance at 0x02A5CC88>
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] Packet dump - received from 10.254.1.200:
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] '\x014\x00A\xff-\xa8\xbc\x95N\x85Q\xb5\xb2A\xe0\x81\x97i[\x01\tvpn_asa\x02\x12\xa77e\xfe\xf9\x113 \xdde\xf71tt\xcc\xde\x04\x06\n\xfe\x01\xc8\x
05\x06\x00\x00\x00\x17=\x06\x00\x00\x00\x05'
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] Sending request from 10.254.1.200 to radius_server_auto
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] Received new request id 52 from ('10.254.1.200', 20747)
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] (('10.254.1.200', 20747), 52): login attempt for username u'vpn_asa'
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] Sending request for user u'vpn_asa' to ('10.255.9.16', 1812) with id 212
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] Packet dump - sent to 10.255.9.16:
2018-01-02T11:31:40+0100 [DuoForwardServer (UDP)] '\x01\xd4\x00A\xa0;|\xd5\x83\x0fP\x8a-Y\xd7,\x0f$\xa5\x98\x01\tvpn_asa\x02\x12\xc3\xf4\xefM\x83\xc2OwT\xfbe\x8c\xfc\xb7\xad\x12\x04\x06\n\xfe\
x01r\x05\x06\x00\x00\x00\x17=\x06\x00\x00\x00\x05'
2018-01-02T11:31:40+0100 [RadiusClient (UDP)] Packet dump - received from 10.255.9.16:
2018-01-02T11:31:40+0100 [RadiusClient (UDP)] '\x02\xd4\x00fi\x9f\x1c3\xb3xI\xaa\xc6Z\x18O\xaf\xd7\xa2\xbf\x07\x06\x00\x00\x00\x01\x06\x06\x00\x00\x00\x02\x19.\x9e"\t\xc1\x00\x00\x017\x00\x01\
x02\x00\n\xff\t\x10\x00\x00\x00\x00\x1d*\x9f\xdfC\xc1`\x01\x01\xd3\t\xe9\x84\x96u\xad\x00\x00\x00\x00\x00\x00h\xcf\x1a\x0c\x00\x00\x017\x07\x06\x00\x00\x00\x02\x1a\x0c\x00\x00\x017\x08\x06\x00
\x00\x00\x04'
2018-01-02T11:31:40+0100 [RadiusClient (UDP)] Got response for id 212 from ('10.255.9.16', 1812); code 2
2018-01-02T11:31:40+0100 [RadiusClient (UDP)] http POST to https://XXX-XXXXXXX.duosecurity.com:443/rest/v1/preauth: user=vpn_asa
2018-01-02T11:31:40+0100 [duoauthproxy.lib.http._DuoHTTPClientFactory#info] Starting factory <_DuoHTTPClientFactory: https://XXX-XXXXXXX.duosecurity.com:443/rest/v1/preauth>
2018-01-02T11:31:41+0100 [HTTPPageGetter (TLSMemoryBIOProtocol),client] Duo preauth call failed
Traceback (most recent call last):
File "twisted\internet\defer.pyc", line 588, in _runCallbacks
File "twisted\internet\defer.pyc", line 1184, in gotResult
File "twisted\internet\defer.pyc", line 1126, in _inlineCallbacks
File "twisted\python\failure.pyc", line 389, in throwExceptionIntoGenerator
--- <exception caught here> ---
File "duoauthproxy\lib\radius\duo_server.pyc", line 141, in preauth
File "twisted\internet\defer.pyc", line 1126, in _inlineCallbacks
File "twisted\python\failure.pyc", line 389, in throwExceptionIntoGenerator
File "duoauthproxy\lib\duo_async.pyc", line 182, in preauth
File "twisted\internet\defer.pyc", line 1128, in _inlineCallbacks
File "duoauthproxy\lib\duo_async.pyc", line 145, in call
File "duoauthproxy\lib\duo_async.pyc", line 159, in _parse_response
duoauthproxy.lib.duo_async.DuoAPIFailClosedError: 40102: Invalid integration key in request credentials
2018-01-02T11:31:41+0100 [HTTPPageGetter (TLSMemoryBIOProtocol),client] (('10.254.1.200', 20747), 52): Denied Duo login on unexpected failure
2018-01-02T11:31:41+0100 [HTTPPageGetter (TLSMemoryBIOProtocol),client] (('10.254.1.200', 20747), 52): Returning response code 3: AccessReject
2018-01-02T11:31:41+0100 [HTTPPageGetter (TLSMemoryBIOProtocol),client] (('10.254.1.200', 20747), 52): Sending response
2018-01-02T11:31:41+0100 [HTTPPageGetter (TLSMemoryBIOProtocol),client] Packet dump - sent to 10.254.1.200:
2018-01-02T11:31:41+0100 [HTTPPageGetter (TLSMemoryBIOProtocol),client] '\x034\x00<:s\x97\xb9\xdd3\x1b\xe7C\x83\xfbkR\xef\x8c\xdd\x12(Denied Duo login on unexpected failure'
2018-01-02T11:31:41+0100 [duoauthproxy.lib.http._DuoHTTPClientFactory#info] Stopping factory <_DuoHTTPClientFactory: https://XXX-XXXXXXX.duosecurity.com:443/rest/v1/preauth>
How can i fix it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2018 04:28 AM
it is very strange. We have also DUO proxy for RRAS.
I have taken ikey and skey from this App - it works!
But why the ikey and skey for Cisco don’t work?
Acount ID: 0199-1825-13
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-02-2018 07:06 AM
Did you create the right kind of Cisco application (you want “Cisco RADIUS VPN” instead of “Cisco SSL VPN”)? Perhaps the Cisco application information was copied/pasted incorrectly?
I suggest you contact Duo support about this issue - it’s pretty much impossible to troubleshoot this error without your actual integration information (ikey and host) but we don’t want you sharing that info to the whole community.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide