- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Can Shibboleth Service Provider integrate with Duo SSO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can Shibboleth Service Provider integrate with Duo SSO
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-18-2022 11:25 PM
I am reaching out for help integrating Duo SSO with Shibboleth Service Provider. Attempting to get user principal name attribute value as persistent-id has been unsuccessful. The attribute value received is a long sting of numbers and letters. Value expected example BSMITH.
Service provider mapping: Attribute name=“urn:oasis:names:tc:SAML:2.0:nameid-format:persistent” id=“persistent-id”; “NameIDAttributeDecoder” formatter="$NameQualifier!$SPNameQualifier!$Name"
Please advise how to get persistent-id working or perhaps an alternate solution to get UPN attribute value.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 05:52 AM
Hi @PortlandGirl,
A NameIDFormat of urn:oasis:names:tc:SAML:2.0:nameid-format:persistent is special and acts differently than most NameIDFormats per the SAML specification which states that when persistent is picked the identity provider (in this case Duo SSO) must create a consistent opaque value will always be returned the same for a specific user but is not any identifiable data.
If that is not what you’re trying to do I’d recommend seeing if you can adjust Shibboleth to use a different NameIDFormat.
Here is the text from the SAML spec:
8.3.7 Persistent Identifier
URI: urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
Indicates that the content of the element is a persistent opaque identifier for a principal that is specific to
an identity provider and a service provider or affiliation of service providers. Persistent name identifiers
generated by identity providers MUST be constructed using pseudo-random values that have no
discernible correspondence with the subject’s actual identifier (for example, username). The intent is to
create a non-public, pair-wise pseudonym to prevent the discovery of the subject’s identity or activities.
Persistent name identifier values MUST NOT exceed a length of 256 characters.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 08:10 AM
Thank you for the information Jamie. I have a follow-up question. The IdP attribute is Username. Is there a way to get eppn urn:oid:1.3.6.1.4.1.5923.1.1.1.6 SAML response attribute from Duo SSO?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 11:24 AM
I’m not sure if we are still talking about the NameID value. The only NameIDFormats we allow are in the dropdown on the page.
If you’re instead trying to send an attribute with the name of urn:oid:1.3.6.1.4.1.5923.1.1.1.6 and the value of Username I’d recommend using the Mapped Attributes section where you can put in an IdP attribute on the left and any name on the right that you’d like the attribute name to be in the SAMLResponse.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2022 02:51 PM
I’m trying to get the user principal name value (e.g. DBROWN) in a way that Shibboleth Service Provider can use it. Eppn is commonly used by universities. If DUO SSO can send oid:1.3.6.1.4.1.5923.1.1.1.6 then authenticator can use the part before the ‘@’ which would effectively be DBROWN, and allow for successful authentication.
Client tried using the “Map attributes” section with preconfigured “Username” IdP attribute. Perhaps it was missed. Is eppn available as a SAML Response Attribute?
I appreciate your continued help. I’ve worked with multiple IdPs but first time with Duo SSO and am really having a tough time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2022 09:28 AM
If the attribute just needs to be named oid:1.3.6.1.4.1.5923.1.1.1.6 in the SAMLResponse from Duo SSO you can do something like this:
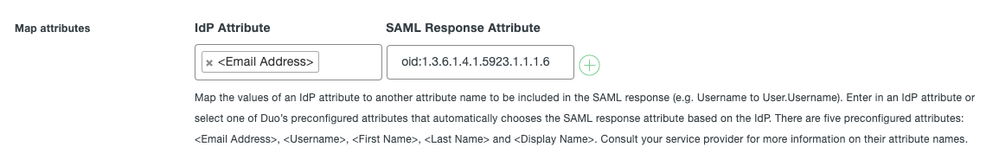
<Email Address> is the bridge attribute value that will send the mail attribute from Active Directory or the Email attribute from a SAML IdP. You can find the list here of the mappings: Duo Single Sign-On | Duo Security
You can also replace that value with a different value if you don’t want to use the bridge attribute and want to send something else down from the upstream SAML IdP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2022 10:02 AM
Thanks for the additional information. I’ll have the institution give that a try!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2022 12:11 PM
Is the map attributes suggestion performing a transform? UserPrincipalName is the unique identifier value we are seeking, or the part before the @. Email address is subject to change. Want to get a clarification about the bridging. If is simply being sent as a random description, that’s not going to be a workable solution.
When neither email address, username, firstName, lastName nor display are suitable attributes, are custom alternatives available? This is why I am asking about the transform.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2022 01:40 PM
There is no way to currently transform attributes with Duo SSO but if there is an attribute already inside of your upstream identity provider that has the value you want, you can type that in under the “IdP Attribute” section instead of using the dropdown.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide