- Cisco Community
- Technology and Support
- Security
- Duo Security
- Protecting Applications
- Active Directory Attributes for SAML with Duo SSO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2022 09:18 AM
We are migrating our Duo Access Gateway (DAG) environment over to using Duo SSO with the Duo Authentication Proxy. We’ve gotten almost everything working. When I went to migrate one of our SPs today, though, I realized that the attributes stored in Active Directory are not being passed as SAML attributes.
This is what we have on our Duo Access Gateway configurations.
$ cat duo_openldap.json
{
“duo_openldap”: {
“0”: “ldap:LDAP”,
“port”: 389,
“enable_tls”: true,
“hostname”: “ldap://ldap.example.com”,
“attributes”: [
“uid”,
“sn”,
“givenName”,
“cn”,
“e■■■■■■■■■■■■■■■■■■■■iation”,
“eduPersonAffiliation”,
“e■■■■■■■■■■■■■■■■■■■■e”,
“mail”,
“infobloxAdminGroup”
],
“search.enable”: true,
“search.base”: [
“dc=example,dc=com”
],
“search.attributes”: [
“uid”
],
“search.username”: “uid=readonly,dc=example,dc=com”,
“search.password”: “REDACTED”,
“referrals”: false
}
}
However, I cannot find a similar configuration for our Duo Authentication Proxy in the authproxy.cfg file.
What is the proper way to signify which directory attributes should be sent via SAML?
Thanks,
Brian
Solved! Go to Solution.
- Labels:
-
Authentication Proxy
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2022 03:23 PM
Hi @bepstein,
You should be able to accomplish this by typing the name of the IdP attribute you’d like into both fields. On the “IdP Attribute” field you may need to hit your Enter key so it uses what you’ve typed instead of the drop-down selection.
Below is an example of what that might look like:
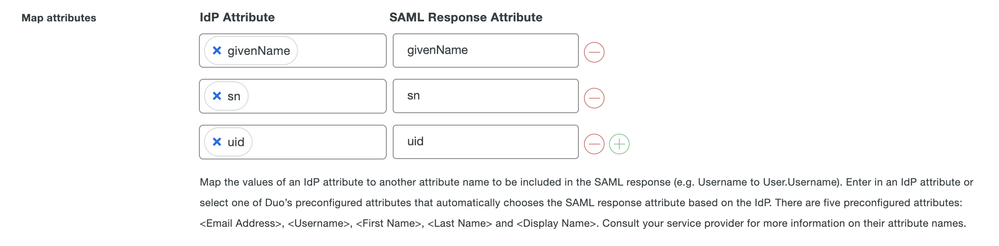
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2022 09:18 AM
Glad you’re making the move from DAG to Duo SSO!
You define additional AD attributes to send in the SAML response in the service provider application, as mapped attributes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2022 09:43 AM
Thank you @DuoKristina . So, if the AD Attribute has the same name as I would like to send to the SP, do I just map the name to itself?
Thanks,
Brian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2022 09:49 AM
Actually, I just started playing around with it. Here’s what I’m trying to do.
I have an LDAP attribute “infobloxAdminGroup” in Active Directory. In Duo Access Gateway, I could specify this attribute in the duo_openldap.json file to be sent.
However, with a Duo SSO protected application, when I go into mapped attributes, it presents me with a dropdown list to choose from.
<Username>
<Email Address>
<First Name>
<Last Name>
<Display Name>
None of these are the attribute I want to pass on to the SP, though. I know I can create an attribute, but that’s not going to work either as each user may have a different value for the attribute.
I see that there is a Role attributes section, but this seems like I would need to somehow import the data from my Active Directory into Duo Groups to utilize it.
Is there a way to use Duo SSO to just pull the LDAP attributes from Active Directory that I would like and pass them onto the SP like Duo Access Gateway does?
Here’s what the documentation says:
https://duo.com/docs/sso-generic#configure-single-sign-on
When configuring an application to be protected with Duo Single Sign-On you'll need to send attributes from Duo Single Sign-On to the application. Active Directory will work with no additional setup, but if you used a SAML idenity provider as your authentication source please verify that you configured it to send the correct SAML attributes.
Below you can see the Bridge Attribute name used that automatically maps certain attributes from your authentication source.
Bridge Attribute Active Directory SAML IdP
<Username> sAMAccountName Username
<Email Address> mail Email
<Display Name> displayName DisplayName
<First Name> givenName FirstName
<Last Name> sn LastName
Can I create my own Bridge attributes somewhere?
Thanks,
Brian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2022 03:23 PM
Hi @bepstein,
You should be able to accomplish this by typing the name of the IdP attribute you’d like into both fields. On the “IdP Attribute” field you may need to hit your Enter key so it uses what you’ve typed instead of the drop-down selection.
Below is an example of what that might look like:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2022 06:48 PM
Hi @jamie ,
Thank you so much! This did work for me and really saved the day. I wish the interface was a little more intuitive on needing to press Enter after typing in the attribute. Now that I know that, it is working great.
Thanks again!
Brian
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: